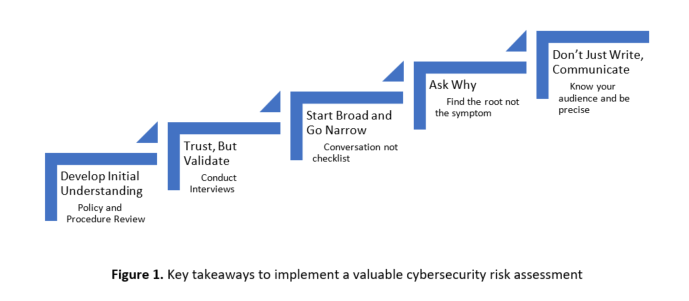
In an age where businesses are relying more than ever on the rapid advancements in technology to drive innovation, strategy, growth and competitive advantage, it is clear the prevalence of technology is not slowing down. But the increase in new devices and systems that utilize connectivity, as well as the transition to the network of devices and systems that were traditionally air-gapped, brings with it an increased cybersecurity risk.
Organizations large and small are attempting to defend against a constant barrage of potentially damaging cybersecurity attacks and struggling to keep up. Increasingly, they are finding that the best approach is taking a proactive, risk-based approach. By repeatedly conducting risk assessments, a holistic understanding of the organization’s risk landscape can be developed, and gaps that exist between people, processes and technology can be utilized to develop a prioritized roadmap for managing and tracking risk over time. The organizations gain the ability to make informed business decisions and move away from a reactive, whack-a-mole approach to cybersecurity.
Policies and procedures are the foundation
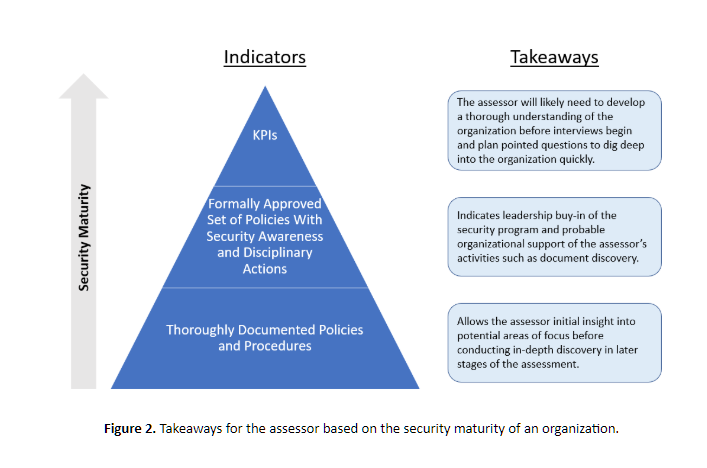
Strong cybersecurity policies and procedures are the foundation of a robust security program. A risk assessor can glean a significant amount of insight into the maturity of an organization’s cybersecurity program simply by looking at a few key areas of cybersecurity policies and procedures, such as those areas identified in the graphic below. They allow the assessor to gain valuable insight on the culture of cybersecurity within the organization, the reporting structure within the organization, the types of technologies present within the organization, and ultimately allows the assessor to drive discovery of information efficiently. This quick and efficient information discovery is especially important for external assessors or those that don’t already have an intimate understanding of the organization.
Documentation is not implementation
Having a strong cybersecurity posture on paper does not mean much if it is not implemented. It’s why conducting interviews of personnel is so important in a risk assessment and why the phrase “Trust but verify” is often half-facetiously repeated by cybersecurity professionals.
When seeking to verify through conducting interviews, it’s tempting to simply go down a list of specific and tailored questions, likely from a framework or compliance standard. Questions like “Does your organization implement a cybersecurity training and awareness training program?”, are to the point, brief, and answer the question asked by the assessment framework, but are not the best way to conduct interviews. Risk assessments are not audits and getting a yes/no answer to a question is not nearly as valuable as taking the time to develop a comprehensive understanding. By having a guided cybersecurity conversation and not simply going through a list of questions, an assessor is able to glean more information on an organization’s risk and develop more valuable findings and recommendations.
Start broad and go narrow
When conducting interviews, start at a ten-thousand-foot level of the topic being discussed, then use the framework as a general guide to steer the conversation and narrow down on specifics. As seen in the below example, the risk assessor should first ask open-ended questions that allow the interviewee a chance to explain the topic in-depth. This allows for a less restrictive and narrow-minded conversation and gives a potential view into how the topic at hand fits into the entire business.
Ask why
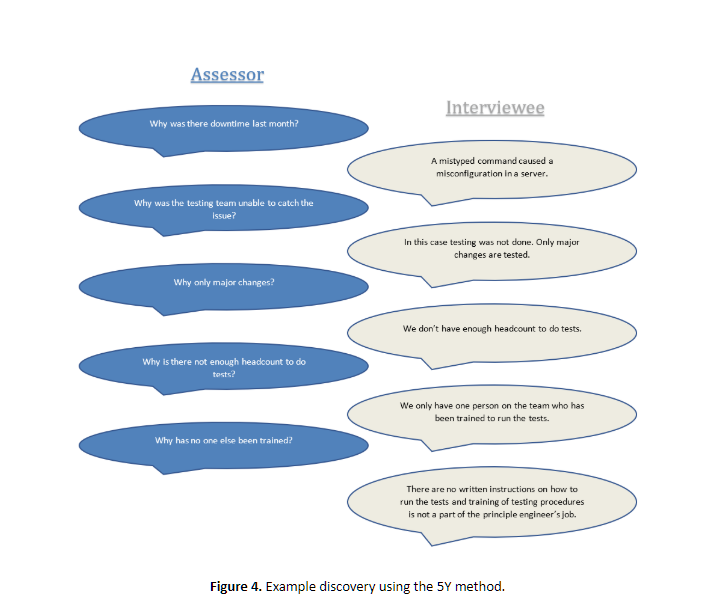
When interviews reveal that documentation does not match implementation, it is valuable to ask the question, “why?”. The well-known 5Y method states that in order to get to the root of an issue and not just deal with the symptoms, “why?” should be asked approximately five times. By employing this mindset, the assessor often reveals the most useful insights to an organization. In the below example, the symptoms of the issue include production downtime, lack of consistent testing, and not enough headcount. The identified root issue is that there is not a documented method for conducting tests and a lack of adequate training in tasks. By asking why repeatedly, the assessor is able to change from a weaker recommendation regarding additional testing to a stronger one that identifies how to promote efficient testing with their identified limited resources.
Original Recommendation: Additional testing should be performed before implementing changes in a production environment.
Recommendation After 5Y: Develop written testing procedures and include training of Jr. Engineers in the Principle Engineer’s job responsibilities to encourage thorough and consistent testing before implementation of changes in a production environment.
Don’t just write, communicate
An assessor is only as good as their report. Writing communication is key to a successful risk assessment, and it is important to know the audience of the assessment or sections of the assessment. An executive summary should be written in a very different manner than a section meant for an Information Systems principal.
It is important to be as precise as possible, stating only findings and recommendations that can be proven as true, and avoiding inferred findings or recommendations. At the end of the day, putting all of the gathered findings and recommendations together in a clear manner will give the organization a valuable tool for making informed risk decisions in the future.