What is capture the flag hacking?
This blog is designed for a person that is brand-new to Capture The Flag (CTF) hacking and explains the basics to give you the courage to enter a CTF and see for yourself what’s it’s like to participate. CTFs are events that are usually hosted at information security conferences, including the various BSides events. These events consist of a series of challenges that vary in their degree of difficulty, and that require participants to exercise different skillsets to solve. Once an individual challenge is solved, a “flag” is given to the player and they submit this flag to the CTF server to earn points. Players can be lone wolves who attempt the various challenges by themselves, or they can work with others to attempt to score the highest number of points as a team.
CTF events are usually timed, and the points are totaled once the time has expired. The winning player / team will be the one that solved the most challenges and thus secured the highest score.
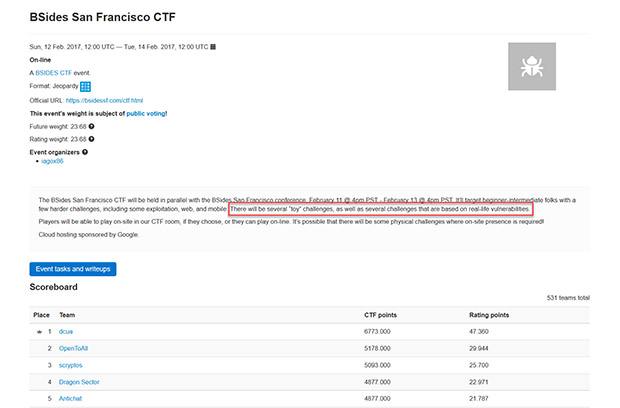
Here is a screen shot of a score board from a BSides San Francisco CTF event:
Please note the sentence that I’ve marked with a red box. As you will quickly see, CTF tasks are often based on real world incidents/vulnerabilities that give you a chance to experience how it’s actually done and better prepare you to defend your own systems from these types of attacks. So not only are CTF events fun, they can also be educational and professionally rewarding.
CTF Preparedness
If you’ve never experienced a CTF event before, don’t get frustrated or give up, because the key to any type of hacking is patience. While this is sometimes a difficult thing to have, the only way to learn is to persist and practice on your own (see this post further down on how to practice) and maybe next time you’ll score first place! One thing you can try to do during your first CTF event, if possible, is find a experienced team that’s willing to let you join them. Make sure you’re clear that this is your first CTF event and you’d really love for them to show you the ropes.
In my experience, members of the InfoSec community are usually very willing to share their knowledge with anyone interested in trying to learn and grow in this field. At the same time, however, one common theme you also often hear in the community is that there is a shortage of talent. At times this can be a very real struggle, and many professionals who have worked their way up in the field have spent considerable time to do so, sacrificing much to learn, practice and hone their craft. For this reason, before reaching out for help with basic questions, you should first research the topic and make an effort to figure things out on your own.
Within the InfoSec community, trust isn’t something you can place value on. If your job is to hack into a client’s network, they last thing anyone wants is for that sensitive information to be shared with anyone outside of the team. Trust is a critical component of this relationship and I cannot express enough how important it is to remain ethical during competitions as well. Finally, last but certainly not least: when you go to a CTF event, don’t forget to bring a laptop or another computer that has an operating system with various tools already installed (more on this below) as without that you’re going to be off to a rough start.
In summary, CTF are a great opportunity to learn, so if you’ve never experienced a CTF event or even a BSides event, I strongly encourage you to jump in and join one as soon as you can!

Adversary Simulation Service
Lets customers test their security operations and detection capabilities against advanced penetration testing techniques.
Learn moreTypes of Events
There are usually two different types of CTF events. The two most common types are:
- Red Team/Blue Team
- In this style of event the red team attempts to capture flags while the blue team attempts to defend the various flags from being captured.
- Red Team
- This style of event usually involves one or more people, working alone or on a team, who attempt to capture various flags while there is no team defending them.
Each type of event has various pros and cons. In a Red Team vs. Blue Team scenario, the attackers learn vital techniques while the defenders have a chance to learn how to defend their systems from an active attack. In a Red Team scenario, however, everyone gangs up on the poor CTF host and does their best to have it divulge every flag the attackers can get their digital claws on.
Types of Challenges
CTFs usually showcase different challenges that utilize or exercise specific areas of focus. Some popular areas of focus are:
- Programming
- These types of tasks usually require some sort of programming to solve. In most cases, it will involve a mixture of programming and some reverse engineering.
- “Crypto”
- These challenges feature common “real world” scenarios that often include the ever-popular ransomware type of malware.
- Exploitation
- These tasks will force you to determine how to exploit (using buffer overflow, string format, SQL injection, etc.…) a given running process on the CTF target machine.
- Reverse Engineering
- For tasks like this, reverse engineering will usually be required, for example, when the server sends you an executable.
How To Participate in a CTF Event?
My first experience with a CTF was at a local BSides event. I went to the BSides event with the following thought: “There are probably going to be a lot of skilled hackers here; I think I’ll take a Tails laptop that will allow me to take notes and surf the web when necessary.” While the mentality of wanting to protect my devices wasn’t exactly a bad idea, relying on a Tails made life rather difficult when it came to participating in the CTF event. To be fair, I didn’t realize there would be a CTF event there and so I didn’t even think about that aspect of the event. What I would recommend you use at your first CTF, in order of easiest to most difficult, would be one of the following:
- Kali Linux
- This distribution comes purpose-built for penetration testing. It’s packed with every tool imaginable and probably a ton more than you’ll never need to use.
- BlackArch
- This distribution is based on Arch Linux but comes pre-built, much like Kali does, with tons of security tools.
- Arch Linux
- This is a base Linux install that comes with standard Linux tools. If you choose this option, you’ll have to do the leg work of installing all the tools you can think of that you might need or at very minimum ensure that you have access to an internet connection to allow you to quickly install the tools you require at the event.
Examples
As I mentioned earlier, there was a BSides event in San Francisco that hosted a CTF session a few months ago. We can look more closely at this event to give you a better idea of what capture the flag is all about.
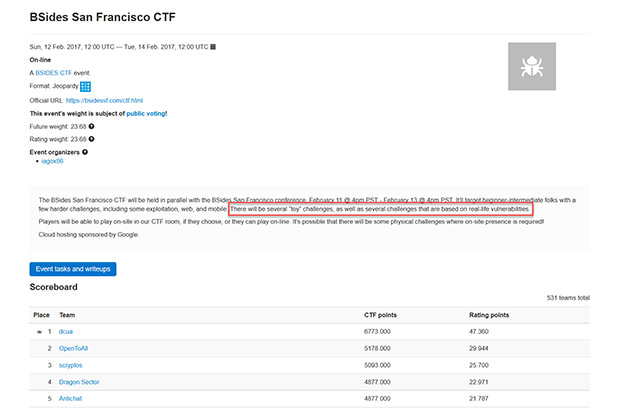
First, the screen shot above shows you the final score board, which I’ll also place here:
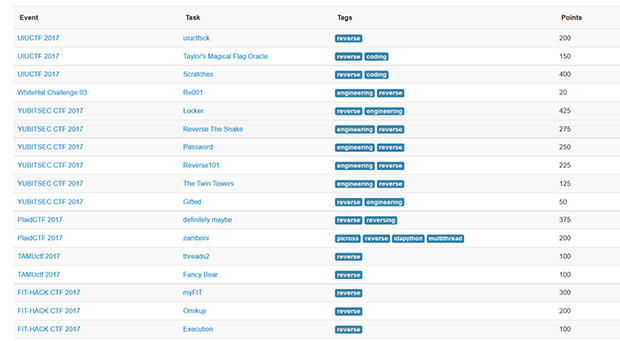
Please note that the winner won with 6,773,000 points while the next closest player had 5,178,000 points. That’s quite a lead which tells me that dcua is likely quite an experienced hacker/CTF player. Now let’s dig into the different types of tasks that we’ve spoken about previously. Here is a list of the different tasks that were available in this CTF event:
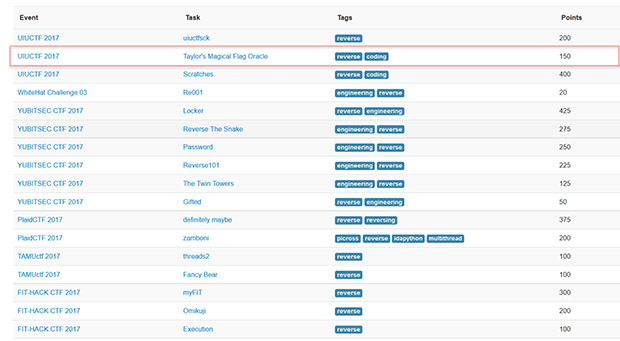
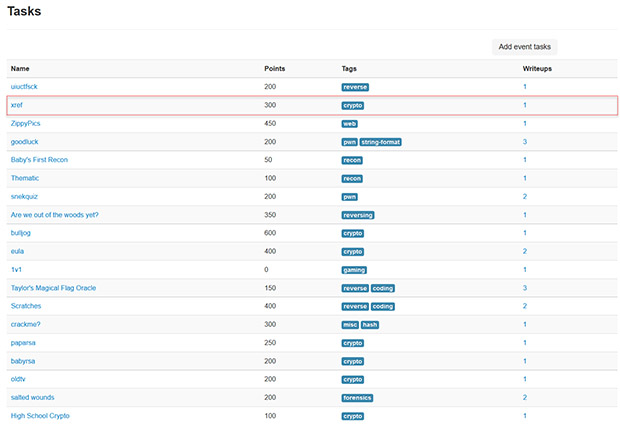
As you can see, there are different types of tasks and some of them overlap in terms of the skills required to solve them. Let’s take a more detailed look at some of the tasks from that list. We’ll just pick one:
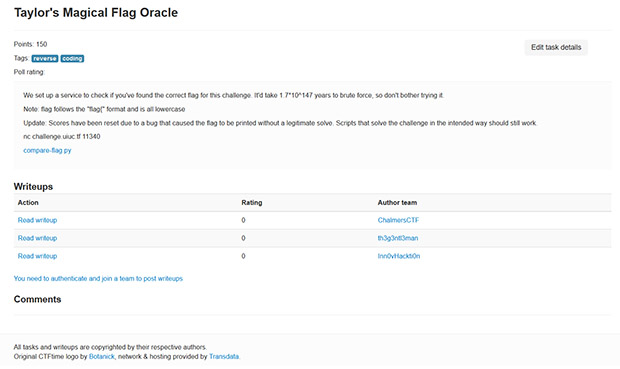
Taylor’s Magical Flag Oracle is a reverse engineering and coding based task that is worth 150 points. If you click the ‘Task’ link you’re presented with detailed information about what’s involved:
As you can see, there are a lot of details that are provided including hints about to how to solve this CTF challenge/task. Because this event has already concluded, there is also a “Writeups” section in which different players have submitting the steps they used to solve the challenge. This section can make for some very interesting reading and can also help you along if you are trying the challenge for yourself and need a nudge down the right path.
Let’s take a quick look at two more challenges and then I’ll move on to resources you can use to learn more about CTF, how to participate, or even how to host one.
For our next example, it seems timely to pick choose the ‘xref’ task given all the news about the recent WannaCry ransomware infections:
Here are the details for ‘xref’:
Notice that this description doesn’t provide a whole lot to go on. That’s what makes this task particularly interesting and somewhat of a challenge; if you’ve never done it before, it will be hard to know even where to start. Thankfully, though, this event is over so we’ll use one of the write ups to get an idea on how the challenge was solved.
The URL here: https://github.com/1337pwnie/ctf-writeups/tree/master/2017/UIUCTF provides the details. In this case, there is a README file contained in the .ZIP file provided that provides a hint. To solve the challenge, some code needs to be written (though the task appears to be missing the ‘programming’ tag). Rather than go over the entire write up here, feel free to browse through the URL and the step-by-step solution.
Next, let’s look at our last task:
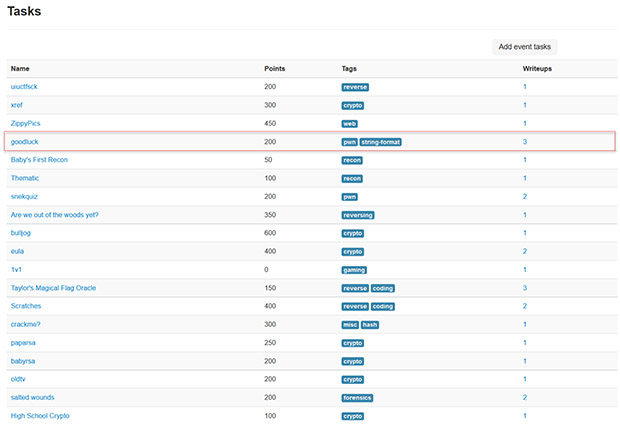
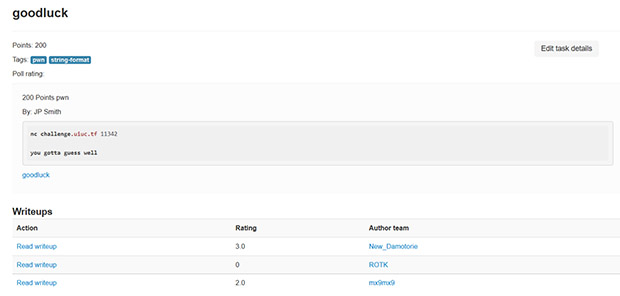
Goodluck is a string format “p0wn” vulnerability which essentially means scoring against it will spit out the flag. In the real world, ideally, accomplishing a task like this would give you unfettered access to the target machine. Here are the details about goodluck:
To solve this, we need to figure out how to utilize a string format vulnerability to give us a flag. The details of this are technical and in depth, so please see the resources section below for links to the various challenges mentioned in this post and you can then utilize the various write-ups about the different solutions that were used to solve the challenges/tasks.
How Can I Learn More About CTF?
There are a lot resources across the web that you can utilize to determine how to how to play a CTF or how to host a CTF. Query Google and YouTube for details on various upcoming events that you can get involved with. A lot these allow remote players to enter the game so you don’t necessarily have to attend an event physically to participate. The specific CTF I used to discuss how CTF works and my experiences with it was taken from here: https://ctftime.org/event/453.
Here is another interesting and useful resource that you may find handy: http://www.amanhardikar.com/mindmaps/Practice.html. This URL gives you access to a wide range of tools all involving vulnerable applications, web applications, operating systems, etc. These resources are a great place to start.
If Google, YouTube and the other resources presented here don’t answer your questions please feel free to reach out to me directly and I will try to help as much as I can. You can contact me on Twitter @CerebralMisjif. Feel free to follow me or ping me there and I’ll do my best to answer any questions you may have.
Conclusion
This blog is designed for a person brand-new to CTF, and it should give you the courage to enter a CTF and see for yourself what it’s like. CTF events are great places to meet fellow information security enthusiasts/professionals, and they also provide good opportunities to network, grow your skillset in a safe environment, and have fun while doing so. In some cases, awards are given out to the winner of a CTF event and those can be mighty nice to highlight if you’re seeking a career in the InfoSec field.
I hope you have found this article to be useful, and educational. I also hope you’ve gained a better understanding of what a CTF is, how it can help improve your knowledge, skillsets as well as ability to defend current systems, and most of all, how much fun a CTF can be! As I mentioned, some sites are now starting to allow remote players to participate in CTF events so keep an eye open for these if you’re interested. I hope to see you at one someday; please reach out to me if you’re going to be at any events so we can try to meet.