 Role Availability Role Availability
|
 Read-Only Read-Only
|
 Investigator Investigator |
 Analyst Analyst
|
 Manager Manager
|
After you initialize a new USM Anywhere Sensor, you must configure it in the Setup Wizard. As you configure the sensor, you can enable USM Anywhere to perform specific actions through scheduled jobs, such as running an asset discovery scan or collecting security events Information collected and displayed that describes a single system or user level activity that took place. from a predefined cloud storage location.
About Accessing the Setup Wizard
The Setup Wizard is accessible under the following circumstances:
- After you first log in to the USM Anywhere web user interface (UI) and see the Welcome to USM Anywhere page, click Get Started to launch the Setup Wizard.
-
If you have already registered one USM Anywhere Sensor but did not complete the setup before logging out, the USM Anywhere Sensor Configuration page launches automatically at your next login to remind you to finalize configuration of the sensor. From that page, you click Configure to launch the Setup Wizard and complete the sensor configuration.
-
If you registered an additional USM Anywhere Sensor, but did not complete the setup, the Sensors page displays an error (
) in the Configured column. See Sensors Page Overview for more information.
Go to Data Sources > Sensors, and then click the sensor name to complete the sensor configuration. See USM Anywhere Sensor Management for more information.
Configuring the Sensor in the Setup Wizard
The first time you log in from the Welcome to USM Anywhere web page, the Setup Wizard prompts you to complete the configuration of the first deployed sensor. Thereafter, you can use the Sensors page to configure an additional sensor or to change the configuration options for a deployed sensor. See Sensors Page Overview for more information.
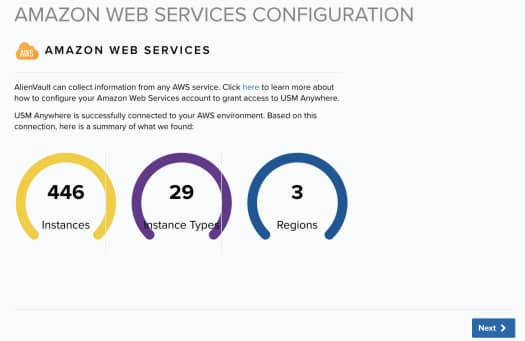
The Amazon Web Services Configuration page provides information about the asset discovery that occurs upon the initial deployment of the USM Anywhere Sensor, summarizing the number of instances, instance types, and regions in your environment.
Click Next to proceed with the Setup Wizard and complete additional configuration on each page.
The Network Security Monitoring page shows the status of the network interfaces monitored by the sensor (it could take a few moments to load the interfaces). All network adapters are configured for network monitoring by default.
You must manually enable port mirroring or port spanning Method of network monitoring in which a system passively collects network traffic on the same ports as other network devices., promiscuous mode Mode in which network IDS monitoring operates in passive listening mode, checking all IP packet traffic passing through it for threats., or both in a virtual switch to send a copy of the network traffic you want to analyze to these interfaces. This page provides links to documentation about how to configure your networking to allow for the interfaces to see the network traffic and perform network intrusion detection.
USM Anywhere connectivity and communications are handled by the first network interface connection on the Network Security Monitoring page. This is the primary network that provides asset scanning and log collection for the particular network.
You can connect additional interfaces to other networks for monitoring, or connect them to individual vSwitch port groups for virtual networks. Each interface should be connected to a vSwitch that mirrors a different subnet within your network.
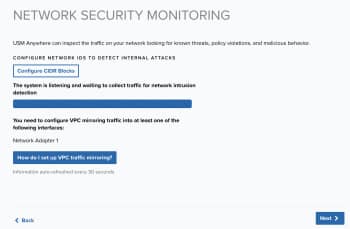
Use this page to verify that USM Anywhere can monitor your network traffic for security events.
Note: You can see red X icons next to the interfaces if the port mirroring or promiscuous mode is not configured. You might also see these icons if the network interfaces have not seen any traffic in the past 30 seconds.
To access detailed information about virtual private cloud (VPC) traffic mirroring
- Click How do I set up VPC traffic mirroring?
This opens a dialog box.
If you have not yet set up VPC traffic mirroring, see VPC Traffic Mirroring with an AWS Sensor for more information.
-
Click Next.
USM Anywhere automatically discovers several of out-of-box logs as long as you have enabled them within your Amazon Web Services (AWS) subscription. See AWS Log Discovery and Collection in USM Anywhere for more information about these logs and how they function within the AWS environment.
To enable the Amazon Simple Storage Service (S3) and Amazon CloudWatch out-of-box log collection jobs
On the Log Management page are syslog port numbers. (These ports are the same for all USM Anywhere Sensors.)
USM Anywhere collects third-party device, system, and application data through syslog An industry standard message logging system that is used on many devices and platforms. over UDP on port 514 and over TCP on ports 601 or 602 by default. It collects Transport Layer Security (TLS)-encrypted Transport layer security. Successor to Secure Sockets Layer (SSL) protocol. Provides security for communication over the Internet between client and server applications. data through TCP on ports 6514 or 6515 by default. These ports support the RFC 3164 and RFC 5424 formats. To configure any third-party devices to send data to USM Anywhere, you must provide the IP address and the port number of your USM Anywhere Sensor.
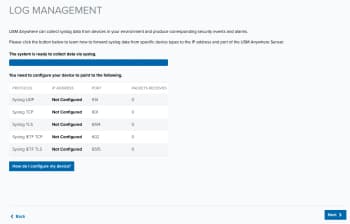
To enable log collection and configure your log management
- Make sure that you have granted the necessary permissions for your OS to allow USM Anywhere to access its logs. You can also integrate a wide variety of data sources to send log data over syslog to the USM Anywhere Sensor.
To learn how to configure your operating systems and supported third-party devices to forward syslog log data, see the following related topics:
- The Syslog Server Sensor App: Log collection (UDP, TCP, and TLS-encrypted TCP) from rsyslog
- Collecting Linux System Logs: Log collection from a Linux system
- Collecting Windows System Logs: Log collection from a Windows system
- Go to the specific AlienApp in USM Anywhere for instructions about syslog forwarding
- When you have finished the log collection setup and integrated any needed plugins, verify that the data transfer is occurring.
- Click Next when this step is complete.
Note: Because the log scan can take some time, you might not see all of the automatically discovered log sources immediately after deploying the first USM Anywhere Sensor.
AT&T Alien Labs™ Open Threat Exchange® (OTX™) is an open information-sharing and analysis network providing users with the ability to collaborate, research, and receive alerts on emerging threats and indicators of compromise (IoCs) such as IP addresses, file hashes, and domains.
You must have an OTX account to receive alerts based on threats identified in OTX. This account is separate from your USM Anywhere account. Go to The World’s First Truly Open Threat Intelligence Community to create an OTX account.
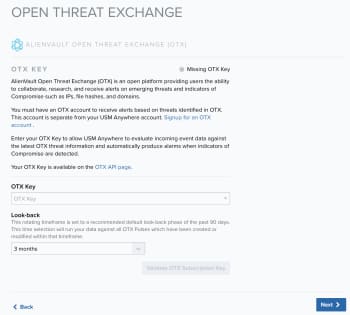
Note: If you do not already have an OTX account, click the Sign up link. This opens another browser tab or window that displays the OTX signup page. After you confirm your email address, you can log in to OTX and retrieve the unique API key for your account.
See Open Threat Exchange® and USM Anywhere for more information about OTX integration in USM Anywhere.
To enable USM Anywhere to evaluate event data against the latest OTX intelligence
- Log in to OTX and open the API page (https://otx.alienvault.com/api).
-
In the DirectConnect API Usage pane, click the
 icon to copy your unique OTX connection key.
icon to copy your unique OTX connection key. -
Return to the Open Threat Exchange (OTX) page of the USM Anywhere Sensor Setup Wizard and paste the value in the OTX Key text box.
-
Click Validate OTX Subscription Key.
With a successful validation of the key, the status at the top of the page changes to "Valid OTX key".
- Click Next when this task is complete.
The Congratulations page summarizes the status of your configuration.
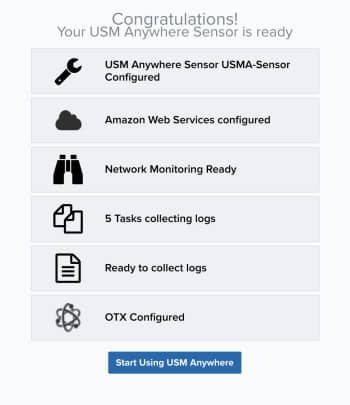
Click Start Using USM Anywhere, which takes you to the Overview dashboard.
Next...
Now is a great time to run a vulnerability scan. See Vulnerability Assessment for detailed information about running a vulnerability scan.


 Feedback
Feedback