During the last few years we have seen an increase on the number of malicious actors using tricks and browser vulnerabilities to enumerate the software that is running on the victim’s system using Internet Explorer.
In this blog post we will describe some of the techniques that attackers are using to perform reconnaisance that gives them information for future attacks. We have also seen these techniques being used to decide whether or not they exploit the victim based on detected Antivirus, versions of potential vulnerable software or the presence of certain security features such as Enhanced Mitigation Experience Toolkit EMET. EMET is a Microsoft tool that uses security mitigation to prevent vulnerabilities from being successfully exploited. This makes it more difficult for attackers – so they would prefer to avoid it.
1. Abusing res:\
The first technique we are describing affects Internet Explorer 8 and earlier. Internet Explorer blocks attempts to access the local file system using “file://” but it used to be possible to access image files within a resource section of a DLL/EXE. In a previous blog post we mentioned how attackers were using this technique as part of a waterhole campaign affecting a Thailand NGO. In that case we found the following code in the HTML of the affected website:
The resList array contains a list of executable files with resource sections containing an image file. An example using explorer.exe:
{id: 'Windows Explorer', res: 'res://explorer.exe/#2/#143'}
If we take a look at the resource sections present on explorer.exe we can find a resource named 143:
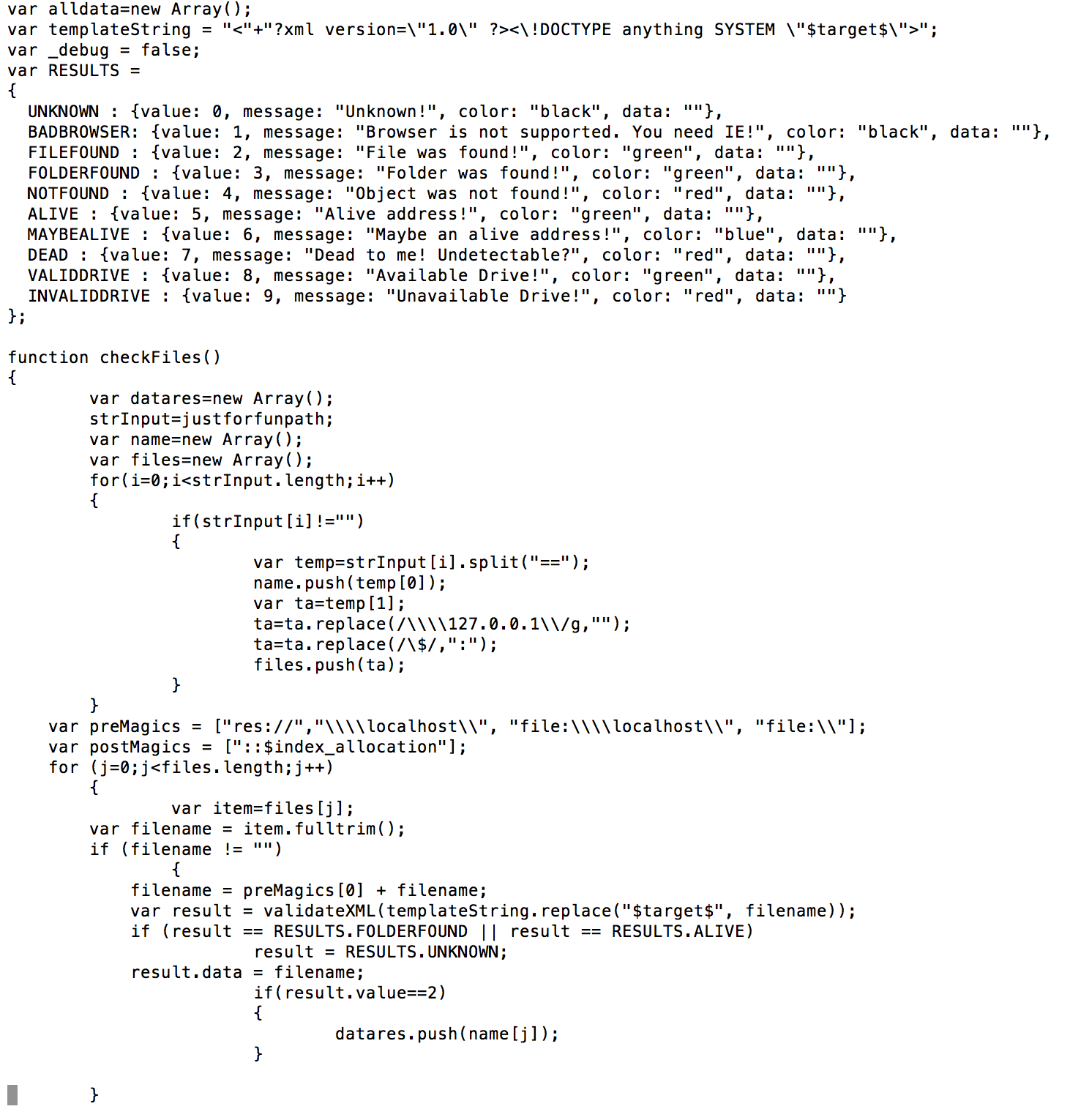
The resLis array contains a big list of executable files that is used to detect Antivirus software and VMware (probably to check if it is an analysis machine used by a security researcher):
The complete list of detected software is:
- Webroot
- Sophos
- Microsoft Security Client
- F-Secure
- BitDefender
- Norton Antivirus
- McAfee Antivirus
- Kingsoft Antivirus
- Avira Antivirus
- Kaspersky Antivirus
- 360 AV
- ESET NOD32
- Trend Micro Internet Security
- Rising Antivirus
- Vmware Player
- Vmware Tools
We found similar code being used by the Sykipot actors in combination with a phishing scheme. In that case the list of software was much longer and it detected common software along with security products:
The list of detected software:
- Microsoft Office (all versions)
- WPS (Kingsoft Office)
- Winrar
- Winzip
- 7z
- Adobre Reader (all versions)
- Skype
- Microsoft Outlook (all versions)
- Yahoo Messenger (all versions)
- Flashget
- Thunder
- Emule
- Serv-U
- RAdmin
- UltraVNC
- pcAnywhere
- RealVNC
- Fetion
- Google Talk
- AliIM
- POPO
- ICQLite
- ICQ
- Tencent Messenger
- Sina UC
- BaihI
- AIM
- Microsoft Messenger
- Windows Live MSN
- Windows Media Player (all versions)
- SSReader
- PPStream
- Storm Player
- TTPlayer
- Haojie SuperPlayer
- Winamp
- KuGoo
- UltraEdit
- Sylpheed
- ACDSee
- Photoshop
- Foxmail
- Gmail Notifier
- Windows Live Mail
- Adobe Media Player
- Flash CS
- Dreamwear
- Fireworks
- Delphi
- Java
- VMware Tools
- Tracks Eraser
- Microsoft Virtual PC
- VMware
- Microsoft ActiveSync
- Microsoft .NET
- PGP
- CCClient
- DriverGenius
- Daemon Tools
- MagicSet
- Baidu Tool
- Foxit Reader
- MySQL Server (all versions)
- SQLyog
- Firefox
- World IE
- TT IE
- Google Chrome
- Maxthon
- 360 IE
- Opera
- Safari
- SaaYaa
- GreenBrowser
Security software detected:
- Microsoft Security Essentials
- AVG
- 360
- SSM
- Keniu
- ESET
- NOD32
- Skynet Firewall
- Kingsoft
- Norton
- Rising AV
- Kaspersky
- JingMin kav
- Mcafee
- BitDefender
- AntiVir
- TrendMicro
- Avira
- Dr Web
- Avast
- Sophos
- Zone Alarm
- Panda Security
They also used this code snippet to detect Adobe Acrobat Reader (English, Chinese and Taiwanese.)
Finally they were also able to list the patches that were installed in the Microsoft platform using a predefined list of patch numbers:
2. Microsoft XMLDOM ActiveX control information disclosure vulnerability
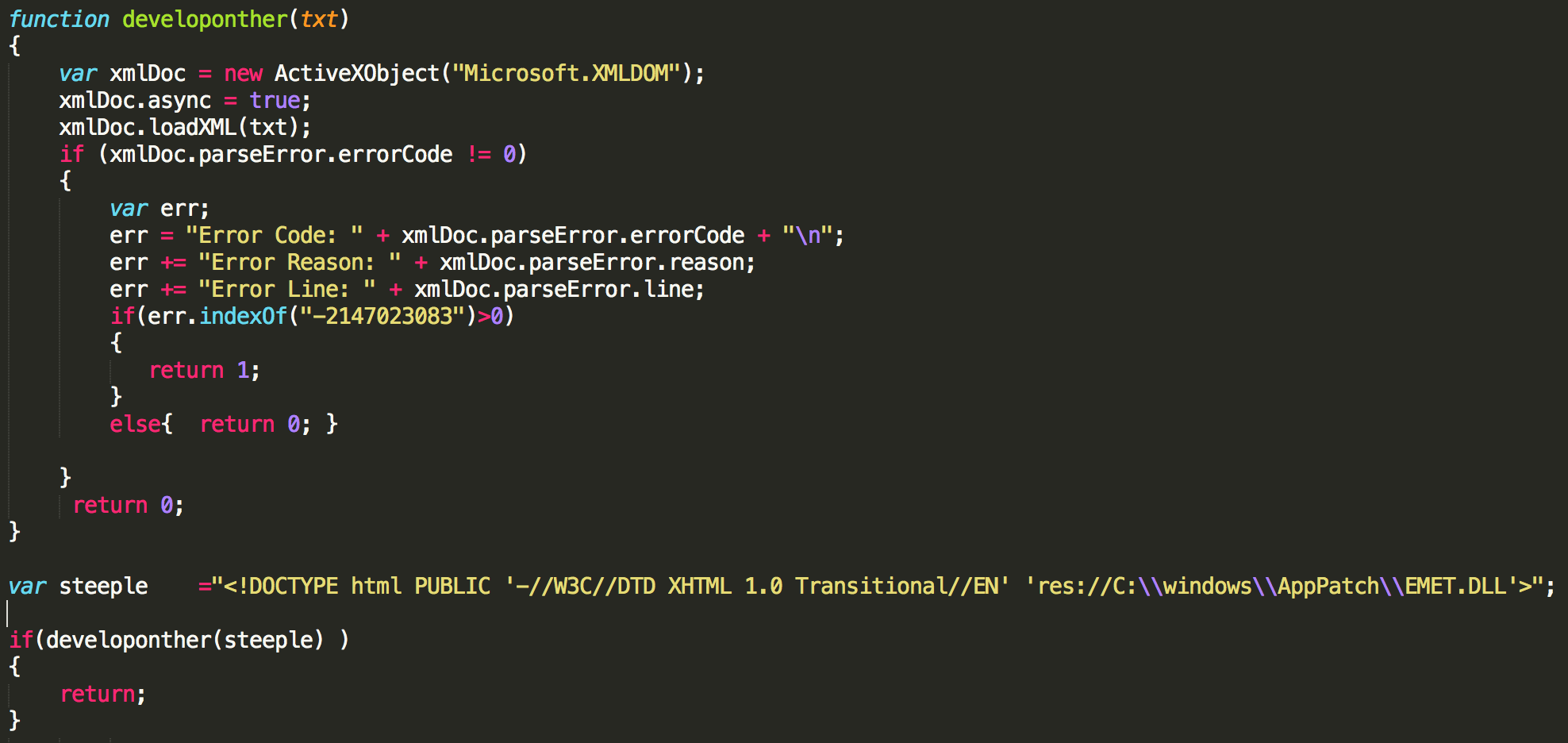
Another technique we found is being used by the Deep Panda actors. They usually use this code in waterholing campaigns to detect specific software installed on the intended victim's system. It exploits the XMLDOM ActiveX to check for the presence of multiple files and folders:
This vulnerability was disclosed last year and it affects Internet Explorer versions 6 through 11 running on Windows through version 8.1.
Software enumerated includes most of the Antivirus and endpoint security products on the market:
- 7z
- AhnLab_V3
- BkavHome
- Java
- COMODO
- Dr.Web
- ESET-SMART
- ESTsoft
- F-PROT
- F-Secure
- Fortinet
- IKARUS
- Immunet
- JiangMin
- Kaspersky_2012
- Kaspersky_2013
- Kaspersky_Endpoint_Security_8
- Mse
- Norman
- Norton
- Nprotect
- Outpost
- PC_Tools
- QuickHeal
- Rising
- Rising_firewall
- SQLServer
- SUPERAntiSpyware
- Sunbelt
- Symantec_Endpoint12
- Trend2013
- ViRobot4
- VirusBuster
- WinRAR
- a-squared
- antiyfx
- avg2012
- bitdefender_2013
- eScan
- eset_nod32
- f-secure2011
- iTunes
- mcafee-x64
- mcafee_enterprise
- north-x64
- sophos
- symantec-endpoint
- systemwaler
- systemwaler-cap
- trend
- trend-x64
- var justforfunpath
- vmware-client
- vmware-server
- winzip
3. More XMLDOM vulnerabilities
At the beginning of the year we found a different method being used in combination with a Zeroday vulnerability affecting Internet Explorer (CVE-2014-0322) targeting the French Aerospace Association. In that case we found the following code snippet.
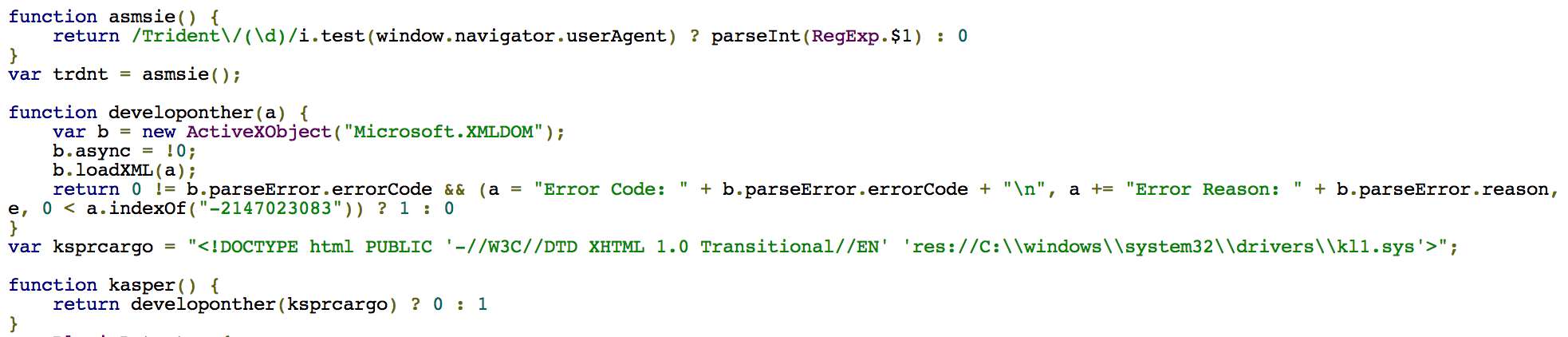
The attackers were using a similar technique to detect if EMET was present on the system. If EMET was detected they didn’t trigger the exploit since EMET was able to block it and alert the user to the 0 Day and diminish the attacker's effectiveness.
A month after the exploit code was made public we detected the same technique being used in the Angler Exploit Kit. They were using it to detect Kaspersky Antivirus.
In recent samples of the Angler Exploit Kit we have seen an improved version where they added detection for TrendMicro products.
In this blog post we have given an overview of the different techniques attackers are using to enumerate software running on a remote system. These techniques can give attackers information that they can use in future attacks to exploit certain vectors based on the software running (or not running) on a system. In addition, we've illustrated ways were cybercriminals have adapted and copied techniques used by more advanced attackers for their own purposes.
References:
Vulnerability in Internet Explorer 10.1
URI Use and Abuse
Angler Exploit Kit








_17.05.21.png)

