By Fernando Martinez and Javier Ruiz of AT&T Alien Labs.
In our previous blog, we analyzed how it is possible to map malware threats using the MITRE ATT&CK™ framework. In this blog, we will test the USM Anywhere platform against red team techniques and adversary simulations. We performed this analysis as part of our continuous efforts to improve the platform’s detection effectiveness.
There are numerous frameworks that can help you simulate the actions that a red team would perform in a post-compromise situation - as well as techniques associated with particular APT groups. These frameworks allow you to simulate malicious activities at an enterprise level, without actually infecting any systems. They just generate enough activity to validate defensive telemetry and test incident response plans and playbooks.
When running scenarios, we will cover a wide variety of techniques using the new MITRE ATT&CK™ matrix implemented in USM Anywhere. We will then show how users can have complete visibility of the entire kill chain from Initial Access to Exfiltration.
First, we’ll see how some of these automated simulation tools work and how we can easily recognize tactics using the matrix visualization in USM Anywhere.
APTSimulator
APTSimulator is a set of Windows batch tests created by Florian Roth (Nextron Systems) to perform simulated attacks against security tools, identify potential gaps, or test a scenario where a system has been compromised in the organization.
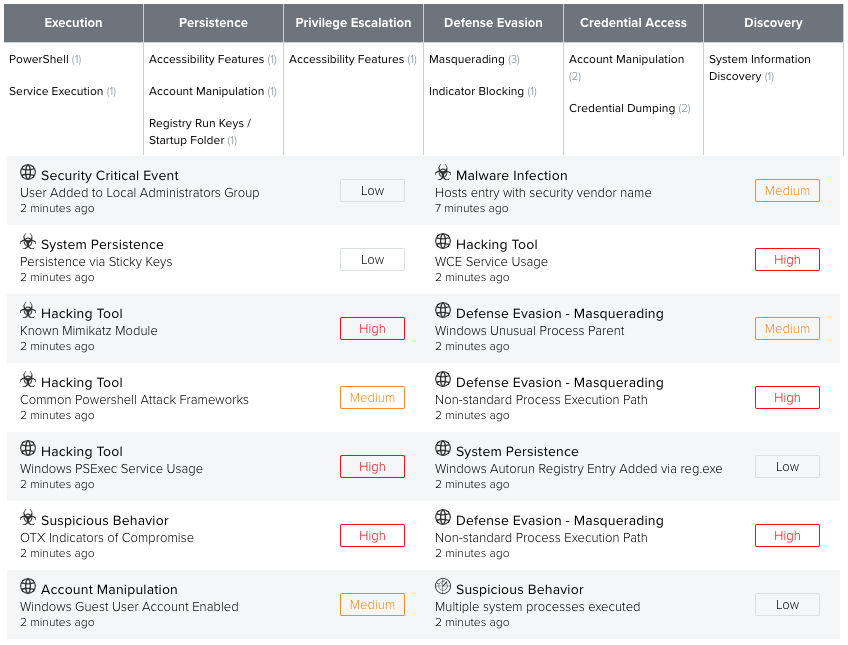
After running all the tests in the lab system at once, we can see how USM Anywhere performed detecting an amount of High severity alarms.
Endgame RTA
Red Team Automation is a set of scripts and modules that Endgame put together, in an open source tool, to be able to simulate adversaries' attacks to Windows systems and map them to the ATT&CK framework.
When deployed in March 2018, it had coverage for almost 50 ATT&CK techniques, including 7 out of 11 tactics: Execution, Persistence, Privilege Escalation, Defense Evasion, Credential Access, Discovery, Lateral Movement, Command and Control.
The execution of all the Endgame RTA test in a same system all together, produces the below results on the Mitre ATT&CK framework.
MITRE ATT&CK Tactics
We will be testing the previously mentioned frameworks, separating them by the MITRE ATT&CK Tactics that they leverage in each situation:
- Initial Access
- Execution
- Persistence
- Privilege Escalation
- Defense Evasion
- Credential Access
- Discovery
- Lateral Movement
- Collection
- Exfiltration
- Command and Control
Initial Access
This tactic represents the vectors adversaries use to gain an initial foothold within a network. Since the adversary simulation frameworks provide tests to perform from inside the network, and initial access is the tactic that covers the transition from outside to inside the network, this tactic is usually left uncovered.
However, we ran a custom test to simulate the successful execution of an exploit against public applications, which is a common technique used to gain access to a company network.
Execution involves any code generated by the attacker that is executed inside the enterprise network, either if it is a line of malicious code or a full Trojan. It is the first step taken after initial access - finding out how / where to execute code to allow the attacker to move up in the kill chain.
As an example for this tactic, we used the execution_win_regsvr32.yml script in the Metta framework. This script uses technique T1117 to leverage Regsvr32, which can be used to execute arbitrary binaries. After execution of the script, USM Anywhere detects:
USM Anywhere detects this activity as a combination of the Execution tactic and Defense Evasion as expected for technique T1117, since it is sometimes whitelisted by the security team due to the false positives that it can generate.
From the other simulators, we could choose similar scripts to achieve an Execution tactic detection:
- Schtask_escalation.py for Endgame RTA, which creates and deletes a scheduled task in the system.
- PsExec from the APTSimulator, which dumps a renamed version of PsExec to the working directory, running it to start a command line in LOCAL_SYSTEM context.
Persistence
This tactic involves any change performed on a system that allows an attacker to continue their activities even if the victim performs a reboot or deletes some of the malware associated files.
As an example for this tactic, we used the APTSimulator framework. The script run-key.bat creates a malicious new run key entry to dump the output of the command “net user” to a file, using technique T1060.
From the other simulators, we could choose similar scripts to achieve a Persistence tactic detection. For example, in APTSimulator the sticky-key-backdoor.bat from script uses technique T1015 with a method commonly known as sticky keys attack.
Privilege Escalation
Privilege escalation attempts to obtain higher level of permissions in the infected system than the current one. The endgame of this tactic is to achieve Administrator or root privileges in the system.
As an example for this tactic, we used the Endgame RTA framework. The script uac_eventviewer.py modifies the Registry value to change the handler for MSC files, bypassing UAC, using technique T1088.
This tactic can also be generated through the APTSimulator with the sticky-key-backdoor.bat as seen in the previous tactic.
Defense Evasion
This tactic applies to any action taken to avoid detection from the victim, disable security systems or slow down any potential incident response to the incident, including: disabling security tools, clearing up logs, masquerading, etc.
We’ve already seen this tactic been used to achieve previous tactics, like Endgame RTA did in the previous section.
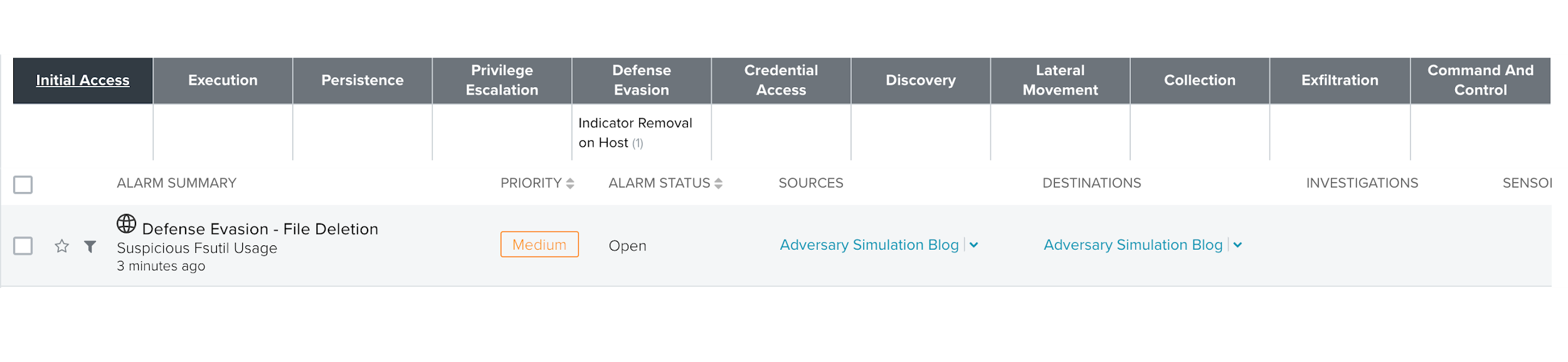
As an example for this tactic, in particular the log deletion example, we used the Endgame RTA framework. The script delete_usnjrnl.py uses fsutil to delete the USN journal, eliminating a log with great forensic value, using a combination of techniques T1070 and T1107.
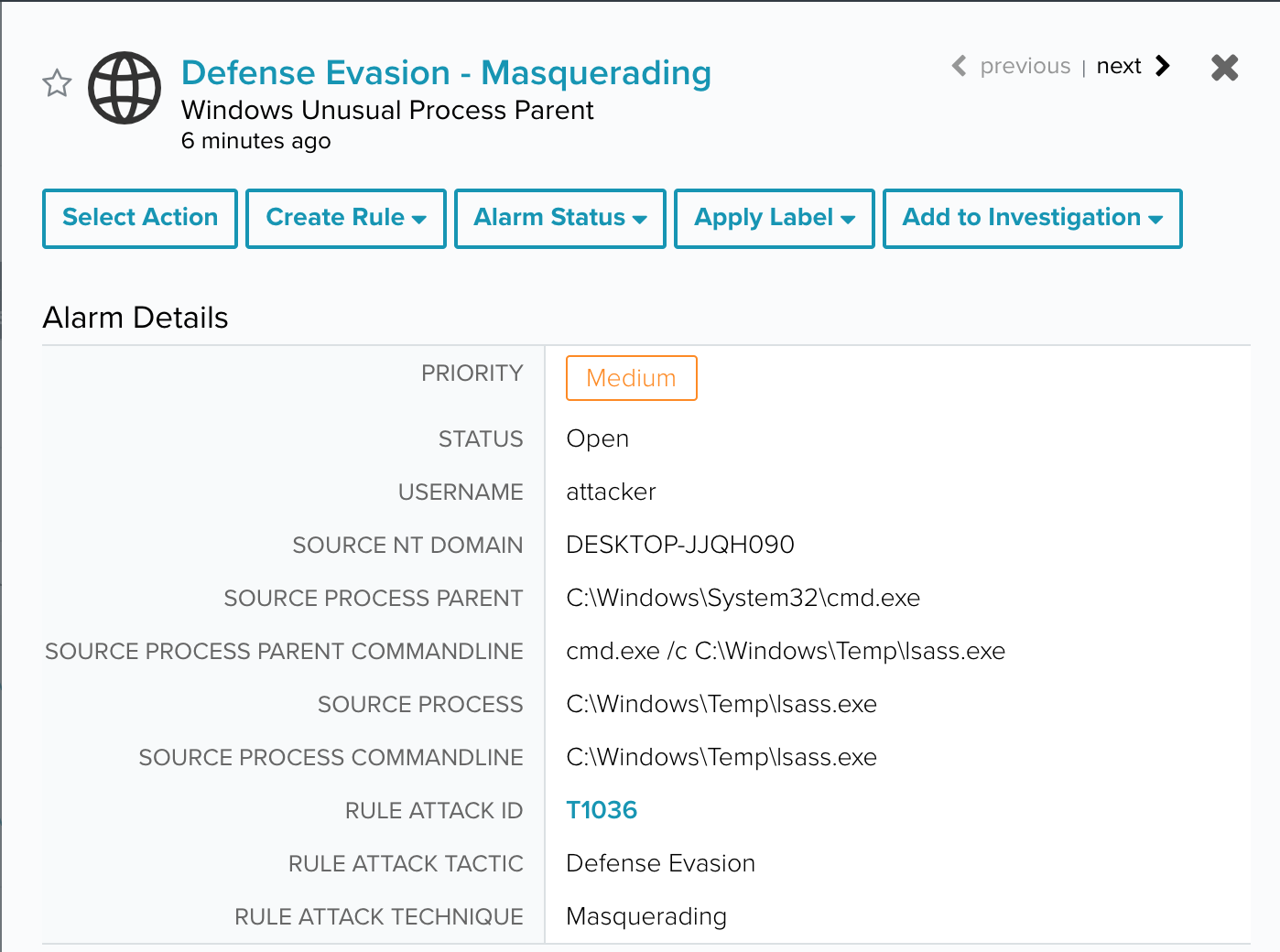
As this tactic is quite varied in application, we also wanted to include an example for masquerading. Through the Atomic Red Team framework, using the test Masquerading as Windows LSASS process. This test attempts to run a cmd making it look as a legitimate lsass process with technique T1036.
In this particular case, the test’s associated commands raise two different alarms due to abnormality of the activity.
Credential Access
Credential access tactic involves the acquisition of usernames and passwords (or their associated hashes) from one machine, the domain or the enterprise. This tactic allows the attackers to masquerade behind somebody’s name to avoid detection and perform Lateral Movement or Privilege Escalation with the newly collected credentials.
As an example for this tactic, we used the Endgame RTA framework. The script registry_hive_export.py exports a copy of the Registry hives: SAM, SECURITY and SYSTEM for later cracking. This technique is known as Credential Dumping (T1003).
Additionally, we’ll be looking at another example of a well-known password retriever tool, Mimikatz, which we can find in the APTSimulator framework (as well as the Atomic Red Team and Metta). The script mimikatz-1.bat executes Mimikatz and retrieves the credentials in the system, through the technique Credential Dumping T1003.
Discovery
This tactic consists of the attacker gaining access to the system it is in as well as the network, to be able to decide where he wants to move to (horizontally and vertically) to achieve their objective.
As an example for this tactic, we used the APTSimulator framework. The script recon-cmd-activity.bat runs several discovery commands to gain knowledge of the environment. This technique is known as System Information Discovery, T1082.
In this case, the execution of these commands by themselves do not create any alarms since they could be used by system administrators or benign users. However, the execution of several recon commands (whoami, systeminfo and net) in a short period of time, does raise an alarm in USM Anywhere as seen below.
Lateral Movement
This tactic involves any attacker’s activity that involves horizontal movement in the network, either in getting access to other systems or executing code in other systems.
As an example for this tactic, we used the Endgame RTA framework. We did this using script lateral_commands.py, which performs several WMI commands usually used by attackers to laterally move to other systems. This script combines several techniques that will be executed if the neighbor system meets several conditions: T1021, T1047, T1077, T1124, T1126.
Collection
Collection tactic consist of gathering and preparing for exfiltration of files that the attacker could find relevant, either if they already exist or are associated with audio/video captures taken from the victim’s computers.
From the previously mentioned frameworks, most of the commands associated with the collection tactic are uncommon enough to generate an alarm. These commands are generally executed by system administrators or common users who are rarely suspicious.
For this test, we executed the below command:
This command attempts to access file shares in the system through a WMIC command. This activity is associated with technique Data from Local System, T1005.
Exfiltration
Attackers usually try to exfiltrate important data collected directly from the infected system to their servers. Data compression before sending the data to the server is a clever way to reduce the amount of network traffic and speed things up.
To test this scenario we will run the following commands:
This code compresses data and then uploads it to the malicious web server. This technique is known as Data Compressed, T1002.
Command And Control
The Command And Control tactic is commonly seen when attackers try to communicate with their systems in order to gain control over the infected machine, checking connectivity or downloading next stages in the infection chain.
If we run the js-dropper.bat test from APTSimulator, which tries to download another piece of the infector using a legitimate Windows built-in utility we will see how that activity has been detected as a Remote File Copy and is classified as a Command And Control tactic.
CONCLUSION
In this blog we have seen several adversary simulation tools available for free that can be used to easily perform tests that would usually be assigned to a purple team. And we’ve seen how USM Anywhere can detect a wide variety of these techniques out of the box thanks to the threat content that the AT&T Alien Labs team adds to the USM Anywhere platform on a daily basis.