Today, a coordinated coalition involving AlienVault and several other security companies led by Novetta is announcing Operation BlockBuster. This industry initiative was created to share information and potentially disrupt the infrastructure and tools from an actor named the Lazarus Group. The Lazarus Group has been responsible for several operations since at least 2009, including the attack that affected Sony Pictures Entertainment in 2014.
Part of our research on this actor was presented at the Kaspersky Security Analyst Summit (SAS) in Tenerife, Spain on February 9th, 2016 as a joint talk between AlienVault and Kaspersky’s Global Research and Analysis Team.
In the research that AlienVault and Kaspersky collaborated on, we attributed several campaigns to this actor. Armed with some of the indicators that US-CERT made public after the Sony attack, we continued to analyze different campaigns in 2015 that we suspected were being launched by the same actor. Eventually we were also able to attribute previous activity to the same attackers including:
- Sony Pictures Entertainment - 2014
- Operation DarkSeoul - 2013
- Operation Troy - 2013
- Wild Positron / Duuzer - 2015
Besides several campaigns were the Lazarus group has utilized wipers to perform destructive attacks, they have also been busy using the same tools to perform data theft and cyber espionage operations.
Today, as part of the Operation BlockBuster release, we want to share some of our findings and TTP’s from the Lazarus Group that allowed us to link and attribute all the campaigns and tools into the same cluster of activity. We highly recommend that you read the comprehensive report Novetta published today http://operationblockbuster.com [no longer available] that includes details on the project’s scope and the more than 45 malware families identified, and includes signatures and guidance to help organizations detect and stop the group’s actions.
Encryption/Shared keys
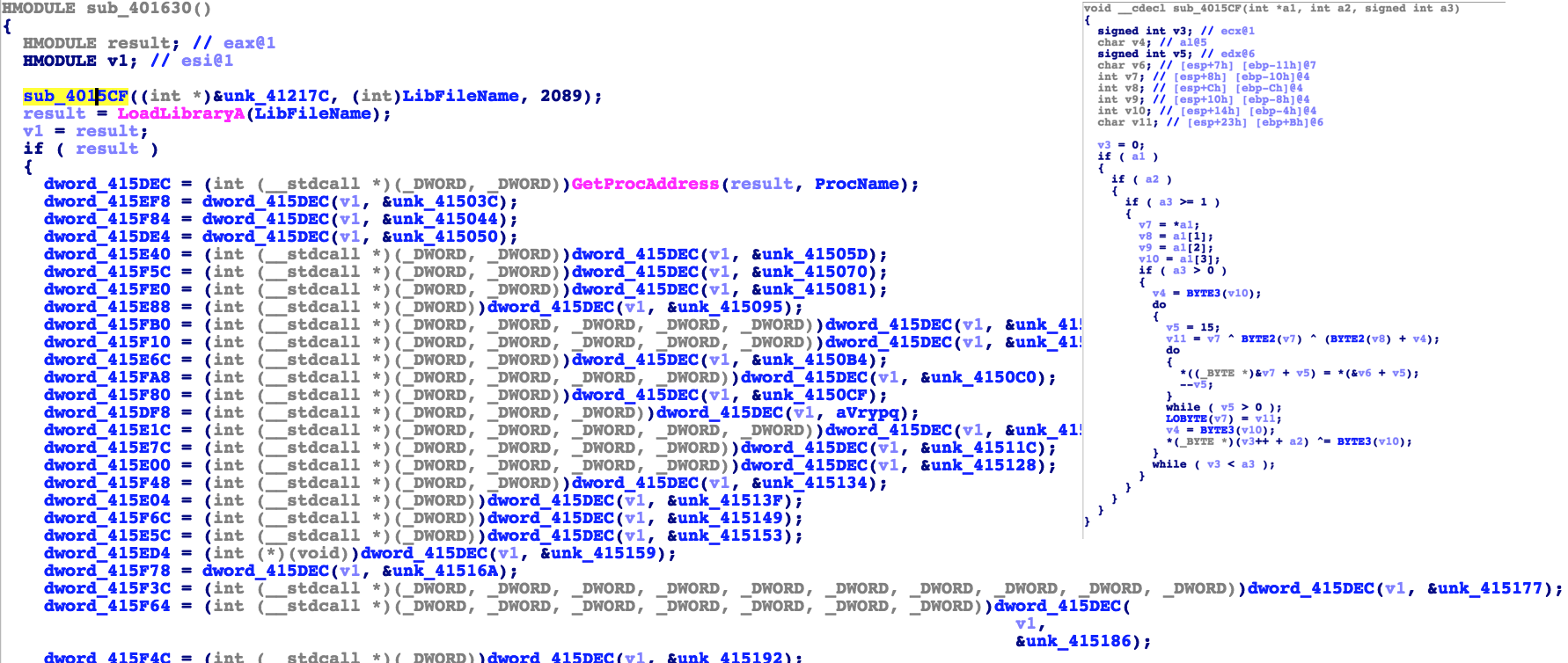
One of the key findings that gave us the opportunity to link several families to the same actors was finding a dropper that the attackers use. This dropper contains a compressed resource (ZIP) with the name “MYRES” that is protected by a password. The attackers have reused the same password in different occasions and we were able to find droppers containing different families used by the group.
This actor also reuses the code libraries they utilize to perform RSA encryption. We were also able to find the exact same public key in multiple variants.
Batch scripts
This actor often uses BAT files that share the same skeleton in order to delete the initial files after infection.
We have seem them reuse this technique across multiple droppers and payloads.
Obfuscation functions
The Lazarus Group uses a few different methods to obfuscate API functions and dynamically load them. One of them consist on using a simple XOR schema.
You can find other examples of API function obfuscation in the Novetta http://operationblockbuster.com [no loner available] report.
Network communications
This actor has different malware families in their toolset that implement a similar C&C protocol. The protocol looks like TLS but it is in fact a “fake” TLS protocol that mimics it.
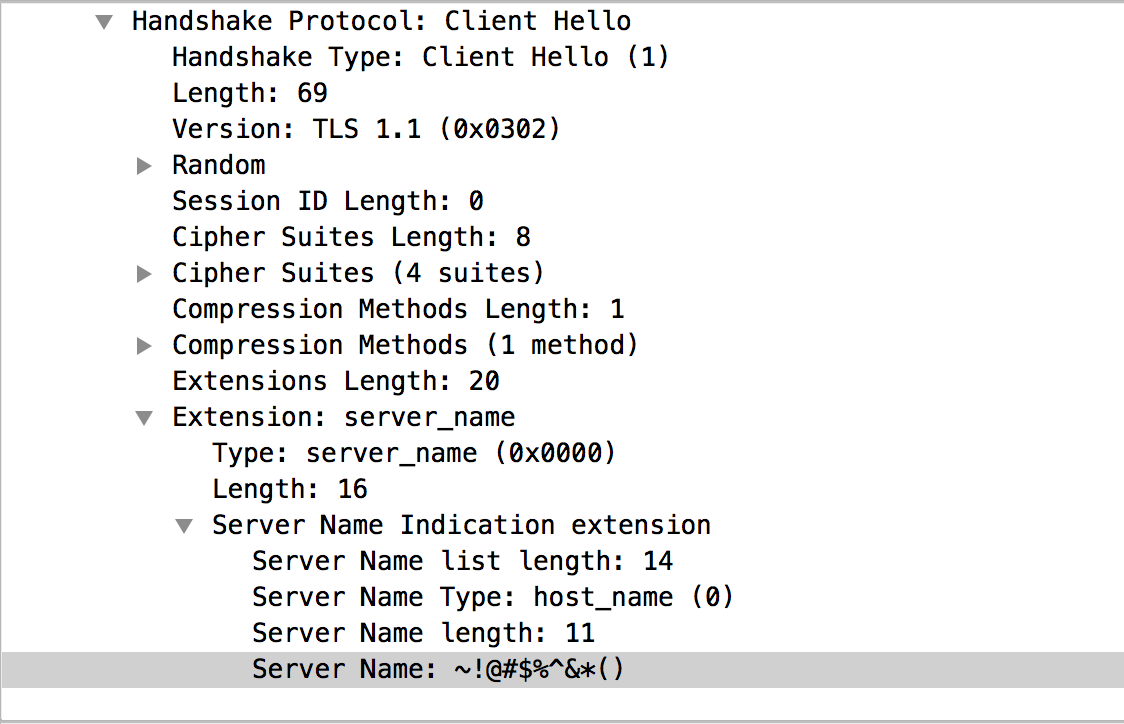
One of the characteristics we have identified is how they choose the values for certain fields when generating “TLS” packets, especially the ClientHello packet.
We have identified different families exhibiting slightly different behaviors:
- Using a static “Server Name” extension in the client_hello packet: “~!@#$%^&*()”
- Choosing between “www.amazon.com” and “www.google.com” for the “Server Name” value.
-
Randomly choosing one of the following items for the “Server Name” value (this list can vary across different samples):
|
wwwimages2.adobe.com www.paypalobjects.com www.paypal.com www.linkedin.com www.apple.com www.amazon.com www.adobetag.com windowslive.tt.omtrdc.net verify.adobe.com us.bc.yahoo.com urs.microsoft.com supportprofile.apple.com support.oracle.com support.msn.com startpage.com sstats.adobe.com ssl.gstatic.com ssl.google-analytics.com srv.main.ebayrtm.com skydrive.live.com signin.ebay.com securemetrics.apple.com secureir.ebaystatic.com secure.skypeassets.com secure.skype.com secure.shared.live.com secure.logmein.com sc.imp.live.com sb.scorecardresearch.com s1-s.licdn.com s.imp.microsoft.com pixel.quantserve.com p.sfx.ms mpsnare.iesnare.com login.yahoo.com login.skype.com login.postini.com login.live.com l.betrad.com images-na.ssl-images-amazon.com fls-na.amazon.com extended-validation-ssl.verisign.com daw.apple.com csc.beap.bc.yahoo.com by.essl.optimost.com b.stats.ebay.com apps.skypeassets.com api.demandbase.com ad.naver.com accounts.google.com |
On the other hand, most of the samples we have analyzed communicate with IP addresses that are part of compromised infrastructure. Since the attackers don’t leverage domain names for C2 it makes it hard to pivot using whois data, and passive DNS. In addition, there is no way to sinkhole since there is no domain infrastructure.
Another example is the use of user-agent values that contain the misspelled “Mozillar” string.
Hangul HWP Document Exploits
Hangul is an office suite and word processing application mainly used in South Korea, especially in the government.
We have observed this actor launching spearphishing campaigns with malicious HWP documents as attachments.
An example is a campaign that was launched on September 2015 that used a zeroday vulnerability (CVE-2015-6585) in the Hangul Word processor which was reported by FireEye.
Based on obtained samples and decoy documents we observed that they were likely targeting a wide range of victims including government, industrial and political entities.
Sample decoy documents
Fake installers
It appears another vector the Lazarus Group uses to infect victims is distributing backdoored software. We have found a few samples using this technique but it is not quite clear to us how they were distributing the files.
An example is a backdoored version of a Remote Desktop Client:
Indicators of Compromise
As part of Operation BlockBuster, Novetta is sharing Yara rules and IOC’s that you can find at the following website:
Operation BlockBuster http://www.operationblockbuster.com/resources/index.html [no longer available]
In addition to that we are making the indicators of compromise available in our Open Threat Exchange: