Intrusion detection system (IDS) software
Intrusion detection plus everything you need to detect and respond to threats.
Accelerate Threat Detection with Intrusion Detection Systems
Unified Security Management® (USM) offers a built-in intrusion detection software as part of an all-in-one unified security management console. It includes built-in host intrusion detection (HIDS), network intrusion detection (NIDS), as well as cloud intrusion detection for public cloud environments including AWS and Microsoft Azure, enabling you to detect threats as they emerge in your critical cloud and on-premises infrastructure.
To ensure that you are always equipped to detect the latest emerging threats, Alien Labs Security Research Team delivers continuous threat intelligence updates directly to the USM platform. This threat data is backed by the Open Threat Exchange® (OTX™)—the world’s first open threat intelligence community.
- Leverage intrusion detection for any environment with built-in cloud IDS, network IDS, and host-based IDS.
- Use the Kill Chain Taxonomy to quickly assess threat intent and strategy
- Make informed decisions with contextual data about attacks, including a description of the threat, its method and strategy, and recommendations on response
- Use automatic notifications so you can be informed of key threats as they happen
- Work more efficiently with powerful analytics that uncover threat and vulnerability details - all in one console
Multiple Types of Intrusion Detection Systems for Any Environment
USM enables early intrusion detection and response with built-in cloud intrusion detection, network intrusion detection (NIDS), and host intrusion detection (HIDS) systems. These tools monitor your traffic and hosts, along with user and administrator activities, looking for anomalous behaviors and known attack patterns. The built-in SIEM capability in the USM platform automatically correlates IDS data with other security information to give you complete visibility of your security posture.
Intrusion Detection in the Cloud
While traditional IDS and intrusion prevention (IPS) software is not optimized for public cloud environments, intrusion detection remains an essential part of your cloud security monitoring. That’s why USM Anywhere™ provides native cloud intrusion detection system capabilities in AWS and Azure cloud environments. In USM Anywhere, cloud sensors purpose-built for AWS and Azure cloud environments leverage the management APIs of AWS and Azure, giving you full visibility into every operation that happens in your cloud accounts.
Network Intrusion Detection System (NIDS)
The network intrusion detection system (NIDS) capability of the USM platform detects known threats and attack patterns targeting your vulnerable assets. Complementary with anomaly detection tools, it scans your on-premises network traffic, looking for the signatures of the latest attacks, malware infections, system compromise techniques, policy violations, and other exposures, and it raises alarms in your USM dashboard to alert you when threats are identified.
Host-based Intrusion Detection System (HIDS) and File Integrity Monitoring (FIM)
The host-based intrusion detection system (HIDS) capability of USM employs an agent on each host to analyze the behavior and configuration status of the system, alerting on suspected intrusions. HIDS captures and monitors key events across the operating system and installed applications.
Quickly View Threats in the Dashboard
USM uses the Kill Chain Taxonomy to highlight the most important threats facing your environment and the anomalies you should investigate. You can easily see the types of network security threats directed against your critical infrastructure and when known bad actors have triggered an alarm.
Complete Threat Evidence
See attack methods, related events, source and destination IP addresses, as well as remediation recommendations in a unified view, so you can investigate and respond to threats faster.
Reduced Noise
Correlating IDS/IPS data with multiple built-in security tools reduces false positives and increases accuracy of alarms.
Automatic Notifications
Set up notifications through popular channels, including email and SMS, to proactively inform you of critical alarms that may indicate a system compromise or attack.
Attack Intent & Strategy
The Kill Chain Taxonomy breaks out threats into five categories, allowing you to understand the intent of the attacks and how they’re interacting with your cloud environment, on-premises network, and assets:
- System Compromise – Behavior indicating a compromised system.
- Exploitation & Installation – Behavior indicating a successful exploit of a vulnerability or backdoor/RAT being installed on a system.
- Delivery & Attack – Behavior indicating an attempted delivery of an exploit.
- Reconnaissance & Probing – Behavior indicating an actor attempt to discover information about your network.
- Environmental Awareness – Behavior indicating policy violations, vulnerable software, or suspicious communications.
Powerful Analytics Uncover Threat and Vulnerability Details – All in One Console
Get to the bottom of who and what’s targeting your assets and what systems are vulnerable.
Search and Analyze Events
You have the flexibility to conduct your own analysis. For example, you may want to search for events that came from the same host as the offending traffic triggering an alarm.
- Search events to identify activity and trends
- Filters help you find more granular data, such as by event name, IP address, and more
- Examine raw log data related to alarm activity
- Raw logs are securely transmitted and stored for forensics and compliance needs
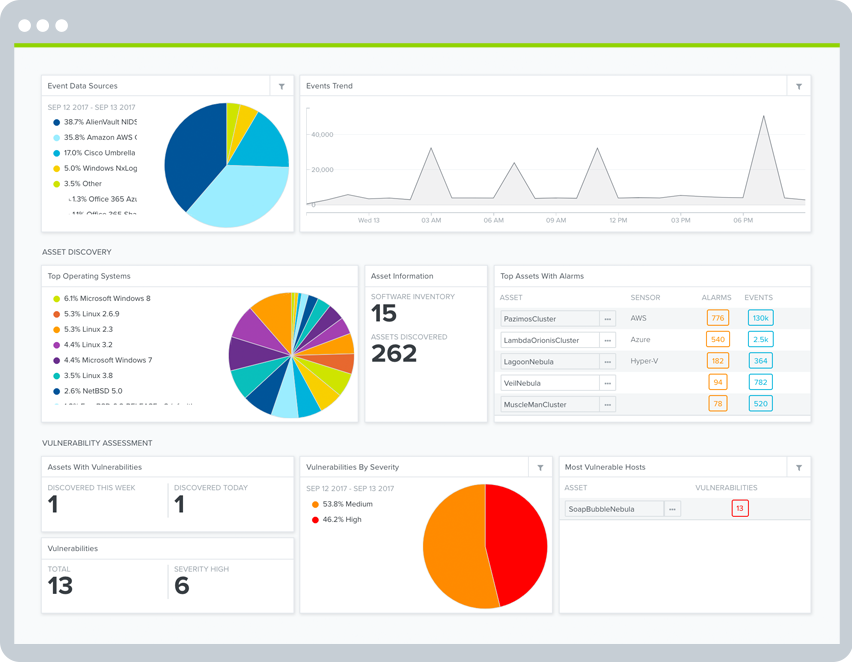
Check Assets and Vulnerabilities
Search the built-in asset inventory for assets involved with an alarm. Integrated vulnerability assessment scans indicate whether an attack is relevant by identifying vulnerable operating systems, applications and services and more – all consolidated into a single view.
- See all reported alarms and events by asset
- Modify your mitigation / remediation strategy based on presence of threats targeting vulnerable systems
- USM correlates reported vulnerabilities with malicious traffic to determine the probability of a breach
Examine Event Details
See the alarm, the individual event(s) that triggered the alarm, and the priority of the alarm.
You can click on any event to examine details such as:
- A summary and description of the event
- Indication of the severity of the event, and its source
- Normalized and enriched event details
- Source and destination IP addresses
- The raw log or event data