What is the Cyber Kill Chain?
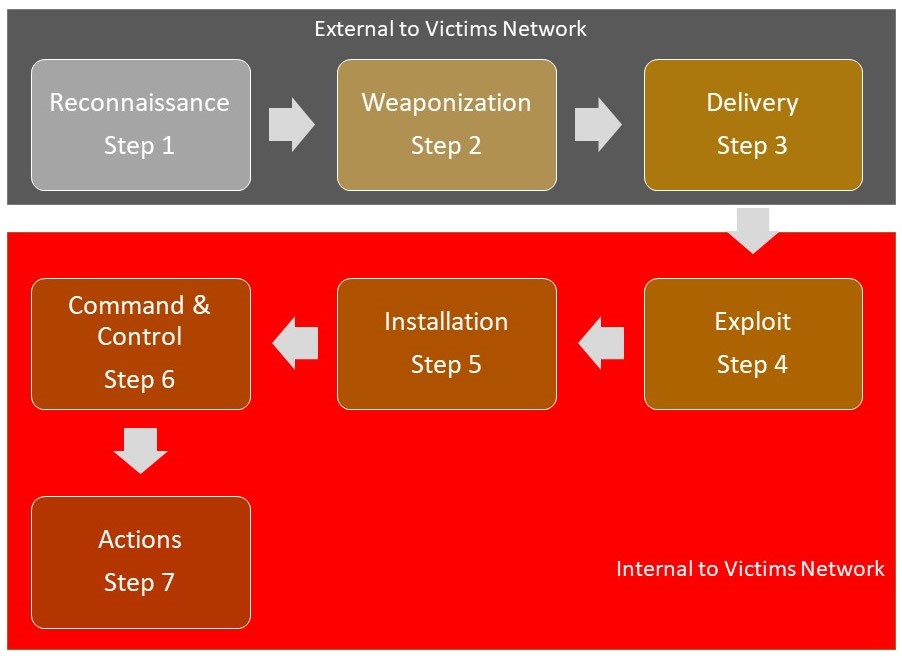
Developed by Lockheed Martin, the Cyber Kill Chain® (CKC) framework is part of the Intelligence Driven Defense® model for the identification and prevention of cyber intrusions activity. The model identifies what adversaries must complete in order to achieve their objective.
In recent years there have been numerous articles written to contest the effectiveness of the Cyber Kill Chain Model as it currently exists. The intent of this article is in no way to disavow or be critical of the work put into creating the Cyber Kill Chain by the LM-CIRT. Instead what this article strives to prove is that with slight modifications there are variances to the CKC that could improve its accuracy in non-traditional attack vectors. Today’s threat landscape has expanded and evermore, cyber-security overlaps many other aspects of security. This article strives to not only reinforce this point but to offer a framework to further the effectiveness of the traditional CKC by providing additional aspects to the CKC, enabling analysts to better understand and further their efforts in stopping data theft and cyber crime more effectively and efficiently.[1]
Purpose of this article – To test the validity of the CKC model against alternative attack vectors that do not utilize the classic cyber kill chain’s workflow, primarily based around internal actor theft of sensitive information.
The basis for the research - The research idea came from an article written by Ryan Stolte for the darkreading.com website. Link to the article is below.
Summary of the research – The author of the article, Ryan Stolte, posed the question of whether or not the existing Cyber Kill Chain Model as written by Lockheed Martin was sufficient for the increasingly versatile threat landscape of today versus the less dynamic threat landscape of 2007 when the CKC was first conceptualized and published.
The desired outcome of research – To create a new conceptual Internal Cyber Kill Chain Model that predicts the activities of an attack perpetrated by an internal malicious actor such as a disgruntled or disloyal employee.
In the referenced article, there is mention of two types of internal actors who are most likely to attempt to perpetrate a malicious cyber or social engineering attack on their employer.
Malicious Actors Defined
Most traditional attacks are carried out through some variant of a phishing attack, which means that most of the attacks are allowed into the network by an unknowing accomplice. In the article, the author breaks down the internal actors by categorizing them as “Flight Risks” and “Persistent Insiders”.
Flight Risks
Flight Risks: Employees looking to leave the company can elevate the risk of data loss. They tend to be less sophisticated and exhibit less cautious behavior on their way out. The kill chain–style reactive risk model begins with looking for early indicators — for example, if an employee frequently visits job search websites, something he or she typically would not do. However, even if employees are visiting those kinds of websites, that doesn’t necessarily mean they are a threat. They become a potential threat when they move to the next stage when, for example, they upload unusually large encrypted files to cloud storage at odd working hours.
Persistent Insiders
Persistent Insiders: Unlike flight risks, these threats are more sophisticated insiders who have no intention of leaving the organization. They repeatedly look for whatever sensitive data they can get their hands on to hurt the organization and/or sell for profit. Organizations won’t see these employees looking at job search websites. Instead, they will visit websites where they can circumvent web proxies. These are websites that allow them to hide and then jump to the Dark Web, for example, to move data and bypass controls.
The next stage of the chain is when they persistently try logging into systems to which they typically do not have access. They quietly “jiggle doors” looking for sensitive data that is outside the scope of their, their peers’, and the overall team’s role.
A combination of those two stages
An employee has repeatedly visited job search websites and has uploaded an unusually large file at odd working hours — is a good indication that the person is a flight risk and must be closely monitored. The next stage entails the employee aggressively trying to pull sensitive data off the network. They may attempt to email sensitive data to an outside address, get blocked, and continue to try other methods until they succeed.
Research
The Classic Model and the Reversal of the Classic Model
The seven steps of the CKC enhance visibility into an attack and enrich an analyst’s understanding of an adversary’s tactics, techniques, and procedures.
As the researcher reviewed the CKC Model against the objectives of the research it was found that of the 7 steps in the CKC, only 2 of those steps were applicable to the process necessary to successfully perpetuate an internal attack as described in Mr. Stolte’s article. Step 1, Reconnaissance, is absolutely necessary for any sort of attack either cyber or physical. The second was Step 7. Actions (Exfiltration), which is considered the end game of the objective. No other steps could be commonly attributed as consistently needed and utilized, or as being beneficial to track in order to prevent or resist an internal attacker.
As a matter of due diligence, the researcher also attempted to reverse the order of the CKC to compare that sequence to the research objectives in hopes there might be a better correlation, However, this research yielded no greater results and thus the research was halted.
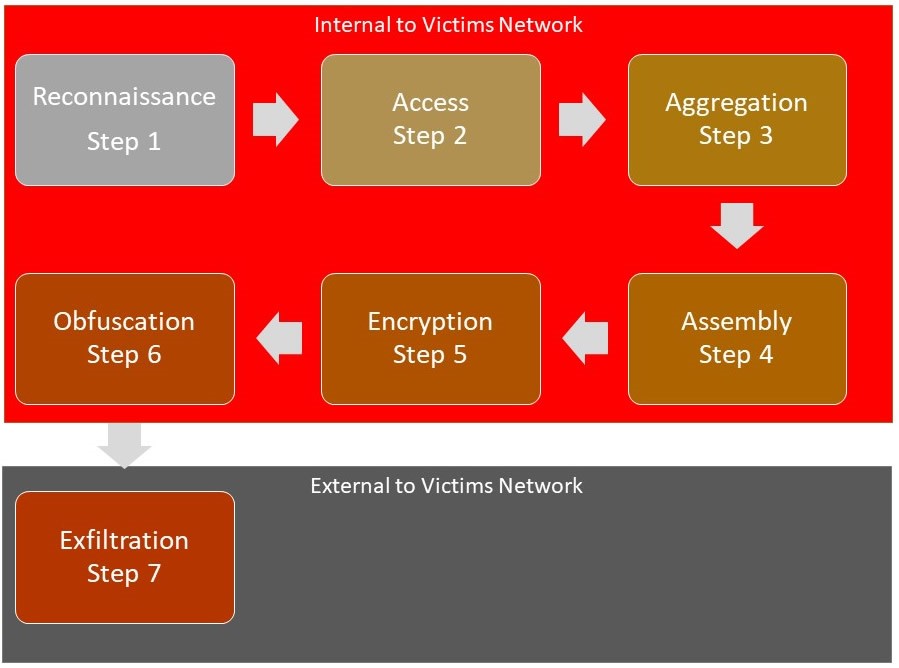
Once review and research were complete on the existing revision of the CKC Model, the researcher started development of an “Internal” Cyber Kill Chain Model, which would create a more efficient and effective process for stopping both internal cyber and physical attacks.
The “Internal” Cyber Kill Chain Model
The reference article talks heavily about the comparison of reactive vs. proactive approaches to cybersecurity. The goal is to stop a potential attack in progress before damage is done, which is nearly impossible as is witnessed with most attacks.
The “Internal” Cyber Kill Chain Model Breakdown
Many security experts tend to stick with the Classic CKC Model regardless of the origination of the attack or the method by which the attack is carried out. I do not subscribe to this thought process. I tend to think and have personally experienced an entirely different process that is taken from an internal actor.
Reconnaissance
A reconnaissance attack, as the name implies, is the efforts of a threat actor to gain as much information about the network as possible before launching other more serious types of attacks. Quite often, the reconnaissance attack is implemented by using readily available information. In the case of the “Internal” Cyber Kill Chain, it is the act of gathering information on network assets, files, databases and any other material that the attack may want to exfiltrate as well how using that information to decide the most effective method of exfiltration.
Access
In order for the actor to carry out the attack, they must gain access to the data they wish to steal if they don’t have access based on their corporate credentials. The actor must assess the following:
- What protections are in place from the IT team to prevent an actor from gaining access to data that they are not allowed permissions to;
- Who has access through their corporate credentials to gain access to the data the actor wants to exfiltrate;
- Once the user with the appropriate access has been identified, how can the actor gain access to the credentials of the said user;
- Is it possible for the actor to request credentials from the IT department? If so, how closely are the credentials monitored or audited.
Aggregation
Once the actor has access to the target data they can aggregate the target data and prepare it for exfiltration. This is the point in which the actor must know how to extract the target data from database systems. It is much easier if the actor is stealing non-database dependent files, however, there are ways to export data from a database, exfiltrate and restore to a spun up database in a different environment.
Assembly
This is the step where the actor prepares the data for exfiltration, such as:
- Migrating the data to a thumb-drive if exfiltrating via temporary storage;
- This step can also be combined with the next step if the actor is encrypting the data before exfiltration;
- Preparing the data to be sent across the internet via a secure connection if uploading to an offsite storage location;
- Creating and depositing the target package.
Encryption
This step is usually used with the previous step “Assembly” but can be used separately if the assembly stage is not necessary. Encryption is a very important part of the process because most detection systems do not employ deep scan capabilities. This is not 100% of cases, but it should become more commonplace as SSL and overall encrypted traffic become more commonplace. A host of major internet players are “calling out” non-encrypted internet traffic especially in the HTTP/HTTPS web protocols as common internet traffic is under constant scrutiny by many of the browser producers and major internet hubs.
Obfuscation
It is necessary for an actor to cover their tracks in today’s IT environment.
The actor will most likely utilize credentials that belong to someone else or credentials that are shared amongst several users as this will make it more difficult to trace the attack to the actor. Alternative options are to recon the location of the log files so that the actor can delete or manipulate the logs to remove proof of the exfiltration.
Exfiltration
This is the act of removing the target data from the premise of the company. Exfiltration can occur in a number of ways. We have covered a majority of them earlier in the article, however, here is a list that is not all-inclusive:
- Thumb Drive;
- External Hard Drive;
- Personal computer that is allowed to access the network domain;
- External storage such as One Drive, Dropbox or other CDN type storage location;
- Storage via the Darkweb;
- Direct to a buyer;
- DNS Tunneling Data Exfiltration;
- SSH and SSL Data Exfiltration via a proxy server to a location of the actor’s choosing;
- FTP & TFTP from an FTP location in the corporate network;
- Email, SMTP port exfiltration;
- Data dump to cloud services or hosting platform.
A smart actor is going to exfiltrate target data slowly and/or over time to minimize the likelihood of detection by monitoring systems or human detection. The actor should also exfiltrate target data at times when the exfiltration is least likely to show up like something out of the ordinary. For example, exfiltration in the middle of the night may be faster but may draw attention while doing so during times of moderate traffic will make detection less likely and more difficult to detect via monitoring systems.
Reference and Attribution
[1] More information on the Cyber Kill Model go to - https://www.lockheedmartin.com/en-us/capabilities/cyber/cyber-kill-chain.html
[2] Ryan Stolte - https://www.darkreading.com/attacks-breaches/reactive-or-proactive-making-the-case-for-new-kill-chains-/a/d-id/1332200
Neat blog back in 2014 on Cyber Kill Chain added by editor :blush: