Executive Summary
The “Security Alert” scam is a prevalent tech-support fraud that threatens both Windows and Apple users. It exploits the trust of users by masquerading as an official support site, using fake pop-up warnings to lure users into dialing scam phone numbers by conveying a sense of urgency. The ultimate goal is gaining remote access to the user’s system and pilfering personal data to extort money.
Combating a “Security Alert” scam is difficult on many fronts because most of the time attackers leverage newly registered domains, which means there is a lack of malicious OSINT (open-source intelligence), and they are able to bypass traditional detection methods. To gain remote access, attackers need the end user to call into a fraudulent support team to install a Remote Desktop Protocol (RDP) tool. An endpoint detection and response (EDR) tool might not catch the initial intrusion as such tools are also used for legitimate business reasons. The most successful way to combat phishing/scams is by end-user education and communication with the IT department.
In a recent incident, a fake “Microsoft Security Alert” domain targeted one of our Managed Endpoint Security with SentinelOne customers, causing alarm for the end users and IT staff, but fortunately, the end user did not fall into the trap of calling the fraudulent number.
The customer immediately contacted their assigned Threat Hunter for support and guidance, and the Threat Hunter was able to quickly utilize the security measures in place, locate multiple domains, and report them to the Alien Labs threat intelligence team.
AT&T Cybersecurity was one of the first cybersecurity companies to alert on the domains and share the information via the Open Threat Exchange (OTX) threat intelligence sharing community, helping other organizations protect against it.
Investigation
Initial Alarm Review
Indicators of Compromise (IOCs)
The initial security layers failed to raise alarms for several reasons. First, the firewalls did not block the domain because it was newly registered and therefore not yet on any known block lists. Second, the platform did not create any alarms because the domain’s SSL certificates were properly configured. Finally, the EDR tool did not alert because no downloads were initiated from the website. The first indication of an issue came from an end user who feared a hack and reported it to the internal IT team.
Utilizing the information provided by the end user, the Threat Hunter was able to locate the user's asset. Sniffing the URL data revealed a deceptive “Microsoft Security Alert” domain and a counterfeit McAfee website. These were detected largely because of improvements recommended during the customer's monthly meetings with the Threat Hunter, including a recommendation to activate the SentinelOne Deep Visibility browser extension, which is the tool that was instrumental in capturing URL information with greater accuracy after all the redirects.
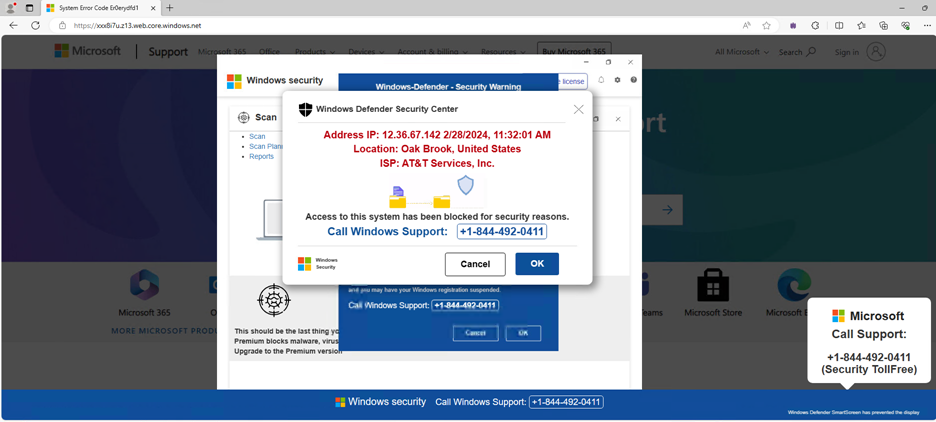
Figure I – Fake Microsoft Support page
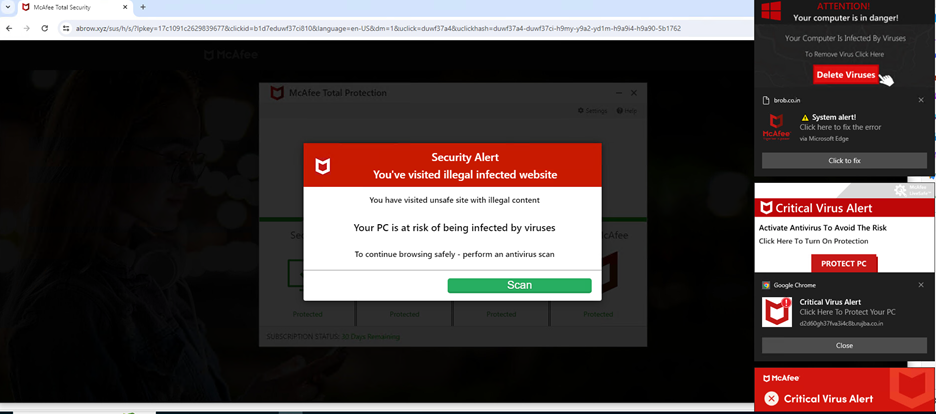
Figure 2 – Fake McAfee page
Artifact (Indicator of Compromise) IOC Fake McAfee Page bavareafastrak[.]org Website Hosting Scam Pages Galaxytracke[.]com Zip file hash Tizer.zip - 43fb8fb69d5cbb8d8651af075059a8d96735a0d5
Figure 3 – Indicators of compromise
Expanded Investigation
Events Search
With the understanding that the endpoint must have accessed a website featuring the fraudulent support page, the search for the event was streamlined to focus on URL requests within a specific time frame. To filter out unnecessary noise, it was necessary to temporarily exclude authentic domains that are associated with commonly used tools within the organization. Once the threat hunter fine-tuned their search parameters, it took a keen eye and leveraging a sandbox environment to find the domain related to the fraudulent support page that the end user had encountered. This threat hunt uncovered a second domain that was posing as a fake McAfee page within the same time frame.
Event Deep-Dive
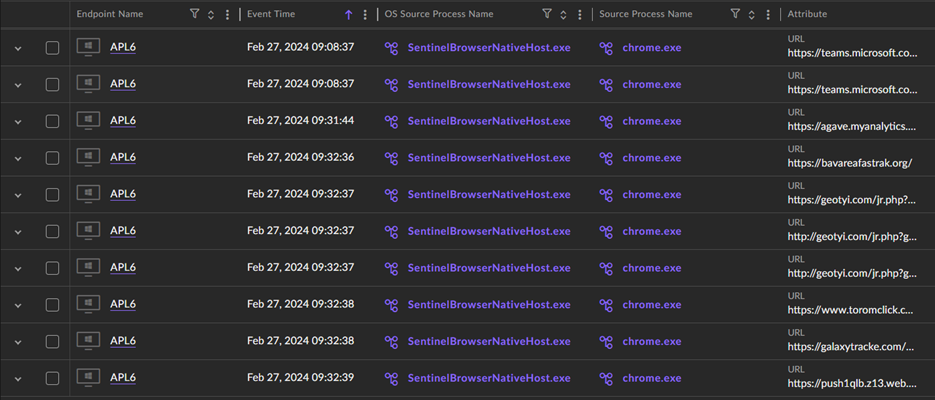
While OSINT searches yielded limited information, the Threat Hunter could manually explore the website to gain a better understanding of its operations. However, before doing this, it was critical to understand how the user had arrived at the website. Using SentinelOne Storyline technology, the Threat Hunter could correlate the sequence of events leading up to the website visit. They deduced that the user likely visited the site through a link shared on the Microsoft Teams web app, which redirected the user to the fraudulent support page via a clickable ad.
Figure 4 – SentinelOne Deep Visibility findings
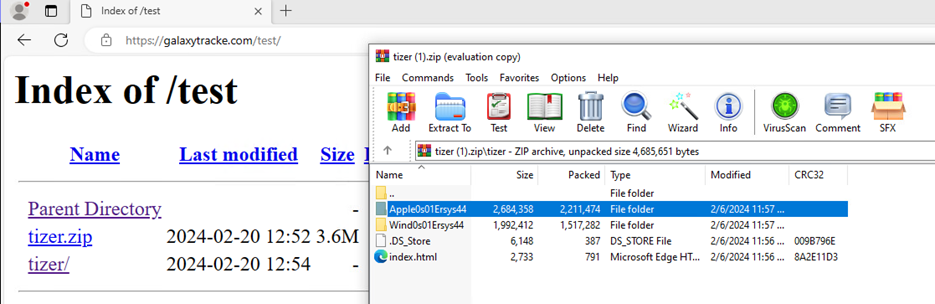
Fortunately, SentinelOne was able to capture the main domain before the user was redirected to the landing page. Utilizing virtual machines as a safety precaution, the Threat Hunter was able to visit the domain where they discovered it was hosting multiple directories, some of which contained HTML code that was used to construct the fraudulent support page. Interestingly, some directories contained .zip files that held HTML files for other types of fraudulent support pages, such as Apple, complete with all the images and sounds necessary to create the pages.
Figure 5 – Website hosting fake “Security Alert” sites
Reviewing for Additional Indicators
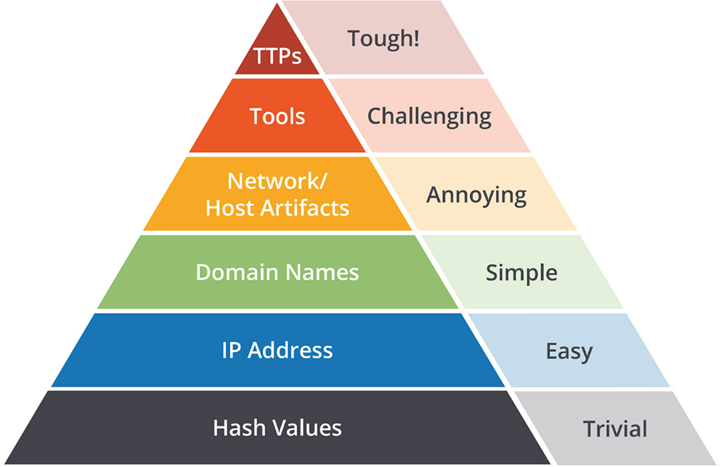
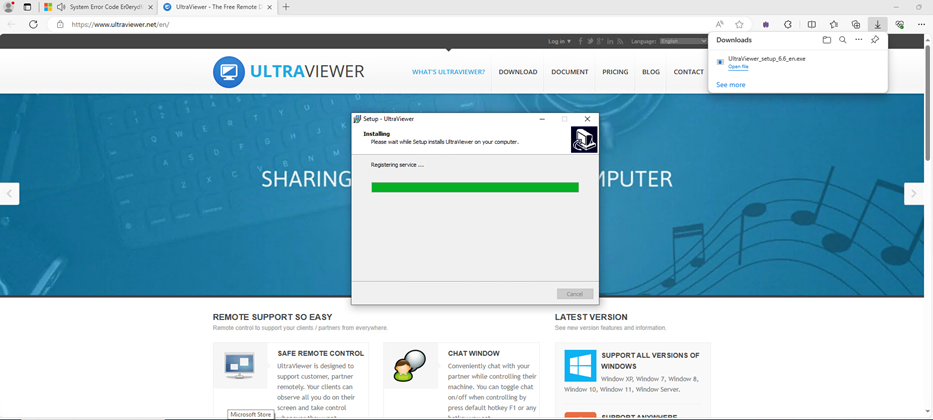
If we review the Pyramid of Pain, which is a conceptual model that categorizes IOCs and attacker tactics, techniques, and procedures (TTPs) according to how difficult they are for attackers to change, we see that domain names are the third-lowest layer. But how does the attacker move up the Pyramid? By giving end users a fraudulent support page to call! Domains will change daily, but one TTP that attackers will always need is gaining access to the machine. In this case, it was by having the Threat Hunter download the UltraViewer RDP tool.
Figure 6 – Pyramid of Pain
Thanks to SentinelOne’s app inventory capabilities, by correlating a successful URL event match with the installation of this tool, we can gauge the extent to which the end user may have fallen prey to the scam. We also reviewed our fleet of managed customers and found no installations of the UltraViewer tool that would indicate a user had been successfully compromised.
Figure 7 – Download of UltraViewer assisted by scammer
Combating Adversaries
Our Alien Labs threat intelligence team promptly added the two domains we identified to an OTX pulse, which enables us to alert on any assets that visit these websites. We recommend that our customers conduct ongoing training with end users to help prevent them from falling victim to the latest scams. Additionally, the malicious domains detected should be blocked at the firewall. Although the threat actors behind these websites have changed their display, the domains remain active. They will continue to be monitored on OTX because of their past activity and potential future use.
Blocking IOCs is only one component of a cybersecurity strategy. And this is why, during monthly calls with our Managed Endpoint Security with SentinelOne customers, we not only discuss the results of our latest threat hunts but also review applications installed in their environments. We provide guidance on how to enhance visibility in their environments, and one way to do this is by activating the SentinelOne Deep Visibility extension, which can significantly improve the tracking of URL events, such as those that occurred in this incident.
| Artifact | (Indicator of Compromise) IOC |
|---|---|
| Fake McAfee Page | bavareafastrak[.]org |
|
Website Hosting Scam Pages |
Galaxytracke[.]com |
| Zip file hash | Tizer.zip - 43fb8fb69d5cbb8d8651af075059a8d96735a0d5 |