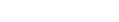Building a SOC in the real world
We’ve covered a lot of ground in this guide, in terms of showing the best ways to leverage people, process, technologies, and threat intelligence to build a SOC. At this point, it is instructive to look at real world examples of building a SOC using AlienVault as the foundation.
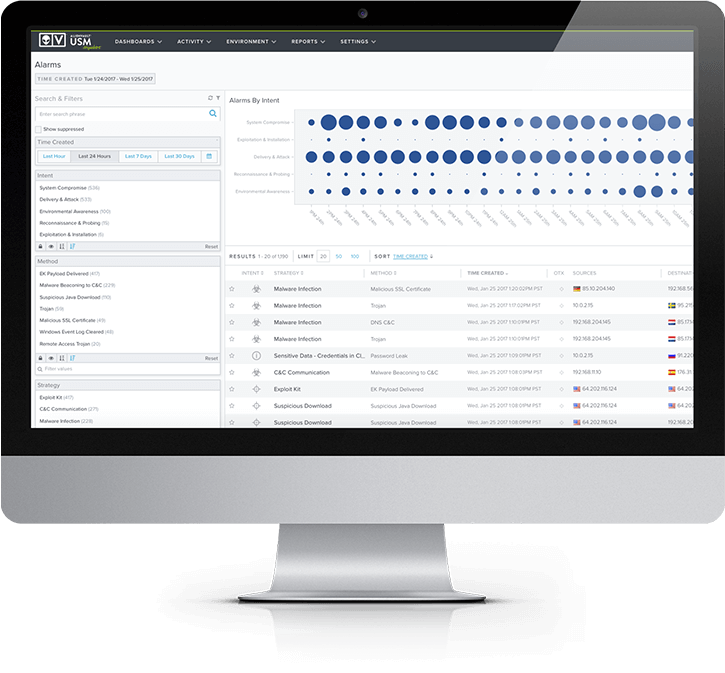
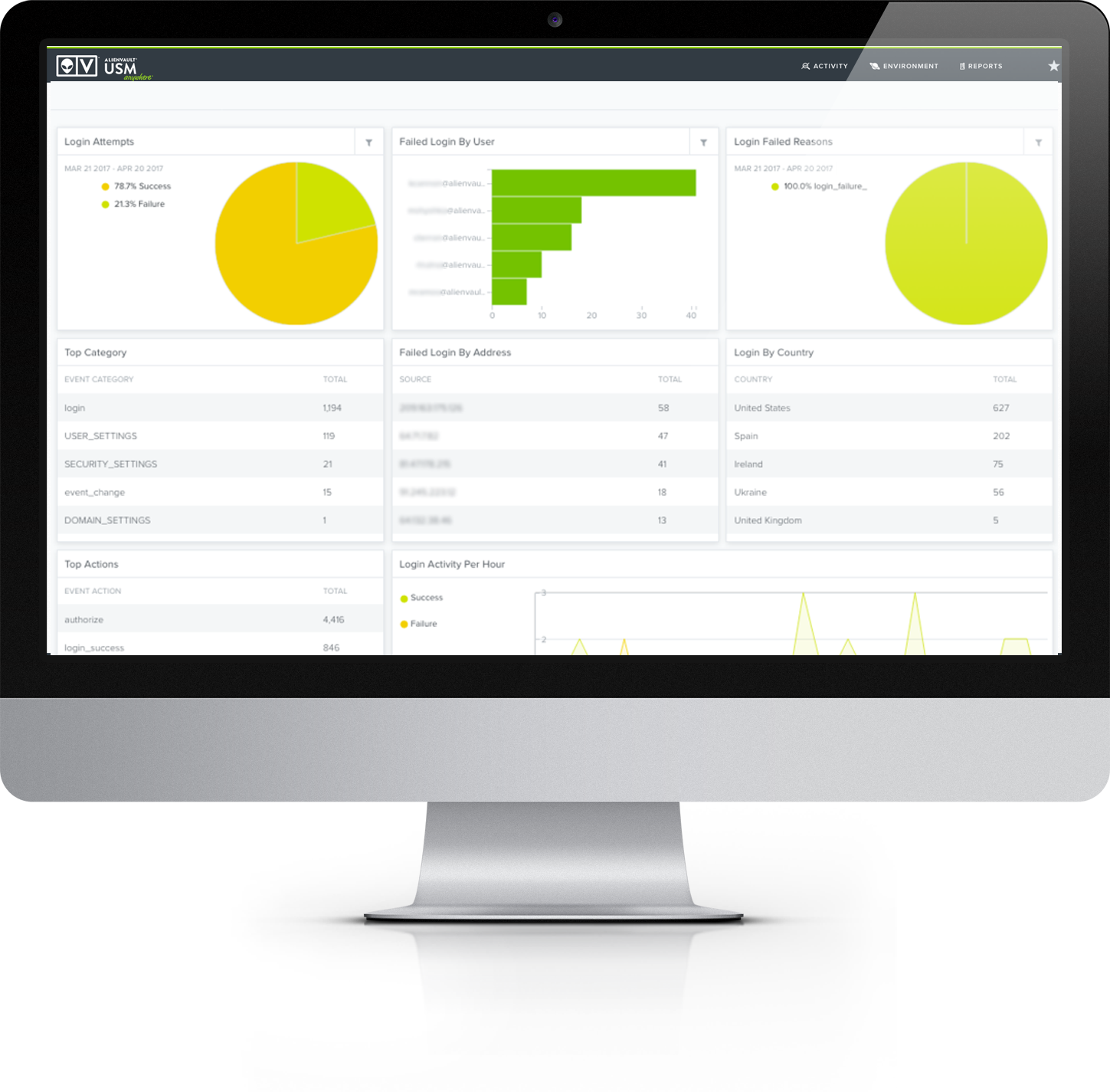
In each of these cases, SOC teams benefited from using a single platform with integrated yet disparate technologies for a full picture view that is continually updated with emerging threat intelligence. This unified perspective simplifies security monitoring, supports incident response workflows, and provides all the core functionality required for building a SOC.
After building their SOCs using AlienVault® Unified Security Management® (USM), these customers have discovered 3 critical lessons learned:
- Become informed. Not overwhelmed.
- Know when to ask for help. And where to go for it.
- Broaden impact with AlienVault USM. Internally & externally.
Key Summary
Building a SOC in the real world. Examine real-world use cases where AlienVault’s technologies, communities, and threat intelligence provide the perfect SOC set-up.
Real World Lesson 1
Become Informed. Not Overwhelmed.
Building a SOC may seem rather intimidating at first. You may be the only person in your entire company that is responsible for IT security. The thought of building an operations center when you’re the only person who can staff it too seems rather ludicrous. At the same time, we’ve seen it with our own eyes.
Meet Matthew. Matthew is CISSP certified and has more than 25 years in IT. He’s solely responsible for the IT and IT security of over 13,000 users for Council Rock School District in southeastern PA. As a result, Matthew has encountered many challenges along the way and has had to adapt and be as creative as possible at every stage.
For example, rather than becoming overwhelmed by all the work in managing, maintaining, and securing thousands of distributed users’ access, Matthew decided to become informed. He couldn’t rely on a huge budget for separate point products for security monitoring, so he turned to open source for answers.
After a few months, Matthew migrated from AlienVault OSSIM to AlienVault USM, because it was important to have a fully supported product as the foundation of their SOC. It was also essential for Matthew to have reports and dashboards he could share throughout the district as well as with auditors - to demonstrate compliance with requirements for vulnerability assessment, log analysis,
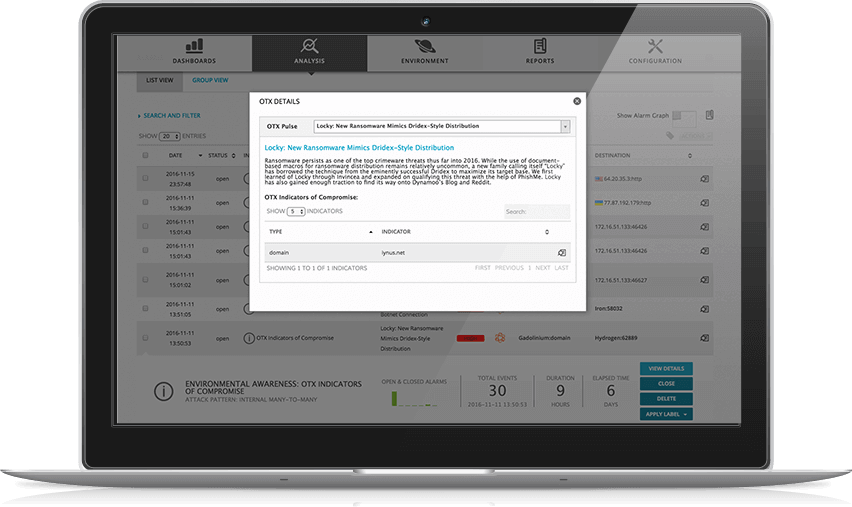
and other security controls. AlienVault USM scans, reports, and dashboards are constantly updated with threat intelligence from AlienVault Labs. In fact, the AlienVault Labs Security Research Team has become an extension of Matthew’s overall security monitoring program. They evaluate and translate threat data into integrated security intelligence that is updated continuously in AlienVault USM via a coordinated set of advanced correlation rules—meaning Matthew can detect emerging threats without taking the time to do the necessary research and write correlation directives himself. In fact, the AlienVault Labs Security Research Team has become an extension of Matthew’s overall security monitoring program. They evaluate and translate threat data into integrated security intelligence that is updated continuously in USM via a coordinated set of advanced correlation rules—meaning Matthew can detect emerging threats without taking the time to do the necessary research and write correlation directives himself.
“My favorite USM feature is the cyber kill chain screen. It makes it really easy for me to prioritize and investigate alarms. I believe those features are what really allowed me to justify to management why we should go with a paid solution.”
– Matthew J. Frederickson,
CISSP District Director of IT for Council Rock School
Key Takeaways & Next Steps
- Consolidate all the essential SOC capabilities into a single platform to overcome the complexities of managing multiple products, feeds, and reports.
- Detect the latest threats by integrating emerging threat intelligence from the AlienVault Labs Security research team, including asset database updates, updated vulnerability checks, updated rules, and more.
- Integrate AlienVault USM with dynamic & collaborative threat indicators from AlienVault Open Threat Exchange® (OTX).
Real World Lesson 2
Know When To Ask For Help
You may not feel as if you’re in a position to build a SOC and manage it on your own. Based on your company’s line of business and the size and skillset of the IT department, you may decide outsourcing to an MSSP (managed security service provider) is a viable option. Many global and regional MSSPs are set-up to provide 24x7x365 SOC support, which includes vulnerability assessment, compliance reporting, alert response services and more.
And many of them rely on AlienVault USM, AlienVault OTX, and the AlienVault Labs Security Research Team as the foundational elements in building their SOCs.
Hawaiian Telcom
As Hawaii’s technology leader in integrated communications and network solutions, Hawaiian Telcom runs a 24x7 state-of-the-art network and security operations center. In 2010, they launched Managed Network and Security Services, and turned to AlienVault USM as the foundation for monitoring and maintaining network security for their business customers.
Most of their business customers lack the cyber security skills needed to manage security operations on a constant basis, and also struggle to demonstrate regulatory compliance with standards such as PCI DSS. The team at Hawaiian Telcom discovered two key trends from their customer base that indicated why they had turned to an MSSP for help.
One was that many customers were in need of a log tracking solution that could allow them to keep a close eye on exactly who was logging into their systems, what they were doing, and how they were getting in. Although the need came about largely because of PCI DSS mandates, which require companies to exhibit this capability, it also happens to be an extremely important indicator of overall security. According to a Verizon report, more than 90% of companies who had been breached did not have these controls in place.
“Hawaiian Telcom offers our customers the most up-to-date network security services supported by AlienVault Labs, which actively tracks & analyzes millions of threats to deliver the latest intelligence directly to the USM platform.”
–Matt Freeman,
Senior ManagerIP & Managed Services, Hawaiian Telcom
Another trend involved the rising cost of the individual security solutions that are necessary to serve these customers. Most of the time these customers lacked a complete set of the different capabilities required to build a SOC (asset inventory, vulnerability assessment, intrusion detection, etc.). They might have had one or two of these capabilities in existing tools, but nothing that tied everything together for them, or associated the data with emerging threat intelligence.
Hawaiian Telcom uses the AlienVault USM platform as their primary SIEM platform for these customers, while also leveraging the critical security capabilities built into the system, such as asset discovery, behavioral monitoring, vulnerability assessment, and intrusion detection. They also enjoy the fact that the AlienVault Labs Security Research Team constantly updates these services based on an analysis of emerging risks. And finally, many of their SOC analysts rely on AlienVault OTX pulses for the latest threat indicators and countermeasures.
Key Takeaways & Next Steps
- When your business requires constant security monitoring and compliance reporting, and you don’t have the skills, tools, or staff to achieve this, an MSSP might be a good choice.
- Find an MSSP in your area that uses AlienVault.
- Apply to become an AlienVault-certified MSSP partner.
Real World Lesson 3
Use AlienVault USM to Broaden Impact
As a SOC analyst, you know that achieving visibility is a critical success factor in detecting the threats facing your company. The more you can discover about a threat, and its details, scope and impact, the more likely you’ll be able to mitigate it. Additionally, the more you can provide in terms of reports, alerts, and metrics
about these threats, the more you can raise awareness to the key stakeholders in your company. This will help you get the resources you need as well as broaden your impact inside your organization by conveying leadership in risk management.
Let’s Face It
The life of the SOC analyst is often one of the unsung hero. You’re on the front lines of defending your company’s most valued assets, as well as ensuring that business operations run smoothly. And yet, it can often seem as if the impact you’re having on a daily basis is not as far reaching as you’d like. The SOC team at Brier & Thorn felt the same way before deploying AlienVault USM. Brier & Thorn is a global IT risk management firm that supports companies in their important strategic decisions on operational security, IT risk management, and managed security services.
Brier & Thorn first began searching for an all-in-one security solution in early 2013 when, as a risk management consultancy, they were tasked with conducting an incident response investigation into a spear phishing attack targeting one of their clients. Brier & Thorn attempted to conduct additional research into this attack and the associated communications, but ran into an obstacle. They lacked an incident response forensics tool to see traffic going in and out of the network. They wanted to be able to deploy something quickly that could detect and alert on communication with known malicious hosts, and broaden their impact as a security services provider.
In their search for the right solution, Brier & Thorn came across AlienVault’s Unified Security Management (USM) platform and its Open Threat Exchange (OTX). After a few conversations with AlienVault, Brier & Thorn determined that the functionality provided by the USM platform delivered the ideal tool set for their incident response investigation. Once deployed, AlienVault USM enabled their team to determine the source of the spear phishing attack, which country it was coming from, and which machines on their client’s network had been compromised.
“As soon as we deployed USM (without having to rely on any network IDS signatures at all) OTX began immediately flagging egress traffic from the network to hosts in Russia. We then began further forensics work based on this suspect traffic that allowed us to quickly find and remedy all of the affected hosts in the network.”
– Alissa Knight,
Group Managing Partner at Brier & Thorn
After the investigation, Brier & Thorn were inspired to expand beyond their existing portfolio of risk management consulting services and establish a new managed security services offering. Using AlienVault USM, AlienVault OTX, and the AlienVault Labs Threat Intelligence Subscription, they built their first SOC to support this new offering. And because they serve customers around the world, Brier & Thorn appreciates the fact that AlienVault enables them to federate all of the security events from their customers’ environments into a single console.
Thanks to AlienVault, they’ve broadened their impact for their clients, and established a brand new line of business.
Whether you’re a consultant looking to broaden your impact for your clients, or a SOC analyst looking to broaden your impact internally, AlienVault provides the full and unified view of cyber security you need for operational tactics as well as strategic success.
Key Takeaways & Next Steps
- When you’re looking to broaden your impact internally, AlienVault provides the visibility, reporting, and emerging threat data you need to have strategic success as well as operational efficiency.
- Learn more about the Brier & Thorn case study.
- Apply to become an AlienVault-certified MSSP partner.
- Find an MSSP in your area who uses AlienVault.
Next Steps: Play, Share, Enjoy!