The Internet was not designed with anonymity in mind, but things have changed. Anonymity has become a necessary and legitimate objective in many applications (browsing the internet, chatting, sending instant messages etc.). The main reason for this is that even if traffic is encrypted, only the content is encrypted. It is still possible to know the source and destination of the communication. On the flip side, anonymity in a corporate network can be devastating as it can open up organization to security risks, liability and potential litigation. And it is highly beneficial for your competitor to know your moves. So what can be done to stay anonymous for doing legitimate business?
If Elliot Alderson uses his computer to hack into an organization, he doesn’t want to leave a trace. No hacker wants to be traced by the victim IT team and investigative agencies like the FBI.
Tor can solve the issue, if you take care of the exit node. This is because unencrypted traffic can be sniffed once it leaves the TOR network. The last server on the TOR network is called exit node or exit relay.
However, integrating Tor with Kali Linux requires a lot of effort. In this article, we will discuss how to install / configure Whonix and how to integrate it with Kali Linux.
What is Whonix and how does it work?
Whonix is a Debian-based Linux operating system that aims to provide privacy, security and anonymity on the internet. The architecture consists of two main components:
- Whonix workstation
- Whonix gateway
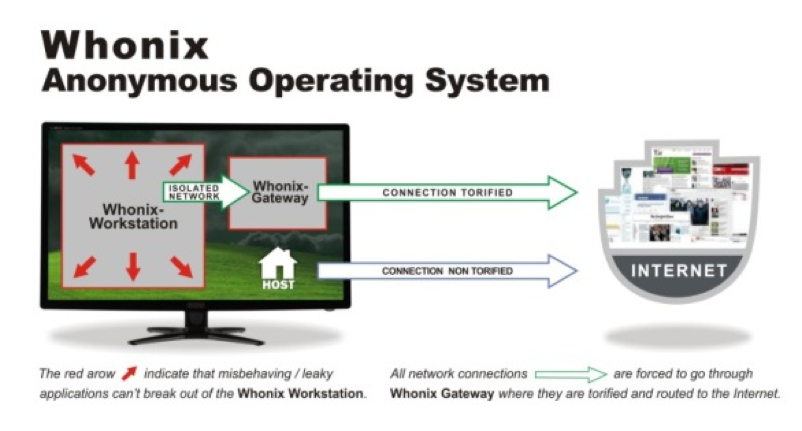
The workstation and the gateway both get installed in a virtual machine. The workstation consists of the desktop application, which connects with the Whonix gateway. he Whonix gateway is the only way for the workstation to communicate with the outside world because the workstation is an isolated machine and it has no idea about its own host IP and configuration.
The workstation uses a Whonix gateway to connect to the internet, and this gateway uses the Tor network. In addition, all traffic first gets encrypted before leaving the network. The workstation doesn’t reveal its real IP, which it doesn’t know. DNS leaks are also impossible and not even malware with root privileges can find out the user's real IP.
We can replace the Whonix workstation with Kali Linux and use Kali Linux anonymously. Here are the steps:
- Install and configure the Whonix gateway in a virtual machine
- Install and configure Kali Linux (using Whonix gateway in the DHCP) in the virtual machine
- All the traffic (Kali Linux) will be routed through the Tor network
- And you can browse anonymously
The things that you need:
The first step is to import the Whonix gateway into your VirtualBox. Click on New and then import the appliance.
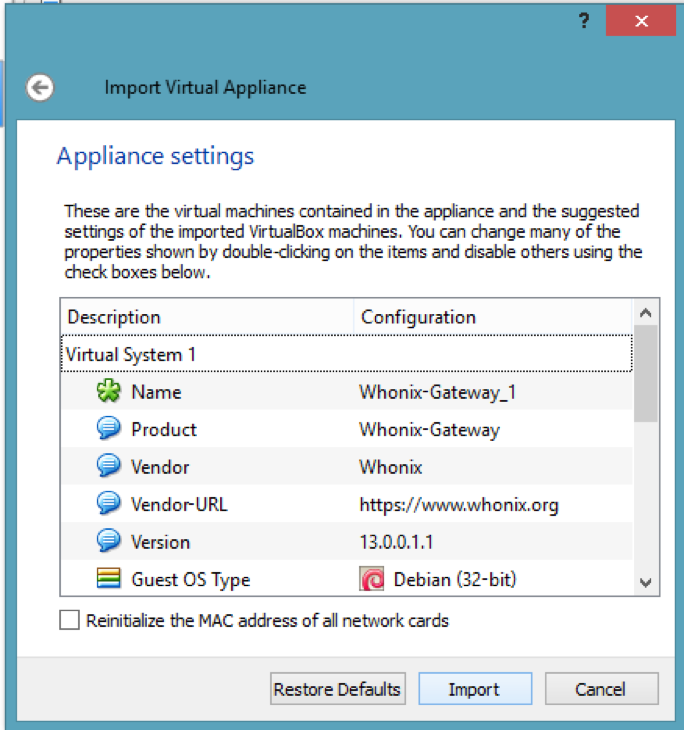
Accept all the components. Here, we have not downloaded the Whonix workstation because there is no need to get it. And, also we will not be installing the Whonix gateway - we just need to import it and run it. Click on the start button and let it load all the components. The next screen will be the terms and conditions, read carefully and accept them.
In the next couple of screens, accept the basic information and tell the machine to enable Tor for you. You should also select the Whonix Stable Repository and then finish the setup. It takes some time, but you will see the desktop with the pre-installed firewall and Tor configuration files. It will automatically connect with the Tor network, and you will get the pop-up. Click on the reload Tor icon to get the new Tor identity as below.
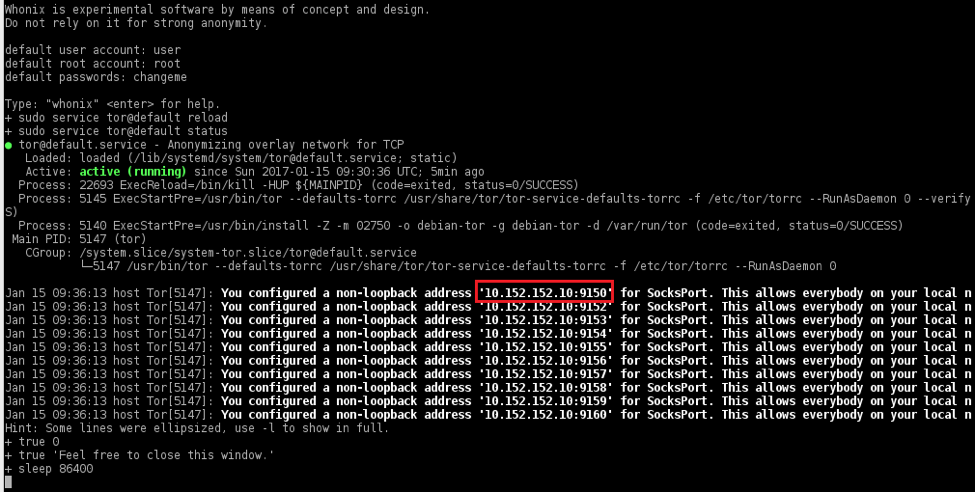
We are done with the Whonix configuration; now let’s move on to the Kali Linux setup. The loopback IP address mentioned in the above picture will be used as the Kali IP address. Create a new VM in VirtualBox, select the appropriate version and assign the memory. Create the new virtual hard-drive and select the VDI. We will be using the dynamic allocated size option so space won’t be an issue, just make sure you have sufficient space on your hard disk.
Go to the settings of this newly-created machine and go to system Processor and Enable the PAE/NX, because most of Linux uses this architecture.
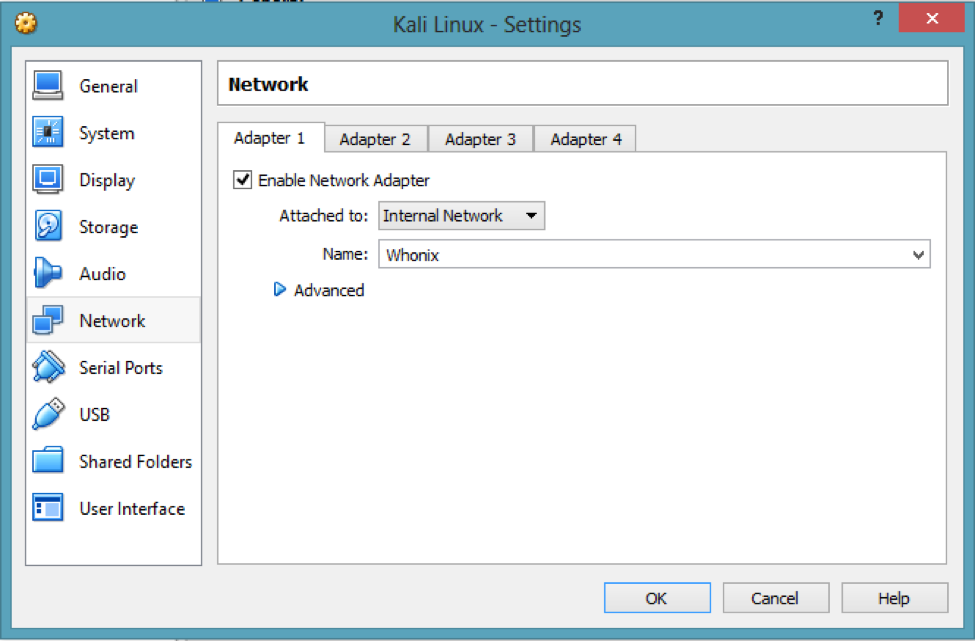
It’s time to configure the network - this is the most important part. Click on Network, enable the network adaptor, and attach it with Whonix as shown below:
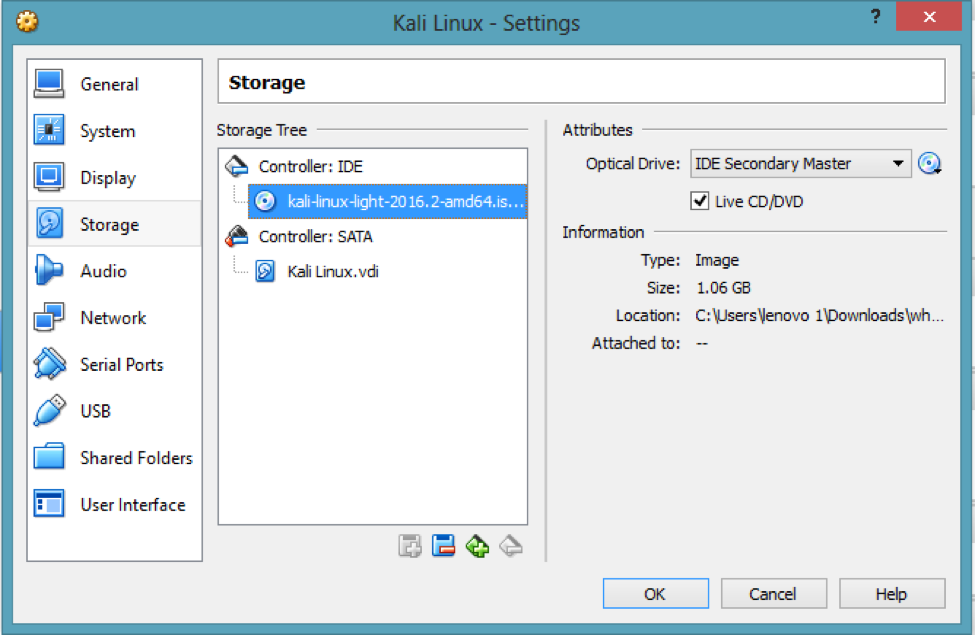
Now, link the setup with the Kali ISO image. In your settings, click on Storage, select the empty controller, and then browse the downloaded ISO image as below.
The setup is done. Save this configuration and start the VM. Select the graphical install option in the next window; give the basic details so that it will load the components. You will get a network error because we have not assigned the IP yet. Click on the continue button and then select manual settings:
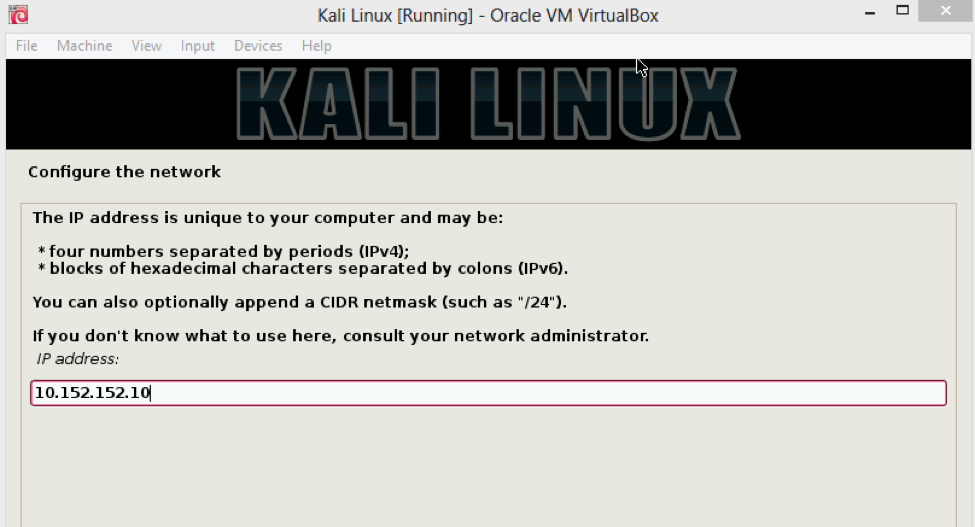
Use the IP address that has been provided by the Whonix gateway as described previously. It will automatically detect the netmask and the default IP too, so you can begin the installation. Start the newly installed Kali machine and we have our anonymous operating system loaded with all necessary tools.
How to prevent/block Tor inside your Business Network?
On the flip side, you may not want anonymous users inside your network. Another AlienVault blog on Tor discusses reasons why. So, how can you know if an employee is using Tor on a corporate resource? How can we detect/block Tor inside a network? Detecting and blocking the use of Tor is never as easy as using it.
The solution to this problem cannot purely rely on technology, but the combination of training and awareness, security policies, security best practices and technologies.
Prevention:
- Stop users from installing Tor: Implementing security controls that limit user access rights on a computer will help prevent the installation of unauthorized software or devices. For this, USB ports should be managed carefully or disabled. Tor can be pre-installed on a USB stick.
- Have a clear Policy on Tor Usage: make sure that the corporate security policy addresses explicitly the use of the Tor on corporate resources.
- Improve awareness and training: all employees should be trained and aware of risks related to using Tor in your corporate network.
Detection:
- Develop a blacklist of Tor nodes: Stop all outbound traffic related to Tor at the border firewalls level by creating an explicit outbound deny rule based on blacklisted IPs. The challenge with this is maintaining the blacklist to remain relevant. So, update the blacklist on a timely basis.
- Block all traffic using self-signed digital certificates: Tor is known for using self-generated SSL certificates (certificates not delivered by a recognized certificate authority) to encrypt traffic between nodes and servers. Blocking all outbound SSL traffic that uses self signed SSL certificates across your network, which is arguably a security best practice, can help prevent the use of Tor.
Detecting/blocking Tor in a corporate network is never an easy thing. Organizations should consider the deployment of more than one solution, as cited above, to improve your chances of preventing the use of Tor in their corporate network.
Tor is an important tool. However, it can have devastating results when used maliciously. Using Tor in a corporate network can open up organizations to security risks, liability and potential litigation. Your organization should pay close attention to the usage of Tor in their corporate network.

