The general consensus among InfoSec professionals is to patch critical vulnerabilities such as Apache Struts as soon as a patch is made available by the vendor. So why mightn’t your company simply patch Apache Struts and go on your merry way?
Not all events can be remediated immediately. Very often, intermediate mitigation measures must be taken to lower the risk of exploit and protect assets very quickly. For example, The Apache Struts vulnerability posed an immediate threat to webservers where the attacker could remotely execute arbitrary commands on the webserver. This is a very serious vulnerability with a high risk of exploitation and a large number of active exploits in the wild.
Apache made a patch available for the vulnerability and the solution would seem to be just applying the patch. However, this is not as simple a matter to execute as it may appear. Apache Struts is a framework for building Servlet/JSP web applications and is embedded in web applications. That means the development team in your organization has to update the library and rebuild their application. It then has to be deployed to QA for regression testing before being pushed to production. This requires time and change windows.
In addition, if they are running older versions of Apache Struts (and not merely one version before the vulnerability), they may face even more significant development and test time, further delaying the organization’s ability to patch the vulnerability.
An interim mitigation measure is to deploy signatures to an Intrusion Prevention System (IPS), thereby blocking the exploit traffic. Test the IPS rules by monitoring network traffic to ensure the malicious traffic is blocked until the system can be safely patched.
Important!
Containment measures such as this have a very short shelf life as attackers have access to these tools and can change the payload to circumvent the signature. It is critical to monitor traffic to ensure the IPS rule is correctly applied and is not being circumvented until a more permanent fix can be applied.
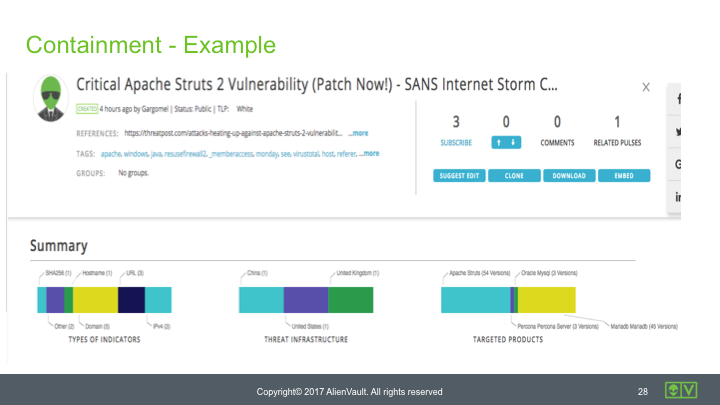
Here’s the OTX Pulse relating to the vulnerability: