Asset discovery
Everything you need to automate asset discovery, detect threats, and accelerate your incident response.
We understand that security practitioners and IT professionals have enough to worry about, and more than enough work to do. With Unified Security Management® (USM), you can stop worrying about what’s connected to your network and what instances are running in your cloud environments.
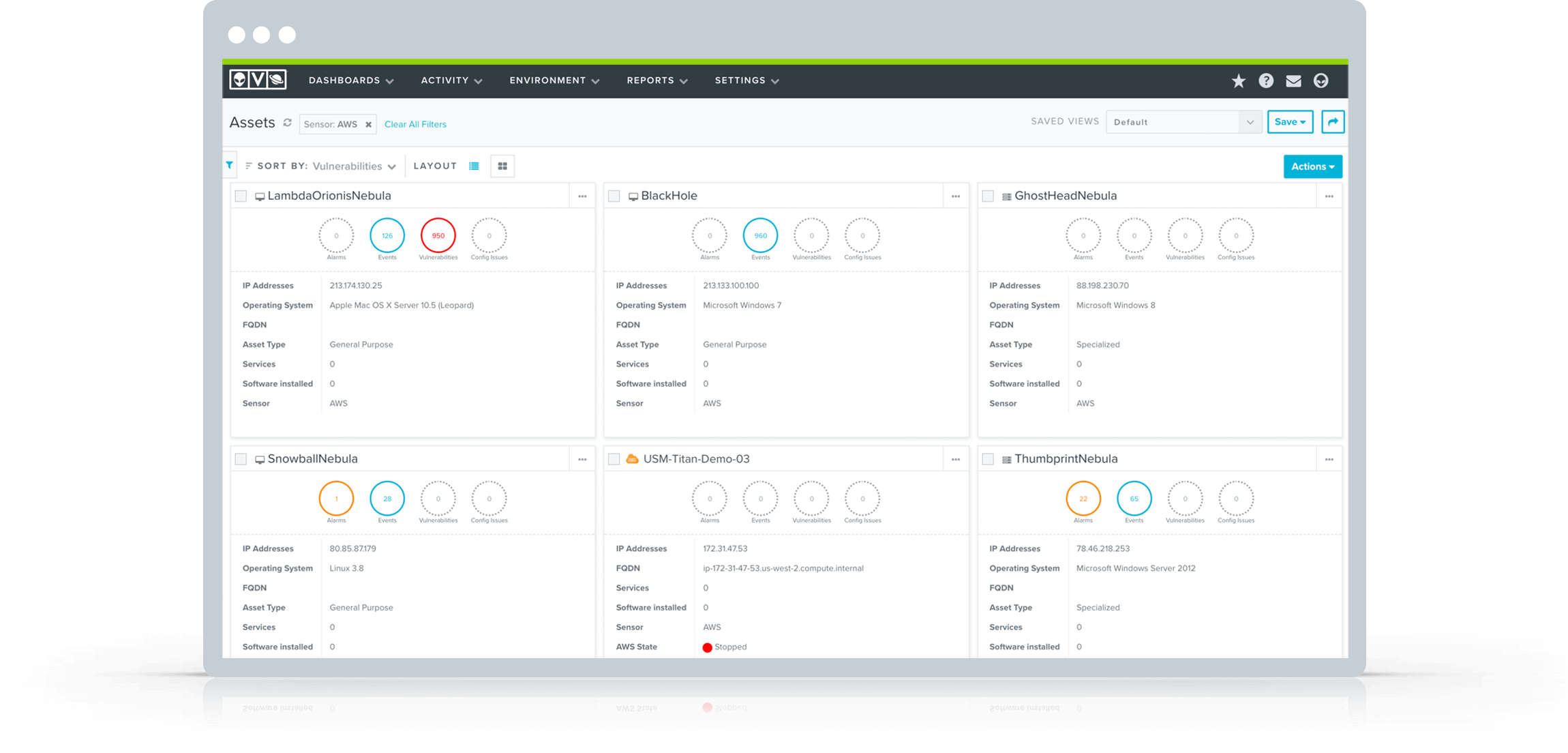
Within minutes of installing the USM platform, the built-in asset discovery will find and provide you visibility into the assets in your AWS, Azure, and on-premises environments. You will be able to discover all the IP-enabled devices on your network, determining what software and services are installed on them, how they’re configured, and whether there are any vulnerabilities or active threats being executed against them. If you have cloud infrastructure, USM’s built-in asset discovery capability will find and provide visibility into the assets in your AWS and Azure environments.
With the USM platform, you'll be able to quickly answer questions such as:
- What instances are running in my cloud environments?
- What devices are on my physical and virtual networks?
- What vulnerabilities exist on the assets in my cloud and network?
- What are my users doing?
- Are there known attackers trying to interact with my cloud and network assets?
- Are there active threats on my cloud and network assets?
Correlate Asset Info with Threat & Vulnerability Data
It's a problem when you don't know what’s on your cloud and network environments and how the assets within those environments are configured. Wouldn't you prefer certainty?
Automated asset discovery and scanning can start you on the path to certainty. The USM platform combines core discovery and inventory technologies to give you full visibility into the devices that show up on your network and the instances running in your cloud environments.
Network Asset Discovery
USM gently scans your environment to gather information about your device. These responses provide clues that help identify the device, the OS, running services, and the software installed on it. They can also often identify the software vendor and version without having to send any credentials to the asset to run a more invasive scan.
Passive Network Monitoring
USM utilizes passive network monitoring techniques to evaluate network communications and identify information about assets that are on the network.
- IP and hardware MAC address pairings for use in asset inventory and to detect MAC spoofing
- IP header analysis to identify operating systems and running software packages
- TCP/IP traffic analysis for OS fingerprinting and basic network topography
Cloud Asset Discovery
USM hooks directly into cloud infrastructure providers’ APIs to give you immediate visibility into your cloud environment within minutes of installation. The USM platform leverages native cloud services like AWS CloudWatch and Azure Insights to collect data from your cloud environments and begin detecting threats.