PCI DSS compliance solutions
Simplify and accelerate PCI DSS compliance with one powerful product.
Have you started your planning around PCI DSS 4.0?
PCI DSS Compliance
Introduction to PCI DSS for new clients:
As part of our Cybersecurity consulting services, AT&T can provide PCI-trained Qualified Security Assessors (QSAs) to assist with either new PCI assessments or PCI DSS 4.0 transition planning and assessments.
If you are new to the world of credit card security, please watch this introduction to what compliance with the data security standard looks like from a practical standpoint. A longtime assessor explains how the requirements translate into what gets assessed and how your implementation teams can best prepare for an assessment.
PCI DSS 4.0 Transition Introduction for Management
This is an in-depth video for clients who are currently compliant with version 3.2.1 of the PCI DSS standard and want to know more about their transition to compliance with version 4.0. Many entities are under the misapprehension that compliance is not mandatory until March 31st, 2025. In fact PCI DSS 4.0 compliance commences with the use of new reporting documents on March 31st 2024. PCI 4.0 affects virtually all entities in some fashion, even those using SAQs, so if you haven’t started your transition yet, this presentation will show some of the reasons why we encourage all entities to start their transition planning sooner rather than later. In many cases the change documentation produced by PCI obscures the complexity of the new requirements. Therefore, this presentation helps Compliance Management understand why additional budget, staffing, and tooling may be necessary for the transition program, and helps Project Managers understand some of the implementation details they can expect in a PCI DSS 4.0 Assessment.
A Faster, Easier Path to PCI DSS Compliance
PCI DSS compliance software is a must-have for any organization that handles credit card data or other types of payment card data. Failure to comply can result in PCI DSS penalties and fines imposed daily, and a data breach resulting from non-compliance could cost millions in settlements, legal fees, and loss of reputation.
Yet, many IT security teams struggle to meet the many security technology requirements defined by PCI DSS 3.2. It can be difficult to know which security tools you need to achieve PCI DSS compliance. It doesn’t help that organizations are often racing to get ready for their next, fast-approaching PCI audit.
AlienVault® Unified Security Management™ (USM) delivers everything you need to get ready for your next PCI DSS audit in one affordable, easy-to-use solution. It combines the essential security technologies you need to demonstrate compliance, including asset discovery, vulnerability assessment, log management, file integrity monitoring, and others. It also provides predefined compliance reports out of the box and automatic threat intelligence updates, helping you to stay in compliance with continuous security monitoring.
Unlike other PCI compliance software, it can take as little as one day to fully deploy the AlienVault USM platform for compliance management. You can centralize monitoring of all your on-premises, AWS or Azure cloud, and cloud applications, helping you to achieve PCI DSS compliance faster and ensure continuous security and compliance monitoring of all your environments. The AlienVault USM platform is also certified as PCI DSS compliant, giving you the assurance you need in a security monitoring platform for cloud, on-premises, and hybrid environments.
The AlienVault USM platform delivers multiple security essentials to help you to prepare for your next PCI audit faster and more easily.
Multiple PCI DSS Compliance Must-Haves in One Solution
- Asset Discovery and Inventory
- Vulnerability Assessment
- Intrusion Detection (IDS)
- File Integrity Monitoring (FIM)
- SIEM Event Correlation
- Log Management & Monitoring
- PCI DSS Compliance Reporting
Report on the Most Challenging PCI DSS Requirements
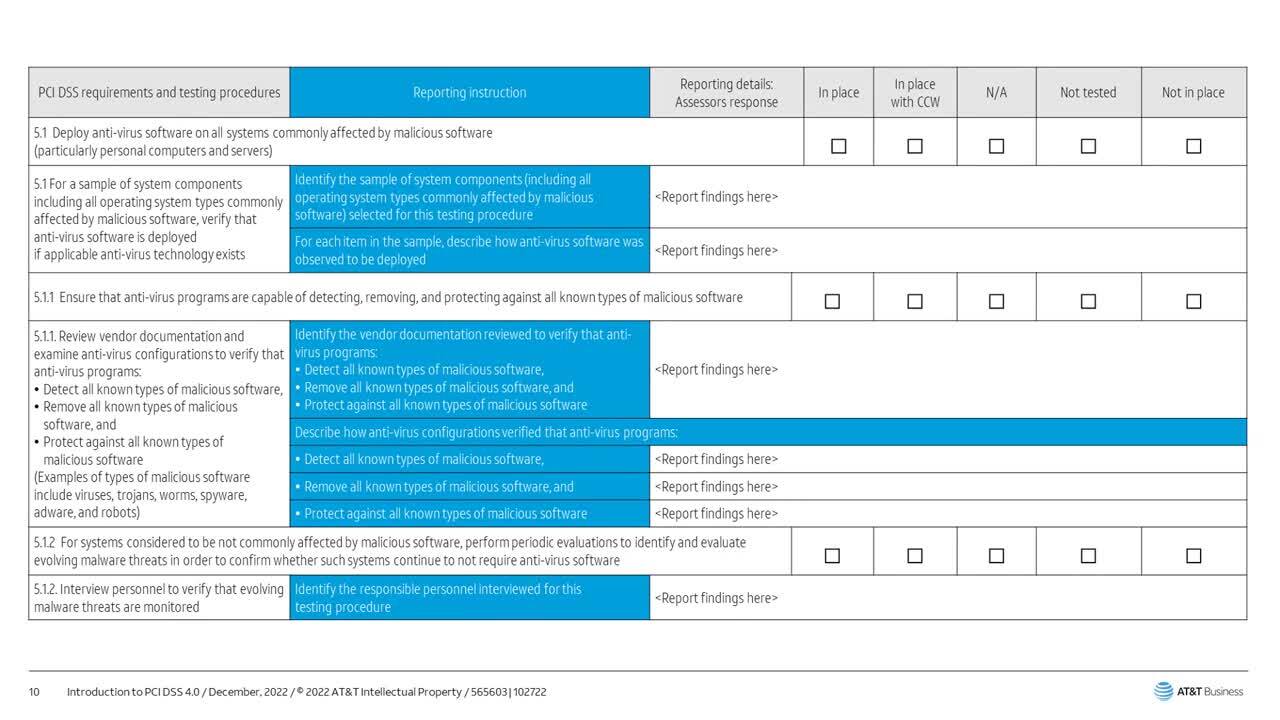
- PCI Requirement 5: Protect all systems against malware
- PCI Requirement 6: Develop and maintain secure systems and applications
- PCI Requirement 10: Track and monitor all access to network resources and cardholder data
- PCI Requirement 11: Run vulnerability scans at least quarterly, and after any significant change in your network
- PCI Requirement 12: Implement an Incident Response Plan
Address multiple PCI DSS compliance objectives with one powerful tool
The AlienVault USM platform delivers all of the following essential security capabilities in one unified solution for security and compliance management.
Asset Discovery & Inventory
PCI DSS requires you to identify all systems that are in scope of your cardholder data environment (CDE). The AlienVault USM platform automatically discovers and inventories all your critical on-premises and cloud assets. You can define custom PCI asset groups that you can use to run vulnerability scans and reports.
Learn more about asset discovery & inventory >
Vulnerability Assessment
A key PCI DSS Control Objective is to 'Maintain a Vulnerability Management Program,' and vulnerability scans are called out in several PCI DSS requirements. The USM platform includes partial, non-customizable file integrity monitoring software (FIM).
Learn more about PCI DSS Internal Vulnerability Scanning >
Intrusion Detection
Another PCI requirement is to implement an intrusion detection system (IDS) to monitor traffic at the perimeter of your CDE and at critical points within the CDE. AlienVault takes a multi-layered approach to intrusion detection, providing out-of-the-box network intrusion detection (NIDS), host intrusion detection (HIDS), and cloud intrusion detection.
SIEM Event Correlation
SIEM event correlation in USM captures all user activities on critical systems, as well as collection and correlation of valid and invalid authentication attempts, so you always know who is trying to access your CDE.
Learn more about SIEM Event Correlation in USM >
Log Management & Monitoring
Log management, monitoring, and retention are pillars of the AlienVault USM platform. It collects, parses, and analyzes log data from your PCI systems, alerting you to any threats facing your environment and helping you to demonstrate compliance of PCI Requirement 10.
Learn more about PCI DSS Log Monitoring & Management >
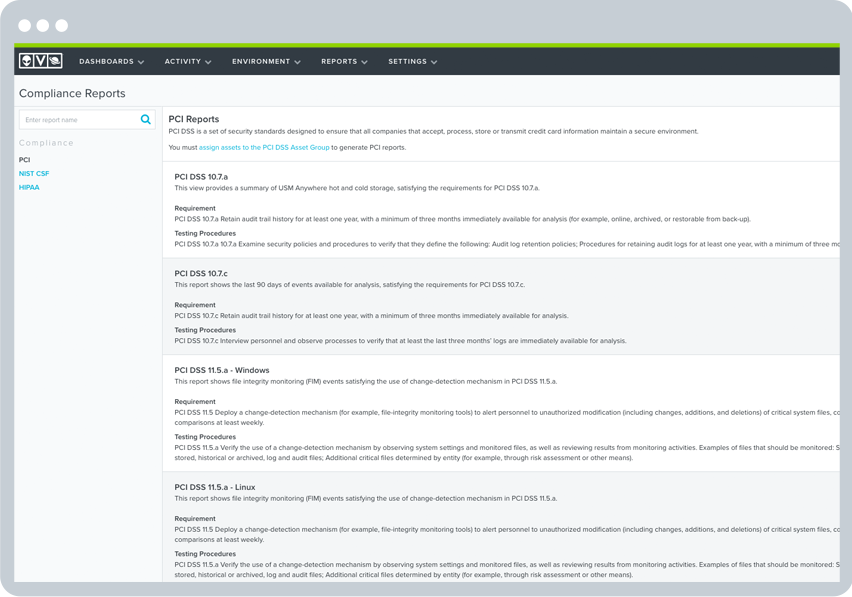
PCI DSS Compliance Reporting
The reporting features in the AlienVault USM platform make it simple and fast to get the visibility you need to demonstrate compliance to an auditor and to maintain continuous security monitoring afterwards. The platform delivers predefined PCI DSS reports out of the box that map directly to common PCI DSS requirements. You can easily customize any of the predefined compliance reports to tailor it to an auditor’s specific request.
File Integrity Monitoring
File Integrity Monitoring is called out as a best practice control across several PCI DSS requirements, and is deemed necessary to pass your audit. That’s because changes on critical servers often signal a breach, or a change that could open your system to compromise. The USM platform includes partial, non-customizable file integrity monitoring software (FIM).
Support for Even the Most Challenging PCI DSS Requirements
Malware Protection: PCI DSS Requirement 5
The AlienVault USM platform helps you identify systems susceptible to known vulnerabilities, or that may not have antivirus software installed or operational. Its network, host, and cloud intrusion detection capabilities monitor for indicators of malware-based compromise. When malware is detected, the AlienVault USM platform enables the orchestration of manual or automated responses to isolate infected systems and block malicious domains.
Vulnerability Assessment: PCI DSS Requirements 6 and 11
Out of the box, the AlienVault USM platform provides vulnerability assessment that enables you to find and fix weak spots in your cloud and on-premises environments. Together, AlienVault USM’s asset discovery and vulnerability scanning tools simplify security visibility by unifying the data gathered in asset and vulnerability scans with known vulnerability information. Built-in file integrity monitoring alerts users to changes to critical files that may indicate a breach.
Incident Response Planning: PCI DSS Requirement 12
When an incident happens, make sure the correct response actions happen and that the right people get notified quickly and efficiently. The AlienVault USM platform provides the alerting and notifications you need to stay informed of your security posture 24 x 7 as well as all the relevant security data you need in one location to respond quickly and to mitigate the potential damage of a breach.
In addition, it delivers advanced security orchestration and automated incident response capabilities as a first line of defense. When an incident occurs, orchestration rules can be automatically triggered to take some action to gather additional data to help expedite your investigation and response activities.
Logging and Reporting: PCI DSS Requirement 10
The AlienVault USM platform helps you collect and protect your log records, as well as prove that you’ve done so.
PCI Requirements 10.1 - 10.4 deal with collecting audit logs, tracking access to cardholder systems and data (including failed logon attempts), monitoring actions taken by admins, and identifying any manipulation of audit logs.
The AlienVault USM platform collects log data from your applications, systems, devices, and cloud accounts. The data is parsed and immediately available to search on and run reports to evaluate what actions individual users are taking in your CDE. The AlienVault USM platform timestamps the data, which addresses section 10.4.
Requirement 10.5 requires that audit trails be secured so they cannot be altered.
The AlienVault USM platform supports a “write once, read many” (WORM) approach to prevent raw log data from being modified once they’re written to cold storage.
Requirement 10.6 mandates that you review logs and security events to identify anomalies or suspicious activity.
The AlienVault USM platform aggregates events from your applications, servers, and devices from across your on-premises and cloud environments. Customizable views, built-in and customizable PCI DSS reports, and advanced correlation capabilities simplify the ability to review data, and enable you to regularly monitor for and report out on threats and anomalies.
Requirement 10.7 mandates that you retain audit history for at least one year, with a minimum of three months immediately available for analysis.
The USM platform stores data online for 90 days, so you can easily search and report on it per PCI compliance needs. It also provides long term storage for the life of the active USM Anywhere subscription.

Discover How AlienVault USM Supports
PCI DSS Requirements
PCI Requirement
PCI Sections AlienVault USM Addresses
How AlienVault USM Helps
1. Install and maintain a firewall configuration to protect cardholder data.
1.1, 1.2, 1.3
- Built-in asset discovery provides a dynamically updated inventory of assets across your cardholder data environment, ensuring only authorized endpoints are deployed.
- Capture events relating to configuration changes on firewalls and routers, including when user accounts get updated.
- Discover unauthorized communications, such as between untrusted networks and systems within the cardholder data environment.
2. Do not use vendor-supplied defaults for system password and other security parameters.
2.1, 2.2, 2.3, 2.4, 2.6
- Identify use of default system accounts on Windows machines.
- Non-customizable File Integrity Monitoring can detect changes to predetermined paths in Windows and Linux systems.
- Identify vulnerabilities such as where an application may have a cryptographic algorithm vulnerability and recommend if patches or workarounds are available.
- Help identify specific services, ports, systems, and users
- Built-in asset discovery provides a dynamically updated inventory of what systems are operational in your environment, and what software is running on each.
- Discover and monitor assets running on-premises and in cloud environments (including Azure, VMware, Hyper-V, AWS, GCP)
3. Protect stored cardholder data
3.6, 3.7
- Monitor for changes to Office 365 policies, including data loss prevention (DLP), information management, and more.
- File Integrity Monitoring can detect when SSH or similar cryptographic keys are modified.
- Unified log review and analysis, with triggered alarms for high-risk systems.
4. Encrypt transmission of cardholder data across open, public networks
4.1, 4.3
- Identify when network traffic goes to unauthorized networks.
- Identify systems using compromised or insecure protocols that may increase their risk of being attacked.
- Monitor for changes to Office 365 policies, including Information Management and more.
5. Protect all systems against malware and regularly update antivirus software or programs
5.1, 5.2, 5.3, 5.4
- Identify systems susceptible to known vulnerabilities, or that may not have antivirus installed and/or operational.
- Identify for indicators of malware-based compromise, and orchestrate manual and automated actions to isolate infected systems and block malicious domains.
- Monitor and store events from antivirus solutions that could indicate a compromise, or attempt to disable antivirus software.
- Monitor for changes to Office 365 policies, including Information Management and more.
6. Develop and maintain secure systems and applications
6.1, 6.2
- Identify systems susceptible to known vulnerabilities, with systems ranked as 'high,' 'medium,' and 'low' risk vulnerabilities.
- Identify patches or workarounds available to vulnerable systems.
7. Restrict access to cardholder data by business need to know
7.1, 7.3
- Identify attempts to access systems using privileged accounts.
- Identify escalation of privilege attempts.
- Monitor for changes to Office 365 policies, including Information Management and more.
8. Identify and authenticate access to system components
8.1, 8.2, 8.5
- Aggregate logs and events from systems, applications, and devices from across your on-premises and cloud environments.
- Identify attempts to use retired or default user credentials.
- Monitor and alarm on Group Policy errors.
9. Restrict physical access to cardholder data
N/A
- Not applicable.
10. Track and monitor all access to network resources and cardholder data
10.1, 10.2, 10.3, 10.4, 10.5, 10.6, 10.7, 10.8
- Aggregate, analyze, and archive logs and events from systems, applications, and devices from across your on-premises and cloud environments.
- Identify logon success and failures.
- Identify privilege escalation attempts.
- Identify where systems are out of sync with the current time and/or Domain Controller, or for non-typical traffic on port 123.
- Identify unauthorized attempts to access or modify key logs.
- Identify where security tools, such as antivirus and firewalls, have been disabled or have failed to start.
- Captures all user account creation and modification activities.
11. Regularly test security systems and processes
11.1, 11.2, 11.4, 11.5, 11.6
- Assess systems for vulnerabilities, and where found rank them as 'high', 'medium,' and 'low' risk.
- Monitor access to and attempt to modify system and application binaries, configuration files, and log files.
- Monitor user and administrator activities in cloud environments such as Azure and AWS, and within cloud applications such as Office 365.
- Apply labels to alarms.
- Generate incident tickets within popular solutions like ServiceNow, directly from within the USM Anywhere console.
12. Maintain a policy that addresses information security for all personnel
12.1, 12.5, 12.8
- Monitor for changes to Office 365 policies, including Data Leakage Protection (DLP), information management, and more.
- Monitor all administrative activities through popular authentication and authorization solutions like Azure Active Directory.
- Monitor network traffic for violations of policy, such as communications that cross your cardholder data environment perimeters.





