Background
Bad actors are getting more sophisticated with the techniques they employ, including their ability to target specific industries and geographical regions. OnionDog is a good example of an attack that exploits a vulnerability in an application that is both popular in the target region, and is commonly deployed in the organizations the attackers wish to compromise.
The Helios team at 360 SkyEye Labs published a detailed analysis of the OnionDog APT earlier this year, and during the dog-days of Summer (see what I did there?) it seems appropriate to revisit this malware. OnionDog has been around for several years and exploits a vulnerability in Hangul office software, which is a popular Korean-language productivity suite. Hangul software is also widely deployed in South Korean Government agencies and facilities.
The group behind OnionDog is the Lazarus Group, exposed by AlienVault and other threat intelligence teams as part of Operation Blockbuster for its targeting of Sony Pictures and a range of other targets.
How it Works
OnionDog used various techniques to entice victims to open the malicious attachment. The attachments targeted a range of government agencies and utilities, such as power, water, ports, transit, and rail to lure its victims (see the screenshot of the ‘Investigation Report of the Korean Railway Accident” below).
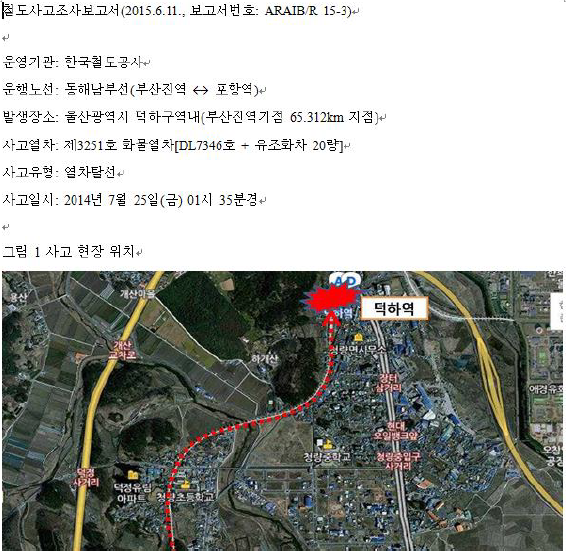
The malware installs a back door to the compromised system, collects and forwards information about the compromised systems to the C&C server, as well as infecting any device attached to the USB drive.
Impact on you
The regional nature of OnionDog will likely limit your exposure to this particular version of the threat if you’re not located in South Korea. However, if there is a user of Hangul software on your network, or if someone in your office may have visited an office that uses Hangul software and plugged a device into a compromised system, you may be at risk of data loss. However, although this version of the malware is localized to South Korea, the Lazarus Group could easily choose another popular application to target specific organizations in other countries.
How AlienVault Helps
The AlienVaultâ Unified Security Management (USM)™ platform delivers the essential security capabilities that organizations of all sizes need to detect, prioritize, and respond to threats like OnionDog. The AlienVault Labs team regularly updates the rulesets that drive the threat detection and response capabilities of the AlienVault USM platform, to keep you up to date with new and evolving threats such as OnionDog. The Labs team performs the threat research that most IT teams simply don’t have the expertise, time, budget, or tools to do themselves on the latest threats, and how to detect and respond to them.
The Labs team recently updated the USM platform’s ability to detect this new threat by adding IDS signatures to detect the malicious traffic and a correlation directive to link events from across a network that indicate a system compromised by OnionDog. Learn more about these updates in the latest Threat Intelligence Update summary posted in our Forums, where you can keep up to date on the latest threat intelligence updates, product news, and engage with your fellow Aliens.
Our AlienVault Labs team and the OTX community will continue to monitor the behavior of this threat, and will update the information in OTX when appropriate.
Also, the integration between our Open Threat Exchange (OTX) and USM means that you get alerted whenever indicators of compromise (IOCs) being discussed in OTX are present in your network. The result is that USM customers are up to date on the latest threat vectors, attacker techniques and defenses. Even if you don’t have USM, you can create a free account in OTX and interact with the community.

