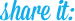Chapter Five
Incident Response Training: Why Security Awareness is Key

Despite the great leaps in innovation we’ve witnessed over the past few decades, nothing beats a human being’s common sense and good judgment. In fact, pragmatism, common sense and good judgment are a few values that aren’t yet possible to develop in software code or artificial intelligence.
The truth is, you can’t automate intuition. And much of the incident responder’s job comes down to relying on your and each employee’s intuition that something in that email just doesn’t look quite right (as an example). Your goal is to reduce the number and impact of cases when someone’s bad judgment, mistakes, and oversights open the gate to a possible breach. It could happen from clicking on an embedded link in an email, or a social engineering scam over the phone.
However it happens, you won’t find the answer in some sort of magic pill - like information security awareness software downloaded to your brain a la Trinity in the Matrix. That’s why you need an information security awareness training program. And yes, like many things in incident response, hearing that phrase is likely to inspire a yawn or two. And a sigh, and maybe throw in a few eye rolls too, while you’re at it.
But it doesn’t have to. There are a few tools, resources, and program ideas that can make information security awareness training effective and engaging for your employees. And that’s what we’ll cover in this chapter.
Incident Response Training vs. Security Awareness Training
We recommend having two different training programs: one for the overall employee population and one that’s specifically for the incident responder. As for any specialized set of skills, incident response training should focus on all aspects of the job, the IR process, as well as the specific technical skills (programming, systems administration, and code analysis) to support whatever technologies or computing contexts that are relevant for your company.
Within this guide, we’re focused on the more broad topic of security awareness training, because we’ve seen that improving the security awareness of everyone in your company will have a big impact on reducing the number and cost of security incidents. We’re also hoping that this entire guide provides a rich foundational resource for training the members of your IR team.

See the Survey: Maturing and Specializing: Incident Response Capabilities Needed >
What Exactly Do Employees Need to Know About Security? How Much Is Too Much?
It’s a great question and one that requires we return to our primary goal for security awareness training: to reduce the number and impact of high risk security incidents. So let’s focus on the biggest risk first: phishing and spear-phishing.
Phishing and spear-phishing attacks are the most common way that employees can be manipulated into exposing your company to risk. These social engineering scams are responsible for many of the high profile breaches you’ve likely already heard of. The key difference between phishing and spear-phishing is that spear-phishing is customized and targeted to a specific employee and company, whereas phishing is more broad and automated, less sophisticated and less specific.
Defending against both types of attacks requires vigilance and awareness on the part of every employee. Remember to keep your training content and approach focused on teaching skills and good judgment vs. teaching the technical aspects of how phishing works on the back end, or esoteric topics like the differences between a rootkit, a bot, and a keystroke logger.
Show employees a few examples of phishing and spear-phishing scams, and encourage them to be suspicious, even if an email may appear to be from someone they know. You may also wish to consider incorporating simulated phishing attacks to educate employees about appropriate security behaviors, measure the effectiveness of your training program, and identify any knowledge gaps.
Security Awareness Training Goals & Metrics
Trying to increase “awareness” around any topic is somewhat dubious. How do you measure how “aware” someone is? Hopefully by their behavior, and with any luck, by the reduction in the number of incidents and exposures you keep having to respond to.
Creating good security metrics is an art unto itself, and while there are many things that generate numbers that can be tracked, good metrics don’t just speak to what has been done, but how well it was done – they enable the future, not recount the past.
That said, here are a few sample indicators for increased awareness and effective training:
- Track help desk tickets, and expect to see an increase in employees reporting suspicious events and activity. This wouldn’t necessarily be because there are more suspicious events happening, simply that employees are more sensitive to them, and feel confident in reporting them.
- Explore non-traditional training methods like simulation exercises to test an employee’s resistance to social engineering scams, and then measure progress on a quarter-by-quarter basis. However, work with your communications team to give everyone ample heads up, to maintain trust and transparency between employees and the infosec team.
Information Security Awareness Training: Top Seven Tips