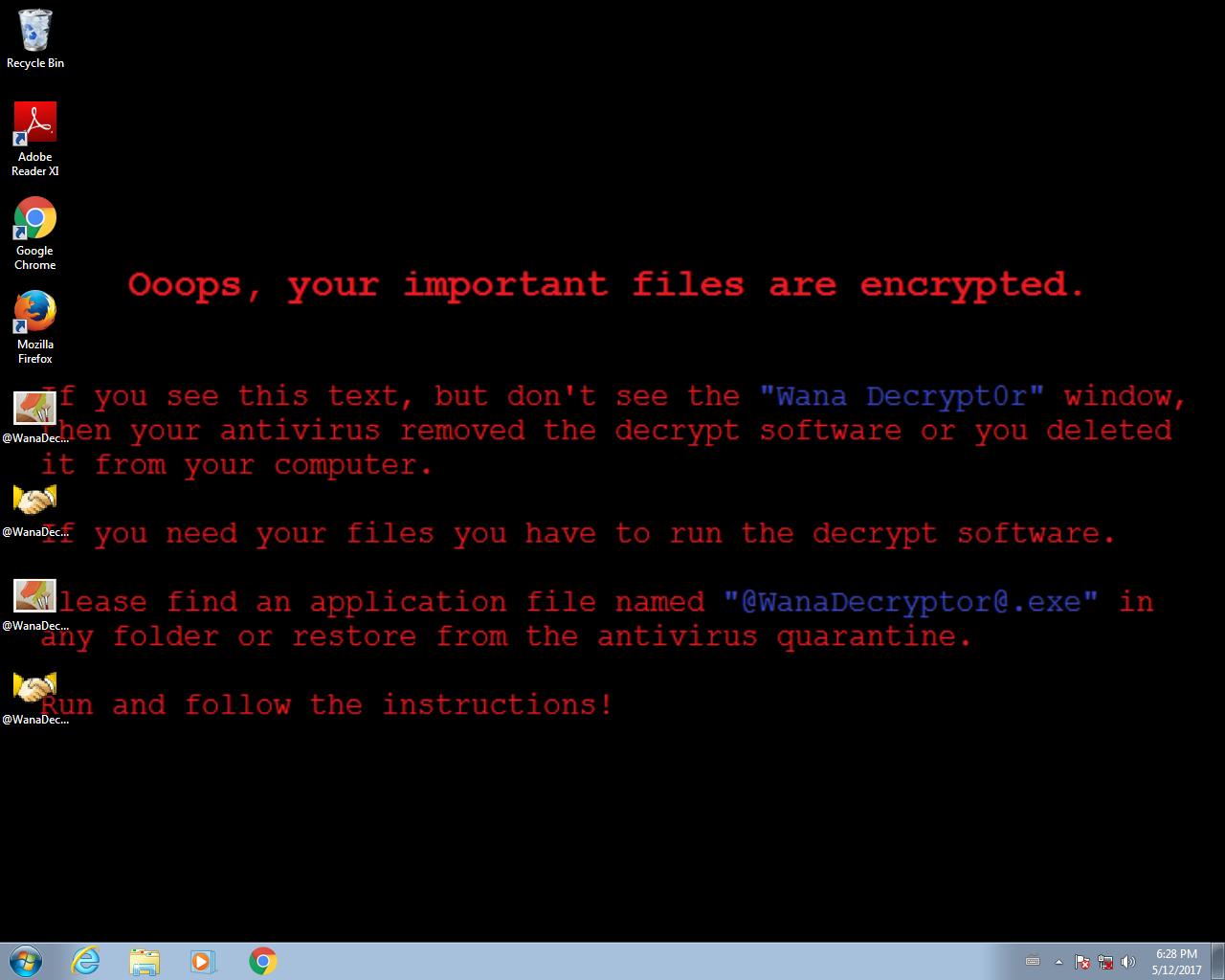
As of early this morning (May 12th, 2017), the AlienVault Labs team is seeing reports of a wave of infections using a ransomware variant called “WannaCry” that is being spread by a worm component that leverages a Windows-based vulnerability.
There have been reports of large telecommunication companies, banks and hospitals being affected. Tens of thousands of networks worldwide have been hit and the attacks do not appear to be targeted to any specific region or industry. Once infected, victims are asked to pay approximately $300 by Bitcoin, and it appears the attackers have found people willing to pay.
The AlienVault Labs team has created a Pulse in the Open Threat Exchange to share the indicators of compromise we have been able to obtain. These indicators can be used to help identify potential attacks in progress.
One method of command and control and secondary installation has been sinkholed by security researchers, however the attackers can still leverage a second communication mechanism via Tor.
The WannaCry ransomware is using the file extension .wncry, and it also deletes the Shadow Copies, which is a technology introduced into the Microsoft platforms as far back as Windows XP and Windows Vista as the Volume Shadow Copy service. This means that even backup copies produced by this service, such as Windows Backup and System Restore, would be affected as well.
cmd.exe /c vssadmin delete shadows /all /quiet & wmic shadowcopy delete & bcdedit /set {default} bootstatuspolicy ignoreallfailures & bcdedit /set {default} recoveryenabled no & wbadmin delete catalog -quiet (PID: 2292)
The following file is also created in the affected systems: @Please_Read_Me@.txt
Once it gets on a network, WannaCry exploits a known Microsoft Windows vulnerability (MS17-010) to spread. This vulnerability was released as part of the Shadow Brokers leaks back in April. Microsoft released a patch for MS17-010 on March 14th. Administrators are advised to immediately upgrade any systems that do not have this patch to avoid potential compromise by WannaCry. So far the only confirmed vector of the attacks is through an SMB exploit, which provides a worm-like mechanism of spreading WannaCrypt.
AlienVault USM Anywhere and USM Appliance are able to detect attempts to exploit this vulnerability via the following IDS signature released by AlienVault on April 18th:
ET EXPLOIT Possible ETERNALBLUE MS17-010 Echo Response
Yesterday we noted a sharp increase in external scans against our customers for the exploit, and we are investigating if it is related to today's attacks:
We will update this blog post as we discover more information about the ongoing situation.