USB monitoring alerts you to potential data theft
USB monitoring to detect when users have attached devices to USB ports on their systems is an essential part of many regulatory requirements and IT best practices. AlienVault® Unified Security Management™ (USM™) gives you the visibility you need to detect activity that could be malicious.
Know When Users Are Attaching External Devices to Sensitive Systems
Best practices, industry guidelines, and regulatory requirements in environments with highly controlled data require the ability to detect the attachment of an external device to a system’s USB port. These devices include thumb drives or external storage drives, which insiders can use to physically exfiltrate data to circumvent data leak prevention technologies on your network.
Whether you are protecting cardholder data, electronic health records, classified data or other types of confidential information, you need to know if there is potential for insider abuse.
USB port monitoring is a critical component of your security strategy to reduce the insider threat.
AlienVault USM delivers essential threat detection and compliance capabilities to detect suspicious or malicious behavior of authorized users:
USB Monitoring
- Attachment of a USB device, such as a thumb drive or external storage device
Host Intrusion Detection System (HIDS)
- Privilege escalation as attackers seek “Admin” or “root” access
- File Integrity Monitoring (FIM) for changes to critical files
- Unauthorized user access attempts to systems and applications storing sensitive or regulated data
Continuous Compliance Management
- Continuous monitoring of your network and devices
- Log retention, management, and analysis
- Auditor-ready report templates for HIPAA, PCI DSS, ISO27001, and more
USB Monitoring
Insiders who wish to exfiltrate data from your network will often attach a thumb drive or external storage device to a USB port.
According to the 2016 Verizon Data Breach Report, unauthorized hardware was the third most common form of insider and privilege misuse, and USB devices were the most common method for stealing data.
Insiders can use removable storage devices to avoid detection by network monitoring or data leak prevention technologies. These devices are an easy and effective way to remove gigabytes of data without triggering your network-based technologies.
USM will alert you whenever a user inserts a device into a USB port on a system you’re monitoring. USM delivers essential awareness to detect potentially unauthorized activity that can lead to data theft.
Host Intrusion Detection System (HIDS)
Host intrusion detection gives you the visibility you need into the status of critical systems and services on individual hosts to detect malicious activity by insiders. This activity includes privilege escalations, modification of configuration files, and attempts to access to in-scope systems and data.
In addition to providing USB device monitoring, AlienVault USM can alert you to malicious activity before you suffer data loss. Because you install Host IDS on individual systems, AlienVault HIDS is able to examine operating system log files to detect any changes to system files and software.
AlienVault HIDS is also able to detect the installation of rootkits, ransomware, and other malware on your critical servers and workstations. It is an essential component to helping you meet compliance requirements for system monitoring, such as for PCI DSS, GPG13, or HIPAA/HITECH.
Continuous Compliance Management
Compliance management is extremely complex. To simplify your compliance efforts, you need to be able to consolidate and automate your critical security controls.
The AlienVault USM platform delivers a single solution that automatically identifies audit events, generates alarms on those events that require immediate attention, and provides reports that satisfy your auditor. Regardless of the specific compliance requirements or guidelines, AlienVault USM offers you a complete solution to help you demonstrate compliance by continuously monitoring your network and devices.
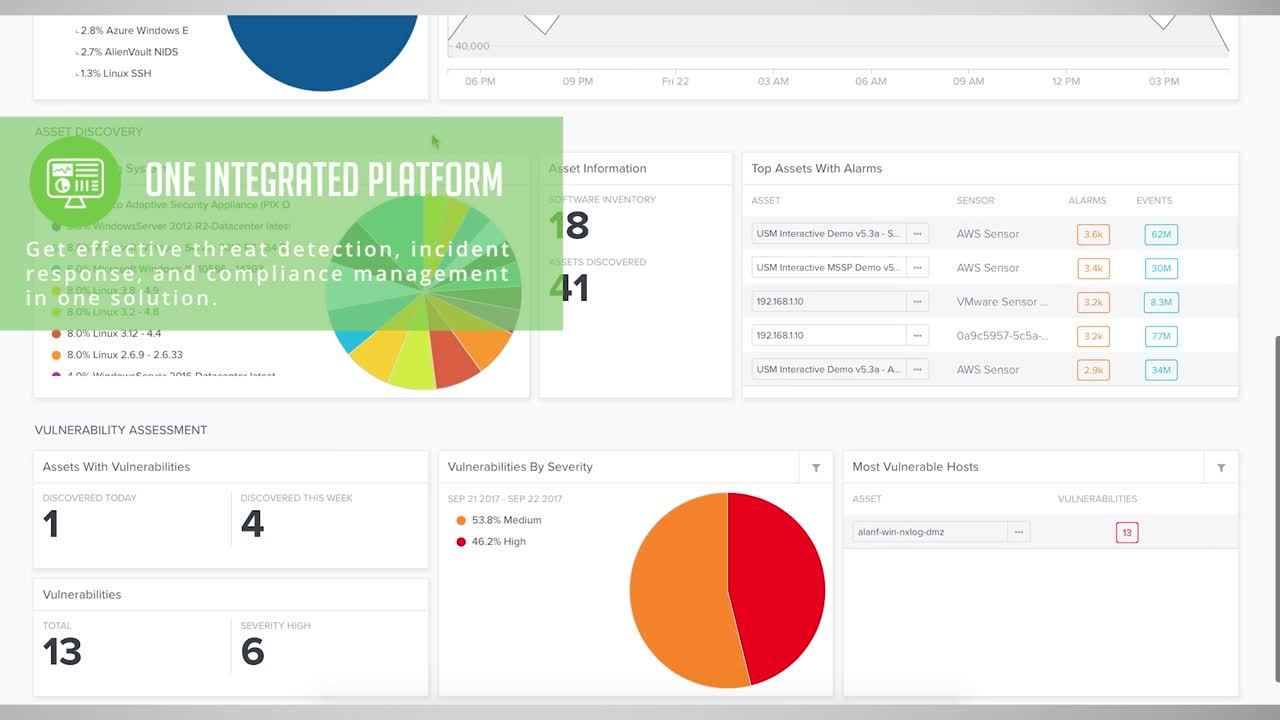
The USM platform builds in essential capabilities for compliance management: Asset Discovery, Vulnerability Assessment, Host and Network Intrusion Detection, File Integrity Monitoring (FIM) and Security Information and Event Management (SIEM), all in a single platform and managed from a single console. The regularly updated threat intelligence delivered by AlienVault Labs eliminates the need for you to spend precious time conducting your own research on emerging threats, instrumenting your security controls, or creating your own correlation directives.
AlienVault USM quickly delivers the insight you need to understand the location and compliance status of critical assets, and changes to access privileges, files, and services on those assets. The AlienVault USM platform offers an extensive library of customizable reports for documenting your compliance.
The AlienVault USM platform puts up-to-the-minute security and threat information about systems, data, and users at your fingertips, giving you complete security visibility and provides you with a unified threat detection and compliance management solution that is both easy-to-use and affordable.