As organizations grow and more endpoints are added across the enterprise, they create an increasingly broad attack surface sophisticated attackers are looking to compromise. According to the 2019 Endpoint Security Trends Report 70% of breaches originate at the endpoint¹. That is likely because endpoints typically represent the Intersection between humans and machines creating vulnerable points of entry for cybercriminals. This is why it is increasingly important to secure your endpoints.
Growth in endpoints
An endpoint is defined as any computing device that communicates back and forth with a network to which it is connected. Some end user devices serve as an interface with human users while others are servers that communicate with other endpoints on the network. Traditional endpoints began as physical devices including servers, workstations, desktops, and laptops, all connected to a corporate network. When smartphones and tablets became handheld computing devices with access to corporate email, document sharing and collaboration tools the number of endpoints at least doubled.
Then came the rise of the Internet of Things (IoT) including devices like printers, webcams, smartwatches, and thermostats, all of which are connected to the network. Industries like healthcare and manufacturing are using millions of IoT sensors to collect and exchange data. This continued growth in IoT only increases the number of endpoints that need to be protected.
Another contribution to the growth in endpoints is the migration to the cloud. It is estimated that 67% of enterprise infrastructure is cloud-based². This cloud transformation is the evolution from physical devices to virtualization and containerization.
Endpoint virtualization
The cloud is a multi-tenant environment where multiple users run services on the same server hardware. Virtualization and containerization are both virtualization technologies that separate the host operating system from the programs that run in them.
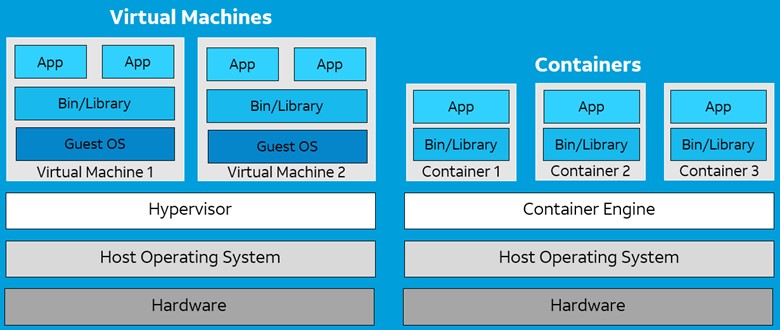
Virtualization is achieved using a hypervisor, which splits CPU, RAM, and storage resources between multiple virtual machines (VMs). Each VM behaves like a separate computer that gets a guest operating system and each VM is independent of each other. This allows organizations to run multiple OS instances on a single server.
Containerization, on the other hand, runs a single host OS instance and uses a container engine to help package applications into container images that can be easily deployed and re-used. By splitting each individual application function or microservice into containers they can operate independently to improve enterprise resilience and scalability. Kubernetes then manages the orchestration of multiple containers. VMs and containers present very different security challenges so let’s look at the evolution of endpoint security and the solutions that meet the needs of complex customer environments.
Securing endpoints
For decades, organizations have heavily relied on antivirus (AV) software to secure endpoints. However, traditional antivirus worked by matching known malicious signatures in a database and can no longer protect against today’s sophisticated threats. Modern endpoint security solutions are less signature-based and much more behavior-based. Endpoint protection platforms (EPP) offer cloud native architectures that provide a layered defense against fileless attacks using machine learning and behavioral AI to protect against malicious activity. Endpoint detection and response (EDR) solutions went beyond protection by recording and storing endpoint-system level behaviors to detect malicious threats.
EDR solutions use data analytics combined with threat intelligence feeds to provide incident responders with the forensic data for completing investigations and threat hunting. In addition to blocking malicious activity and containing the incident EDR solutions enable businesses to respond and remediate threats. Endpoint security continues to evolve with features including IoT discovery and solutions to protect mobile devices.
Mobile security is one of, if not the single most important facet of enterprise security being overlooked today. Mobile threat defense (MTD) prevents or detects threats on mobile devices across the web, applications, the device, and the network. Phishing is the most common mobile threat and phishing protection keeps users safe from being lured to malicious websites where attackers deliver malicious downloads or inject code onto a device.
App analysis uses various techniques including anti-malware filtering, code emulation, application reverse engineering, and dynamic app security testing to detect malware or risky apps that could expose sensitive data. Device vulnerabilities or privilege escalations are identified by monitoring OS versions, system parameters, device configurations, and system libraries. MTD also analyzes network connections to detect a compromised Wi-Fi network for malicious behavior or checking for invalid certificates to prevent man-in-the-middle attacks. Mobile security is not just a “nice to have” solution but becoming more of a “must have” solution, which is also becoming the case for cloud security.
Cloud workload protection platform (CWPP) provides visibility and protection for a range of workloads including virtual machines, virtual servers, and containers in Kubernetes clusters. CWPP detects runtime threats at the VM and container level, providing visibility and the cloud metadata needed for incident response. These platforms can improve efficiency by providing analytics and reporting which enable cloud engineers to optimize and scale application capacity based on demand.
Integrating CWPP with cloud security posture management (CSPM) solutions provides broader visibility while integration with the DevOps CI/CD pipeline build process helps protect machines throughout the software lifecycle. CWPP protects sensitive data using controls like data encryption, which often helps organizations meet some compliance and regulation standards. Flexibility and scalability are important considerations when selecting a CWPP to support an organization’s current and future cloud infrastructure including public, private, and hybrid cloud environments.
As technology advances and the number of endpoints grow so does the potential attack surface for cybercriminals to exploit. These transformations will compel endpoint security vendors to continue delivering innovative solutions in the future.
¹Absolute | 2019 Endpoint Security Trends Report
²SaaSworthy | Cloud Computing Statistics in 2023

