Rohan Viegas of VMRay explains some of the key factors IT security teams should consider when evaluating a malware analysis sandbox and whether it’s a good fit for their existing SIEM environment. He then outlines how VMRay Analyzer complements and enhances the capabilities of AlienVault’s flagship platform, USM Anywhere.
For IT security organizations, malware threats and attacks continue to play a prominent role in the threat landscape. According to Verizon’s 2018 Data Breach Investigations Report:
- Of the 2,216 data breaches that were studied by participating security vendors, 30% involved malware.
- Six types of malware (ransomware, C2, RAM scraper, backdoor, etc.) were among the top 20 varieties of action used in the data breaches covered in the study.
- Ransomware, used primarily to commit financial crimes, is now involved in more than 40% of malware attacks.
- Malware attacks can be completed in minutes. However, due primarily to poor detection, an intrusion may not be discovered for weeks or months, potentially causing damage all the while.
“Full-featured SIEM, Looking for the Right Malware Sandbox”
When selecting an automated malware analysis sandbox to address these challenges, IT security teams should not only compare the side-by-side capabilities of different vendor products. They should also weigh how a particular sandbox will interact with their existing SIEM platform and the extent to which a product’s strengths (or its weaknesses) are utilized across the managed security ecosystem. Below are some key points to consider.
The sandbox’s detection efficacy. Malware today is designed to recognize when it is running inside an analysis environment and to stall or exit in the sandbox, thereby evading detection altogether or inhibiting the analysis by not fully revealing its behavior. This leaves blind spots in the analysis results, which can then be carried over to the SIEM. A key quality to look for in a sandbox is its ability to reliably conceal itself from the samples being analyzed so the malware can fully execute, giving you comprehensive visibility into the threat.
The quality of Threat Intelligence that can be shared. Another consideration is what types of threat information can be ingested by your SIEM and made available across your security environment. Important IOCs include severity scores, suspicious behaviors, network activity, dropped files etc. You also need to consider how complete that information is.
Full visibility into malware behavior is essential for generating quality threat intelligence. For instance, if you discover a malicious file, the analysis results should detail all the places it tried to reach out to, all the bad files it tried to create, and all the registry keys it tried to touch or modify.
How can the Threat Intelligence be used once your analysis results are handed off to your SIEM? Can the data be easily monitored? Correlated with other data sources? What actions can you take with this information? To build on the prior example, if your sandbox identifies a new malicious file that has reached out to an unfamiliar and presumably bad IP address, can you search your entire infrastructure for systems that have also accessed that address?
Rising to the Challenge
For organizations that have USM Anywhere or another comprehensive SIEM platform in place, adding VMRay Analyzer to the managed security environment addresses these core challenges, strengthening the ability to detect and respond to malware threats, attacks and vulnerabilities more quickly and effectively.
Unlike traditional malware sandbox solutions, VMRay Analyzer runs solely in the hypervisor layer and does not modify a single bit in the analysis environment. The sandbox remains completely invisible to the malware sample and can transparently monitor all aspects of the malware’s behavior, without triggering the evasion techniques that thwart detection and analysis in other sandboxes. In turn, analysis results provide complete and detailed visibility
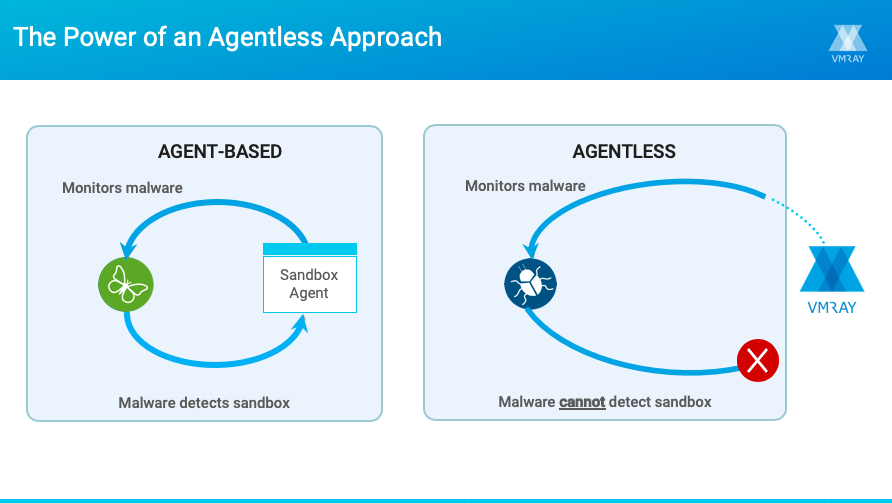
VMRay Analyzer’s Intelligent Monitoring engine, for example works much like an auto-zoom lens on a camera, adjusting to find the optimal level of monitoring. This allows analysts to distinguish between legitimate operations performed by the OS and trusted applications and unusual or malicious activities performed by the monitored sample. The result is to ensure security teams don’t miss any critical information while also delivering results that are precise and noise-free, with minimal false positives.
Once VMRay malware analysis results are ingested by the SIEM, using VMRay’s REST API interface, that information gains wider use and greater value. It can be monitored, searched, correlated with other data sources, and shared with security devices, such as firewalls and endpoint protection system. It can also be investigated and acted upon.
In addition, VMRay also has an out-of-the-box SIEM integration by publishing analysis alerts in Syslog/CEF format. These customizable syslog messages are generated when critical events occur.
Here are some of the ways VMRay Analyzer makes SIEM environments, such as USM Anywhere, more efficient, useful and comprehensive.
- Ensures timely analysis and detection of zero day and polymorphic threats—as well as known threats—and translates that information into actionable intelligence.
- Automatically propagates analysis results (including sample details, severity scores, IOCs, network activity and YARA rule matches) to the SIEM’s centralized environment.
- Improves the productivity and effectiveness of analysts and incident responders by providing all the information they need and only the information they need to analyze and respond to malware threats, vulnerabilities and attacks.
- Eliminates the productivity-killing noise and false positives that many sandboxes generate, while also ensuring irrelevant information is not pumped into the SIEM environment.
- Continually adds to the malware-related threat intelligence that is made available to the SIEM.
Sandboxes and SIEMs work in tandem to effectively detect malware or respond to a security breach. Choosing an evasion-resistant sandbox that generates precise, actionable Threat Intelligence ensures that you will have a good fit with your existing SIEM environment.

