Security log analysis & management
Automated security log analysis and management in AlienVault Unified Security Management (USM) simplifies threat detection and delivers actionable results.
Accelerate Log Analysis to Pinpoint Threats and Simplify Log Management
One of the most overlooked and underutilized tools that you can use to secure your cloud, hybrid cloud, and on-premises is security log analysis. You can almost always find evidence of an attack in the logs of your devices, systems, and applications. However, if you are not performing regular log monitoring and security analysis, many threats may go unnoticed.
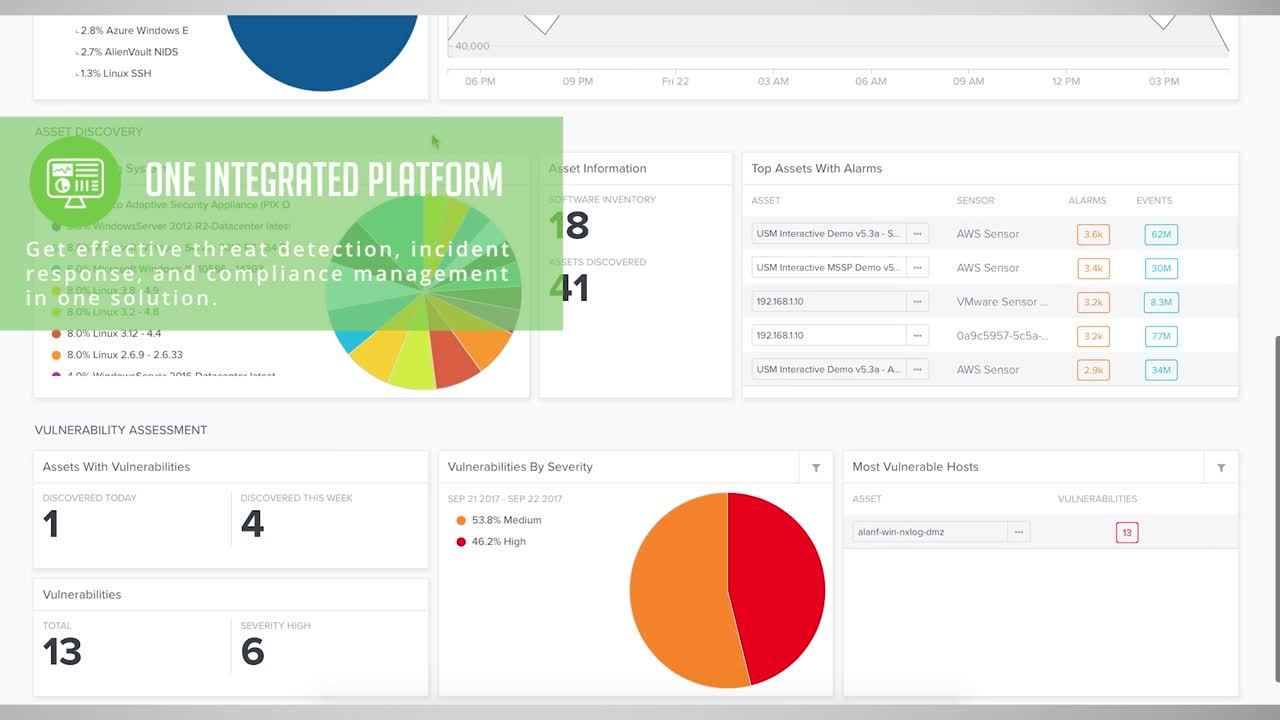
One of the core capabilities of AlienVault® USM™ is its ability to automatically aggregate and manage event log data from its built-in detection capabilities as well as collect logs produced by other devices in your environment. USM monitors the data and automatically executes advanced analysis, producing normalized events and correlating them to produce actionable intelligence, and alerts you to any threats facing your environment.
USM collects log data from across your cloud, hybrid cloud, and on-premises environments, such as:
- Azure cloud access logs: Insights
- AWS cloud access logs: CloudTrail, S3, ELB
- AWS VPC Flow monitoring
- Asset access logs
- Audit logs
- VMware & Hyper-V access logs
- System logs on Windows, Linux, and Unix servers Network device logs
With AlienVault USM, you get all the features and functionality you expect from security log analysis and management including:
Event Correlation with Regularly Updated Threat Intelligence
- Integrated SIEM functionality automatically correlates log data from different data sources
- Regular updates to threat intelligence automatically spots the latest threats
Security Log Analysis Simplified with Intuitive UI and Extensible Architecture
- Advanced search and analytics enable fast, accurate forensic threat assessment
- Hundreds of plugins included to parse logs from the most common data sources
Multifunctional Security Log Management and Storage
- Granular visibility into raw logs with query-based search functionality; simplifies forensic analysis compliance audits
- Tamper-proof raw log storage ensures integrity and meets compliance requirements
Event Correlation with Regularly Updated Threat Intelligence
Anyone who has had to manually configure a SIEM knows that, while it can be frustrating, getting your environment’s different devices and services to send data to a collection point is not the difficult part of security log management. Most devices, operating systems, and applications have built-in functionality to export data into the syslog format, a widely-used logging standard. In cloud environments, you can use native services like AWS CloudTrail and Azure Insights to collect various cloud logs.
The difficulty is in the actual security log analysis and management of the data you collect. Threat research and analysis is a full-time job in most large IT organizations so, unless you have a team investigating emerging threats and regularly developing intelligence, you’re at a major disadvantage.
One of AlienVault USM’s core capabilities is a powerful SIEM with integrated analysis tools that normalize and correlate event log data to produce actionable threat intelligence. Rather than presenting you with only a list of events for you to search and filter through, AlienVault USM’s automated log analysis and management software can produce alarms to alert you of attacks and other security events occurring in your environment.
You receive regular updates to the advanced event correlation from our in-house team of security experts, the AlienVault Labs Security Research Team. This group of security researchers is constantly on the lookout for new attack methods, traffic patterns, and malware associated with malicious activity. The regular updates to the Threat Intelligence in AlienVault USM include correlation directives, IDS signatures, vulnerability assessment data, knowledge base articles, and reports.
Log Analysis Simplified with Intuitive UI and Extensible Architecture
Different use cases require different approaches to security log analysis and management. For instance, historical analysis of compliance calls for an easy-to-use interface and the ability to filter down to a granular level (e.g., all authentication events involving assets storing cardholder data transpiring during the last three months). Doing this quickly allows for faster analysis and, in turn, the ability to swiftly develop new policies and procedures to address the offending behavior.
One potential challenge that can arise when instrumenting a security log management solution is when parsing and normalizing incoming logs using plugins. While most devices output log data in a standardized format, some logs are structured differently, contain extra pieces of information, or fail to adhere to any known format. Some SIEM security platforms come with a limited set of plugins and do not continually build new plugins as new data sources arise.
By contrast, AlienVault USM ships with hundreds of plugins that are ready to parse log data from today’s most commonly used data sources, meaning you’re able to start monitoring your environment immediately after deployment. These out-of-the-box plugins are compatible with most major devices and applications, including network gear (firewalls, UTM, routers, wireless access points), as well as endpoint protection, web servers, and external detection methods.
The AlienVault USM Plugin library provides source-optimized data collection for a complete range of technologies, making it easy for you to get complete visibility into your entire environment. In addition, AlienVault will build a plugin for most commercially available products upon request at no additional charge.
In USM Anywhere™, AlienApps extend the platform’s core capabilities by integrating with popular third-party security tools, including Cisco Umbrella and McAfee ePO to provide specialized data collection, visualization, and action response orchestration.
Multifunctional Security Log Management and Storage
Some regulatory compliance standards require that you store logs in their raw state for a particular amount of time as well as provide for the export of this data for external analysis. Similarly, some audits (in-house or regulatory), can only be performed via queries to logs in their raw state. While some security log analysis and security log management solutions can certainly ingest these raw logs, very few retain the log data in its original state, or give you the ability to export the data.
By default, USM Anywhere stores all data associated with a customer’s subdomain in cold storage for the life of the active USM Anywhere subscription.