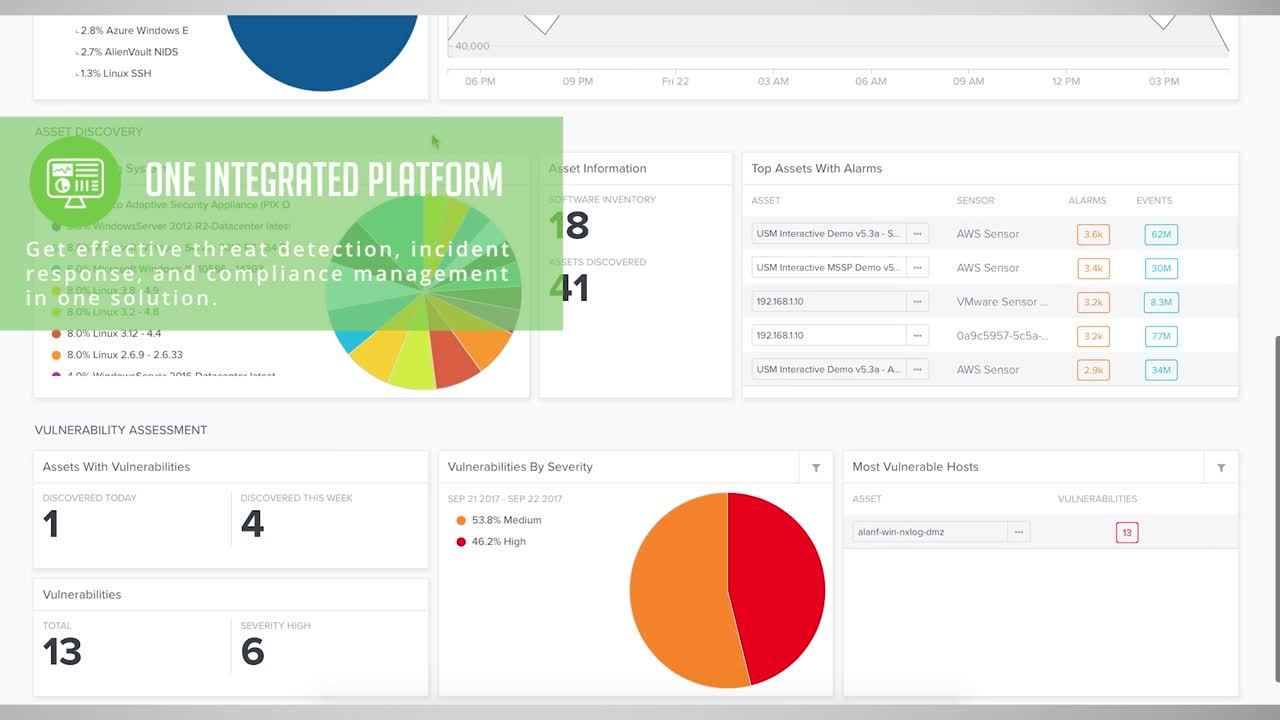
Complete Security Visibility in One Single View
Security analysts are a lot like detectives. During security incidents and investigations, they need to get to “whodunit” as quickly as possible. This is complicated, especially when mountains of security-relevant data are constantly being produced. Context is key: one piece of information by itself may mean nothing, but then again, it may become a very important piece of a larger puzzle.
Security intelligence is an essential part of putting that puzzle together. By automating the correlation of real-time events identified through built-in essential security, AlienVault’s Unified Security Management™ (USM) platform provides the security analyst with all of the puzzle pieces in one single view.
Dynamic Incident Response Guidance - for Every Alarm
Being a security analyst isn’t easy. You don’t have all day to research new exploits. But it turns out AlienVault Labs is a team dedicated to doing just that. In addition, there are often so many items to respond to, it’s hard to know what to do next. AlienVault’s dynamic incident response guidance and it’s vigilance in discovering new malicious hosts and exploits can help you.
For each alarm that is generated by the AlienVault USM™ event correlation engine, customized step-by-step instructions are listed in our console. By providing contextually relevant workflow-driven response procedures, analysts know exactly what to do next. The AlienVault Labs research team has curated these how-to-respond instructions based on rich CSIRT experience, as well as our own threat intelligence.
For example, an alert might identify that a host on your internal network is attempting to connect to a malicious external host. The dynamic incident response guidance would include details about:
- The internal host such as owner, network segment, and software that is installed
- The network protocol in use and specific risks associated with it
- The external host and what exploits it has executed in the past
- The importance of identifying potential C&C (command and control) traffic
- Specific actions to take for further investigation and threat containment – and why you should take them