Security automation & orchestration
Shorten your incident response time with USM Anywhere.
How Security Automation and Orchestration Can Help
Security automation helps IT teams increase mean time to response and handle intrusion threats faster and more efficiently. By automating your incident response, SOC teams can improve performance and save time.
With the proliferation of single-point security solutions in the marketplace today, it’s no surprise that IT teams struggle to efficiently monitor the security of their environments, or drive effective incident response. Juggling a myriad of solutions that weren’t designed to work together wastes time and resources that small IT security teams can’t afford to lose.
Instead, you need a solution that saves you time by enabling your point solutions to work together, providing centralized orchestration of incident response actions. USM Anywhere™ delivers security operations automation, helping security teams work more efficiently and achieve faster threat detection and incident response.
Built on a foundation of essential security capabilities, USM Anywhere disrupts the cycle of solution-stacking with a unified approach to security and compliance management. By integrating security automation across both internal and external IT security and management technologies, USM Anywhere simplifies end-to-end security management across your entire critical infrastructure.
With a highly extensible architecture, the USM Anywhere platform enables automation that scales as new technologies and threats emerge, saving you the headache and expense of juggling more and more solutions that aren’t built to work together.
USM Anywhere provides security automation and orchestration capabilities to help resource-constrained IT teams work effectively.
Extend Your Reach with Security Orchestration from a Single Pane of Glass
- Connect USM Anywhere with other security solutions like Cisco Umbrella and Palo Alto Networks for proactive, optimized defense
- Easily incorporate new technologies into your security architecture with bidirectional information sharing for accelerated threat detection
Shorten the Time Between Detection and Response with Security Automation
- Reduce the mean time to detect threats with our Threat Intelligence and USM Anywhere’s powerful threat detection capabilities
- Prioritize threats based upon their categorization against the Cyber Kill Chain taxonomy
Take Control of Automated Incident Response
- Orchestrate actions that align to your incident response process
- Easily set up automated response actions based on activity you care about
- Suppress alarms that don’t matter to your organization
Keep Your Organization Secure with a Unified Approach to Security Orchestration
- Unify security and compliance monitoring across your on-premises and cloud environments, and your SaaS applications
- Maintain an active and effective security posture with continuously updated threat intelligence
Extend Your Reach with Security Orchestration from a Single Pane of Glass
Security professionals and attackers are locked in a vicious cycle, with malicious actors spinning out new threats daily and security teams racing to keep up. As the IT security market churns out new point solutions to address these new threats, resource-constrained teams are left with a patchwork of solutions that weren’t designed to work together.
We take a different approach. USM Anywhere’s architecture makes it possible to readily extend the platform’s capabilities through modular software components called AlienApps™. AlienApps interact with other IT security and operations products, and with business-critical applications, to help you unify your security architecture from a single platform, and centralize your orchestration of incident response activities.
AlienApps connect your USM Anywhere deployment to today’s essential tools and services, including Microsoft Office 365, Google G Suite, Cisco Umbrella, and Palo Alto Networks. As new products are procured to address new threats, AlienApps ensure USM Anywhere's ability to share security information and coordinate responses.
AlienApps build on the security automation tools within USM Anywhere by offering capabilities like bidirectional, proactive defense.
Through the AlienApp for Cisco Umbrella, USM Anywhere incorporates log data from Cisco Umbrella into its threat analysis, providing visibility into internet activity at your organization. When USM Anywhere detects a malicious domain, such as ransomware communicating with its ‘Command & Control’ server, it orchestrates a response action that passes the IP addresses of the malicious domain to Cisco Umbrella, which then blocks traffic between that domain and your employees and assets.
Similarly, the AlienApp for Palo Alto Networks allows USM Anywhere to collect and analyze log data from Palo Alto Networks Next-Generation Firewalls, helping detect potential threats within or against your network. When it detects a threat, you can respond—manually or automatically—by sending the IP addresses of potential threats back to the firewall, which can then apply the appropriate policy to either block or isolate the affected IP address.

Shorten the Time Between Detection and Response with Security Automation
Built with resource-constrained teams in mind, USM Anywhere comes with out-of-the-box security orchestration features to help you detect, prioritize, and respond to threats to your organization, starting on Day One. With USM Anywhere, you can shorten your incident response time with features like prioritized alarms, notifications via email or SNS, automated response actions, and remediation templates—all in one unified solution.
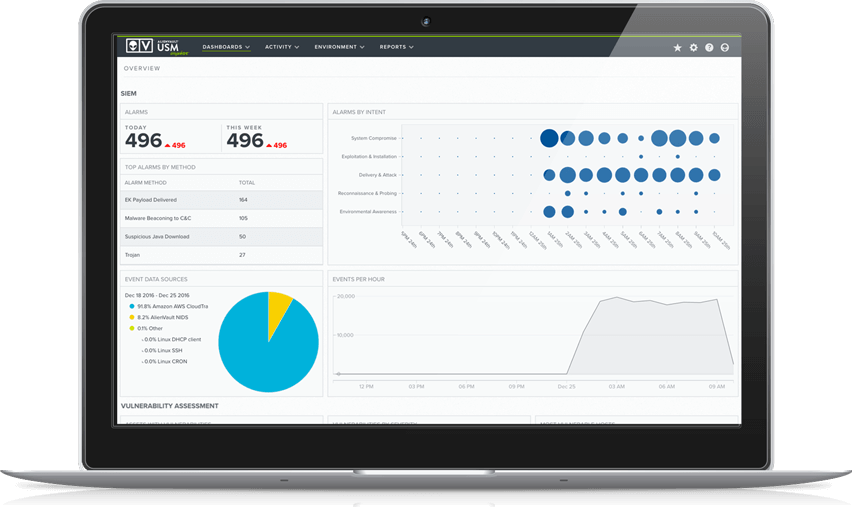
When USM Anywhere detects a threat within your environments, it applies automated prioritization to help you focus on the most important threats first. USM Anywhere prioritizes alarms using the Cyber Kill Chain taxonomy, which weighs factors like how recent the threat is, how valuable the affected assets are to your organization, and what data source the event data came from.
When USM Anywhere detects a threat that requires your attention, you can receive automatic notifications via email, in-product alarms, or Amazon SNS.
USM Anywhere’s security orchestration features help you respond quickly and efficiently to threats affecting your environments. For example, if USM Anywhere detects evidence of ransomware on one of your assets, you can swiftly orchestrate the collection of additional data to help you investigate. For example, when investigating a server you suspect has been compromised, you might want to see what connections are set up, who has logged onto the machine, what processes and services are running on the machine, or your own custom query results.
As the threat landscape evolves, so should your security posture. USM Anywhere keeps your security monitoring and incident response capabilities up-to-date with the latest threat intelligence from the Alien Labs Security Research Team. The Security Research Team investigates the new threats so you don’t have to, continuously building new threat intelligence updates into the USM platform in the form of new correlation directives, intrusion signatures, vulnerability signatures, response templates, and more.
Take Control of Automated Incident Response
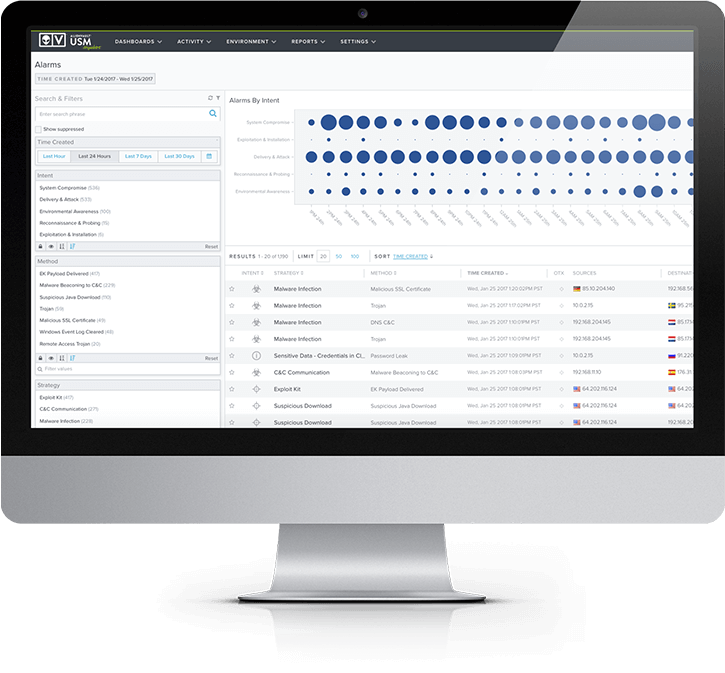
USM Anywhere’s out-of-the-box security orchestration features help you respond to incidents quickly and efficiently. However, when it comes to the automation of incident response actions, many teams are cautious since traditional automated response solutions have not offered the granularity of control required to ensure success in each organization’s unique environment.
USM Anywhere makes it simple to create customized, granular security orchestration rules that automate the incident response actions that make the most sense for, and that align to the particular infrastructure of, your organization.
If certain activity is significant to your organization, you can tap into the extensive event logs USM Anywhere collects from a wide variety of data sources to set up an appropriate automated response action.
For example, you can set up an orchestration rule in USM Anywhere to protect a critical server from brute force attacks by automating the process to action your firewall to block the IP addresses of the attacking servers.
If malware has taken control of a system or communication is detected to a known malicious host, using an automated orchestrated response you can automatically shut it down or isolate the system to avoid cross-contamination to other systems.
You can tailor these rules according to your organization’s unique infrastructure. For example, you might want to take swift, automatic action if you suddenly see communication going from your database server to outside of your environment. Similar activity from a server that isn’t mission-critical might not require the same level of response.
You can also control the volume of alarms you see within USM Anywhere based on your organization’s needs. If a certain alarm doesn’t apply to your organization—for example, if uploading files to Dropbox is a normal business practice and you don’t want that activity to generate noisy alarms—you can easily define suppression rules to cut down on noise.

Keep Your Organization Secure with a Unified Approach to Security Orchestration
While USM Anywhere’s built-in security automation tools offer tremendous time and resource-saving benefits, the foundation on which USM Anywhere is built on is the key to keeping your organization secure.
USM Anywhere delivers five core security capabilities that organizations need for efficient incident response:
Asset Discovery
USM Anywhere creates an inventory of your critical assets, ensuring that your security plan covers everything you need to monitor.
Vulnerability Scanning
Set up regular authenticated scans to identify and respond to vulnerabilities affecting your environments, reducing the ways an intruder can breach your environments.
Intrusion Detection
Effective incident response relies on fast and accurate detection. USM Anywhere provides host intrusion detection, network intrusion detection, and cloud intrusion detection to secure your organization.
Behavioral Monitoring
Identify suspicious behavior and potentially compromised systems across your critical infrastructure.
SIEM and Log Management
Collect the forensic evidence you need to meet your compliance goals, as well as to enable effective incident response.
USM Anywhere integrates these essential capabilities into a single platform that addresses your security monitoring and compliance needs across the breadth of your critical infrastructure, including your on-premises and cloud environments, and SaaS applications.
The threat landscape changes daily, which poses a challenge to security teams without their own team of researchers who can discover and investigate new threats. USM Anywhere addresses this problem by incorporating continuously updated threat intelligence from the Alien Labs Security Research Team, enabling optimal protection for your organization. The Security Research Team researches the latest threats so you don’t have to, serving as an extension of your own security team so you’re always ready to detect the latest threats.