SIEM event correlation
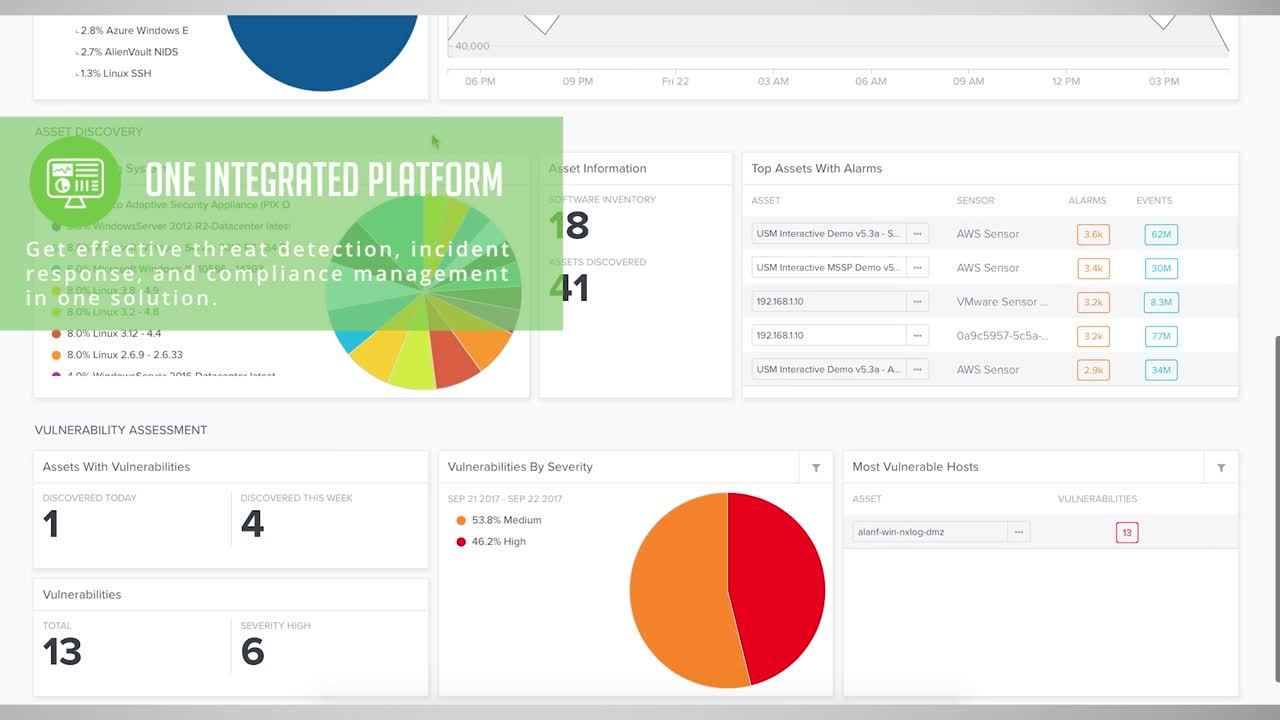
With the power of SIEM event correlation delivered in Unified Security Management™ (USM™), you can easily detect and respond to emerging threats without the complexity of integrating multiple security tools and researching and writing SIEM correlation rules.
SIEM Event Correlation Made Simple
SIEM event correlation is an essential part of any SIEM solution. It aggregates and analyzes log data from across your network applications, systems, and devices, making it possible to discover security threats and malicious patterns of behaviors that otherwise go unnoticed and can lead to compromise or data loss.
However, in traditional SIEM platforms, correlation can get pretty complicated pretty quickly. First, you have to collect all of the relevant security data from your applications, systems, and devices. The most common data sources include your network IDS, vulnerability assessment tool, and your servers. Once you have the data, you then have to research the threats in your environment to understand their behavior and to write correlation rules to identify it.
Writing correlation rules is time consuming and requires a deep understanding of how attackers operate, which is constantly evolving. Just when you think you understand how they operate, attackers shift their tactics, and the rules you’ve created become obsolete and useless. In short, threats are a moving target that never stop changing. It’s no wonder that some of the largest organizations in the world continue to be breached, despite the millions of dollars they spend on security.
USM dismantles the challenges of traditional SIEM correlation so that you can focus your attention on what really matters – keeping your organization secure and in compliance. USM combines the essential security capabilities you need into a single platform, drastically reducing your deployment time and complexity as well as total cost of ownership. The solution leverages the Alien Labs and the Open Threat Exchange™ (OTX™) to deliver event correlation rules and threat intelligence updates straight to your USM environment so that you don’t have to understand every single threat targeting your environment and build correlation rules to detect them.
Save Time and Money with All-in-one Security Essentials
- Alleviate integration headaches with a complete unified security platform
- Easily collect data from third-party applications, systems, and devices to feed the SIEM event correlation
- Start detecting threats immediately with 3000+ correlation rules delivered out of the box
Continuous Threat Intelligence Delivered as Threats Change
- Alien Labs is an extension to your security research team
- Keep pace with attackers with correlation rules and security updates delivered directly from Alien Labs
- Leverage the Open Threat Exchange, the world’s largest open threat intelligence community
Focus on the Threats That Matter Right Now
- Prioritize your response efforts with automated risk assessment and alarm escalation
- Quickly assess your threat exposure with a cyber kill chain prioritization strategy
Save Time and Money with All-in-one Security Essentials
Effective threat investigation and response requires more than a standalone SIEM event correlation product. When an incident happens, you need immediate 360° visibility of the actors, targeted assets, exploitable vulnerabilities on those assets, methods of attack, and more. Log data alone doesn’t provide enough context to make fast, effective decisions.
However, it can be extremely expensive and complex to purchase all of the separate essential security tools you need to get this amount of contextual information and to integrate these products with a traditional SIEM to achieve a holistic view of your threats and vulnerabilities.
By contrast, USM delivers five essential security capabilities - asset discovery, vulnerability assessment, intrusion detection (IDS), behavioral monitoring, and SIEM – all on a single, easy-to-use platform. This significantly reduces the costs and complexity of deploying and managing a security solution, while still providing you with all of the contextual information you need to respond to threats in one place. When threats happen, USM provides every detail you need: what’s being attacked, who is the attacker, what is their objective, and how to respond.
In addition, USM ships with over 3,000 pre-defined SIEM correlation rules, so you don’t have to spend hours creating your own. As the threats change, the threat intelligence is continuously updated to monitor for those changes. With USM, you can launch faster and start detecting existing threats in your environment on day one.
Focus on the Threats That Matter Right Now
It’s not productive—let alone feasible—to investigate every incident and alarm raised in your SIEM. For example, an alarm that’s raised after five failed password attempts in a row could either be the early signs of a brute force attack or someone who accidently left on caps lock while typing his password.
So, how do you decide which alarms to ignore and which ones to focus on right now?
With USM, it’s simple. We prioritize events and sequences of events based on cyber kill chain taxonomy so that you can quickly assess your threat exposure and take action on the activities in the later stages of the cyber kill chain – the highest-priority threats in your environment.
Designing your monitoring and response plan around the cyber kill chain model is an effective method because it focuses on how actual attacks happen, from initial probing to exploitation of your vulnerabilities to compromising your system and stealing resources.
In addition, USM has built-in intelligence to assess the risk of events based on multiple parameters and to escalate alarms and alerts as that risk grows. By cutting through the noise of alarms to help you focus on the threats that matter, USM makes it easier to keep your network environment protected.