Heartbleed is a vulnerability with a CVSS score of only 5.0/10. As of this morning we have observed 840 breaches related to the Heartbleed vulnerability, CVE-2014-0160. More than enough has been said about the technical details of the vulnerability; hence I’d like to use this post to discuss the vulnerability management implications of Heartbleed, because they are both alarming and telling.
To make this clearer, Common Vulnerability Scoring System (CVSS) ranks CVE-2014-0160 with a CVSS score of only 5.0/10.0. A good observer will note that the National Vulnerability Database is not all that comfortable with ranking the vulnerability that broke the Internet as a 5.0/10.0. In fact, unlike any other vulnerability in the system we have seen, there is an “addendum” in red text http://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2014-0160:
“CVSS V2 scoring evaluates the impact of the vulnerability on the host where the vulnerability is located. When evaluating the impact of this vulnerability to your organization, take into account the nature of the data that is being protected and act according to your organization’s risk acceptance. While CVE-2014-0160 does not allow unrestricted access to memory on the targeted host, a successful exploit does leak information from memory locations which have the potential to contain particularly sensitive information, e.g., cryptographic keys and passwords. Theft of this information could enable other attacks on the information system, the impact of which would depend on the sensitivity of the data and functions of that system.”
So what does this mean for your organization? How should you prioritize the remediation of Heartbleed versus other vulnerabilities? NVD’s answer is “think about what can be stolen.” The problem here is that the CVSS temporal metric, which is used to account for the vulnerability in the wild, can only reduce the CVSS score. So we’re still stuck at a 5. Why?
CVSS scoring is failing to take into account quite a few factors:
1. It’s a target of opportunity for attackers:
The amount of sites affected by the vulnerability is unfathomable – with broad estimates between 30-70% of the Internet.
2. It’s being actively and successfully exploited on the Internet:
We are logging about 20 breaches every few hours. The rate of incoming breaches is also increasing. On April 10th, we were seeing 1-2 breaches an hour. Keep in mind this is just from the 30,000+ businesses that AlienVault Open Threat Exchange (OTX) monitors - not 70% of the Internet. For those unfamiliar with OTX, I'm referring to AlienVault Open Threat Exchange (OTX™) which is an open threat information sharing and analysis network, created to put effective security measures within the reach of all organizations. OTX provides real-time, actionable information to all who want to participate.
In addtion, to clarify, we define “breaches” as successful exploits - that is, indicators of compromise of a vulnerability were found or an exploit was detected at the same time as a vulnerability was open on an asset. It is possible they are 0 impact breaches, but they help us understand likelihood regardless.
3. It’s easy to exploit:
There exists a Metasploit module and exploit code on ExploitDB.
In fact, there is proof of this happening. Below is a time series of the volume of breaches for Heartbleed for the past month. This pattern shows a steady increase in breaches from the release date, ending with around 20-30 breaches being tracked per hour.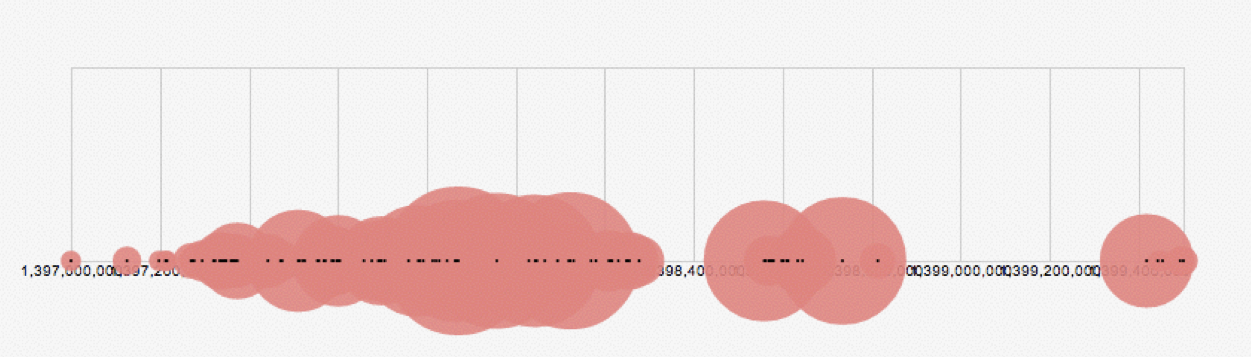
We already knew Heartbleed was a big deal – this data isn’t changing anyone’s mind. The interesting bit is that Heartbleed is not the only vulnerability to follow such a pattern. Of all the breached vulnerabilities in our database, Heartbleed is the fifth most breached (that is, most instances recorded) with a CVSS score of 5 or less. Attached are a few other breach volume patterns so that you can get a feel what successful attacks look like. These are of different scales, so the smallest circles represent small volume attacks, increasing from there. I show two different attack patterns, one for a terminal denial of service, one for an RCE.
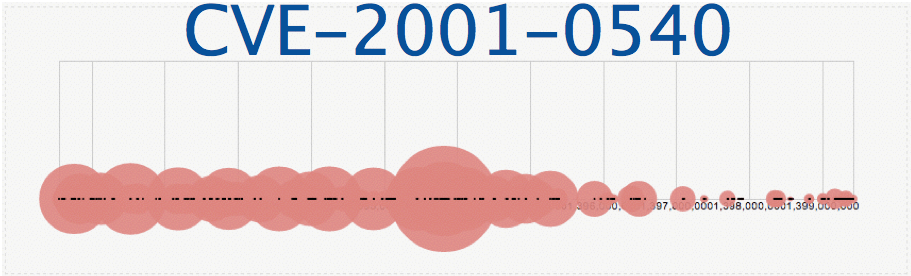
1. CVE-2001-0540 - Score: 5.0. Memory leak in Terminal servers in Windows NT and Windows 2000 allows remote attackers to cause a denial of service (memory exhaustion) via a large number of malformed Remote Desktop Protocol (RDP) requests to port 3389.
2. CVE-2012-0152 - Score: 4.3, Terminal Server Denial of Service Vulnerability
3. CVE-2006-0003 – Score: 5.1, Allowing remote attackers to execute arbitrary code via unknown attack vectors.
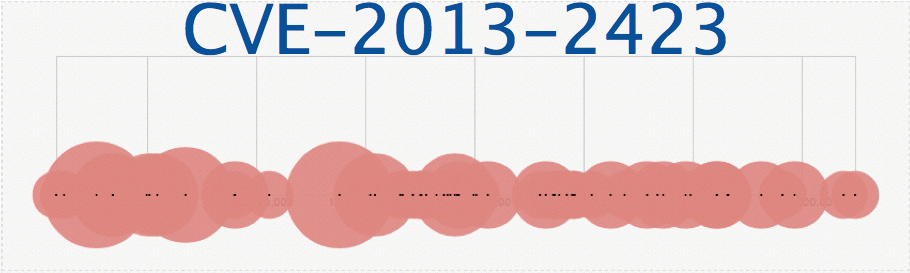
4. CVE-2013-2423 - Score: 4.3. Vulnerability in the Java Runtime Environment (JRE) component in Oracle Java SE 7 Update 17 and earlier, and OpenJDK 7, allows remote attackers to affect integrity via unknown vectors related to HotSpot
Two of these are terminal denial of service, and two of these are remote code executions. The common thread is that all of these have a network access vector and require no authentication, all of these have exploits available, affect a large number of systems and are currently being breached. You can tell from just seeing the velocity of attacks over time that these are the real persistent threats - vulnerabilities which have many and vast exploitation campaigns, and closing the door on these (not CVSS 10 which is unexploited, not something the media highlights) is what reduces risk the most in your environment.
However, what’s missing from this analysis is how to compare a few vulnerabilities which you know are being actively exploited. Next, we graph all 5 of the aforementioned vulnerabilities over time (from the beginning of the year) and scale them so that you can compare the volume and velocity of breaches. It is easy to see that Heartbleed represents only a small portion of the breach landscape, and CVE-2001-0540 is a much more significant exploitation campaign.
Does this mean that you should not patch Heartbleed? Of course not. It means that when assessing risk to your environment, the first step to take is to consider the probability of a successful attack happening on that intrusion point. And from here, without any consideration for the specific environments in which these vulnerabilities exist, it looks like CVE-2001-0540 is the bigger risk.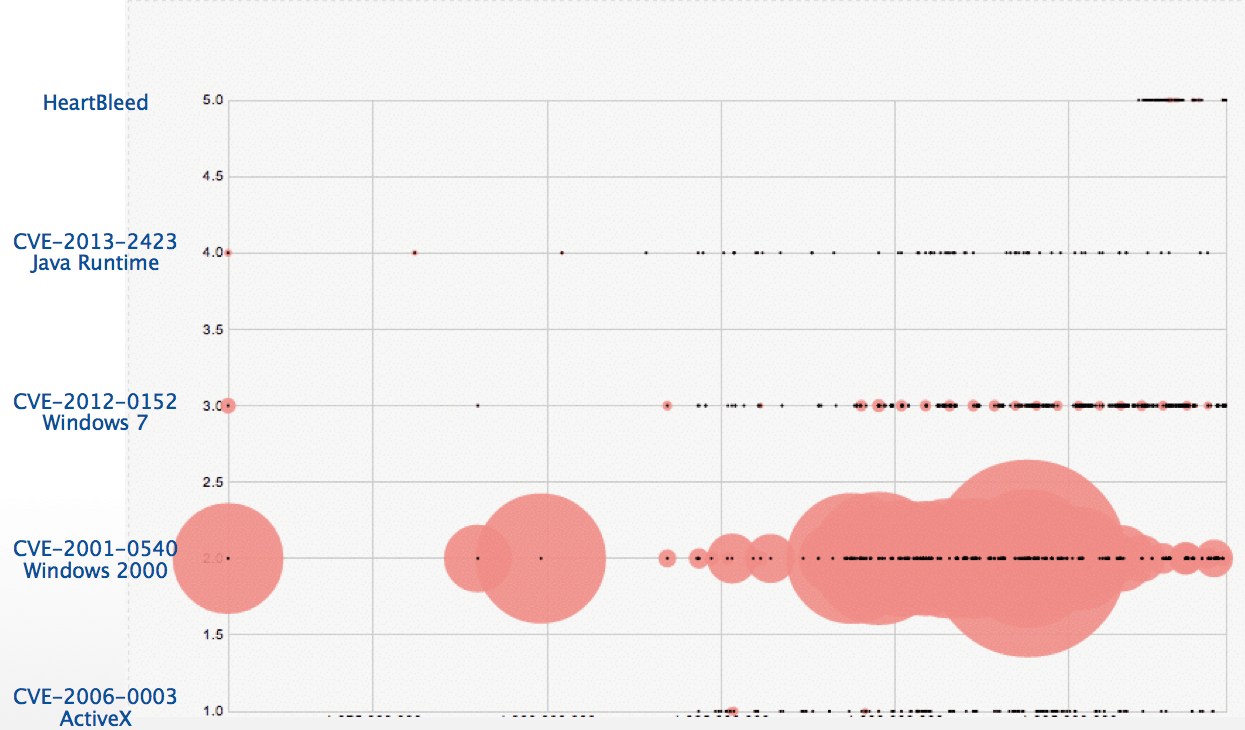
Heartbleed IS a big deal. But it’s not the only one – there are plenty of vulnerabilities which have received less press and are buried deep within the PCI requirements or CVSS-based prioritization strategies which are causing breaches, today. It’s important to check threat intelligence feeds for what’s being actively exploited, to think like an attacker and to have the same information an attacker has. It’s also important to learn a lesson from this past week: while the press took care of this one, it won’t take care of a remote code execution on a specific version of windows that your organization happens to be running. Just don’t say it’s not a big deal when a breach occurs on a CVSS 4.3. You have been warned.

Michael Roytman is responsible for building out Risk I/O’s predictive analytics functionality, and has been selected to speak at some of the top information security events on this topic, including BSides, Metricon and SIRACon. He formerly worked in fraud detection in the finance industry, and holds an MS in Operations Research from Georgia Tech. His home in Chicago contains a small fleet of broken-down drones.
Related Topics:
- Webinar Slides from Risk I/O
- AlienVault blog
- AlienVault Open Threat Exchange (OTX)

