Given you’re here, you’re likely new to this topic, so please be aware in that fileless malware, fileless malware attack, and fileless attack are different words for the same thing. With that clear, let’s jump in!
What is Fileless Malware and How Does It Work?
There are many definitions of a fileless malware attack. I like the description from the Poneman Institute:
"A fileless attack is really an attack technique - what we're talking about is a technique - that avoids downloading malicious, executable files, usually to disk, at one stage or another by using exploits, macros, scripts, or legitimate system tools instead. Once compromised, these attacks also abuse legitimate systems and admin tools and processes to gain persistence, elevate privileges, and spread laterally across the network."
What's most confusing about these attacks is that they might not be 100% file-free. Typically, different technique types are termed “fileless”, but that doesn't mean the malware or an entire attack campaign won’t include executables at some stage. For example, a traditional phishing attack could have components of a fileless attack in it. Instead of opening the file, clicking on a link and it downloading something to your hard drive, malware may just run in your computer’s memory. It’s a phishing attack, but one piece is fileless. That scenario is more common than a completely fileless malware attack where everything is running in memory. More commonly, we're going to see traditional attacks: phishing campaigns, spoofs, Man in the Middles (MiTM), where something in the attack vector includes malicious code that runs in memory.
The other point is that you might hear “fileless attacks” referred to as non-malware attacks, memory-based attacks, in-memory attacks, zero footprint attacks, and macro attacks. These are all different flavors of attack techniques. The whole premise behind the attack is that it is designed to evade protection by traditional file-based or signature-based tools. So any technique designed to try to circumvent or evade detection by those tools really falls into the fileless attack category.
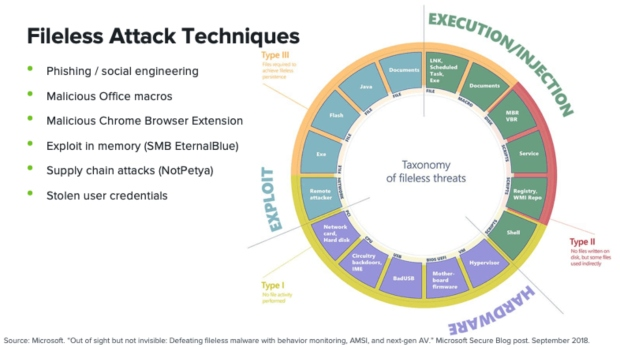
Just to get a picture of some of those techniques, in the picture below on the left there are some example delivery methods we see for fileless types of attacks. As we know, phishing and social engineering remain tactics that work for attackers.
This nice diagram from Microsoft that shows a full taxonomy of fileless threats. The diagram shows the breadth of different types of techniques and different types of tools, tactics, and procedures that malicious attackers are using to launch attacks.
There has been an increase in these attacks. McAfee puts it at 432% growth year over year in Powershell malware that they've witnessed. And SentinelOne found a 94% increase in just the first half of 2018.
We're seeing these attack methods persist because they are effective. Attackers are also looking for ways to infiltrate that don't require some kind of vulnerability exploit, to evade detection.
Trusted Admin Tools Leveraged for Fileless Attacks
Living off the land is the use of trusted admin tools to conduct malicious activity. It's a way to hide in plain sight.
These methods help attackers gain persistence within your environment, elevate privileges, and spread laterally across the network. Commonly, we see these with PowerShell, and WMI. We've also seen some using Visual Basic Scripts and UAC Bypass – where attackers are leveraging trusted tools to perform malicious actions. This is true within Linux and Windows as well.
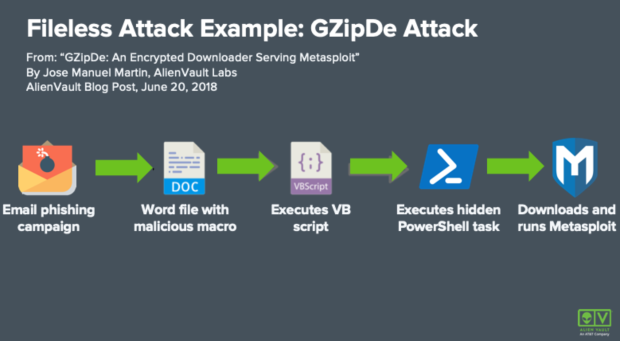
Example of a Fileless Malware Attack: GZipDe
Here’s an example of an attack and how, at different stages, we see the use of sanctioned applications or different types of a vector that might not register with a file detection tool.
Our AlienVault Labs team wrote about this in a blog post in 2018. The way this attack works is through an email phishing campaign that includes an attachment, such as a normal-looking Word document. Once you open that Word document, there's a malicious macro. Once those macros are enabled, a Visual Basic script executes, which launches a hidden PowerShell task, which then connects to the downloads and runs Metasploit in memory. You see a mix of file and fileless attack throughout the process.
At first glance, it looks like a traditional attack. Everyone is familiar with phishing campaigns. Then, as you go through the processes, it runs complete programs or attacks in memory - not writing it to a disk so that an anti-virus can’t see it.
It also makes this non-persistent. If an attacker is trying to evade audit and capture at a later point, fileless attacks are great.
Have a Suspect Machine?
One of the first steps you’ll do to investigate and audit a suspect machine is isolate it and turn it off. Since everything runs in memory in these types of attacks, as soon as you turn a suspect machine off, all evidence of the attack will be gone.
There are ways to keep these attacks persistent. You can write cron jobs or tasks to a system from a PowerShell script to attain persistence. However, generally, fileless malware attacks are gone once you reboot the computer.
Fileless Malware Detection
AlienVault® Open Threat Exchange® (OTX™) is a community of security researchers and practitioners. Individuals contribute information to the community after seeing attacks unfold in their environments, just to help others in the community keep up to date. It’s a great resource for anyone who wants to get an understanding of what’s happening in the wild.
I searched OTX™ for a few examples of fileless campaigns that we saw in 2018. This is from a quick search of “fileless”.
A perfect example of a fileless campaign is GhostMiner cryptomining. It was first recognized a few hundred days ago in our community. It started out as something you would download to your hard drive. It has morphed over time to using an executable PowerShell evasion framework so that they can execute the program within memory rather than downloading it to your drive. It installs cryptomining software, but in a new way.
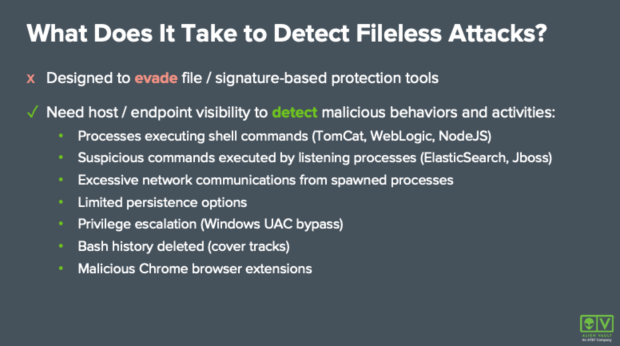
What does it take to detect and defend and begin to protect yourself against these attacks? They are designed to evade file and signature-based protection tools - traditional anti-virus types of tools. What you need is better visibility on the host and on the endpoint.
Some of the ways to detect them include things like looking for processes executing shell commands or suspicious commands executed by listening processes like ElasticSearch. We might see excessive network communications from processes that are somewhat abnormal or anomalous, as well as limited persistence and privilege escalation. We might also see attackers trying to cover their tracks by deleting their bash history or installing malicious Chrome browser extensions. All of these can be indicators that there is some type of fileless malware attack occurring in your environment. You’re going to need to spot anomalous behavior rather than a specific Indicator of Compromise (IoC).
To summarize:
Conclusion
The growing trend of fileless malware attacks will definitely make your life as a defender more challenging. There are free tools, like OTX, to help you keep up, and other offerings, like USM Anywhere to help quickly detect fileless attacks to prevent damage, even when there aren’t yet signatures or IoCs identified for the morphed version of fileless malware.
If you’re curious to explore further, check out the Fileless Attacks webcast by Danielle Russell and Aaron Genereaux where they walk you through actual detection examples.