Managed detection and response service
Learn how our approach to managed detection and response (MDR) can help detect cyber threats early and provide coordinated defenses for fast response.
Why AT&T Cybersecurity for MDR
Protect your business with 24 x 7 threat detection and response from AT&T
Compared to a do-it-yourself approach, a managed detection and response (MDR) service can provide a faster, simpler deployment and help to drastically reduce the complexity and cost associated with managing a security technology stack.
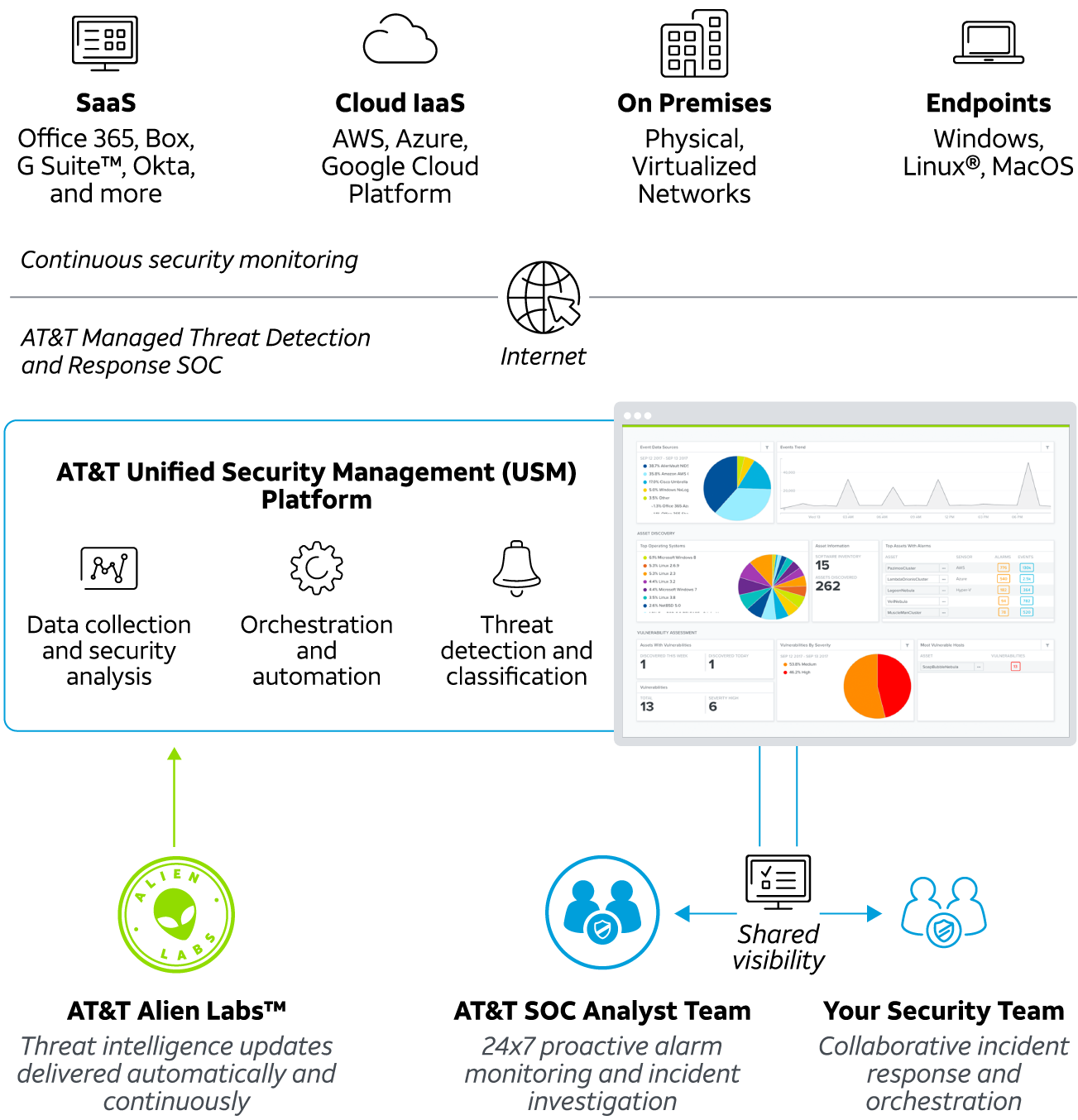
AT&T Managed Threat Detection and Response is an MDR service that helps you to detect and respond to threats before they impact your business. It provides 24 x 7 proactive security monitoring, alarm validation, security orchestration and automation, and more in one service, helping you to enhance your security posture quickly and cost effectively.
Built on AT&T Unified Security Management
Gain centralized security visibility across your cloud environments and on premises, including endpoints, networks, and cloud apps.
Fueled with AT&T Alien Labs threat intelligence
AT&T Alien Labs fuels our SOCs with continuous threat intelligence backed by the Open Threat Exchange (OTX) and the AT&T CSO.
Managed 24x7 by AT&T SOC analysts
Our SOC analysts monitor and investigate alarms, working with your security or IT personnel to respond to incidents.
Get started in less than 30 days
Our SOC analysts can be monitoring your critical infrastructure and responding to threats within 30 days of contract signature.
Resources
Learn more about threat detection and response
AT&T Managed Threat Detection and Response takes advantage of our award-winning unified security management (USM) platform that combines multiple essential security capabilities in one unified console to help support earlier detection, fewer false positives, and faster response.
Continuous data collection across your environments
Centralize security monitoring of all your critical assets across cloud environments and on premises, including endpoints, networks, and cloud apps.
Multiple security capabilities in one unified platform
Our USM platform is able to provide more complete threat coverage than point solutions alone, enabling early detection and helping to minimize false positives.
- Cloud and network asset discovery
- Vulnerability assessment
- User and asset configuration
- Network intrusion detection (NIDS)
- Endpoint detection and response (EDR)
- Dark web monitoring
- SIEM event correlation and log management
AlienApp integrations for continuous monitoring and security orchestration
The highly extensible architecture of the USM platform makes it possible to readily extend its security orchestration and automation capabilities through modular software components called AlienApps.
Some of the 450+ pre-built AlienApps include Microsoft Office 365, Box, Salesforce, Google G Suite™, Cisco Umbrella™, Palo Alto Networks®, CarbonBlack, and more.
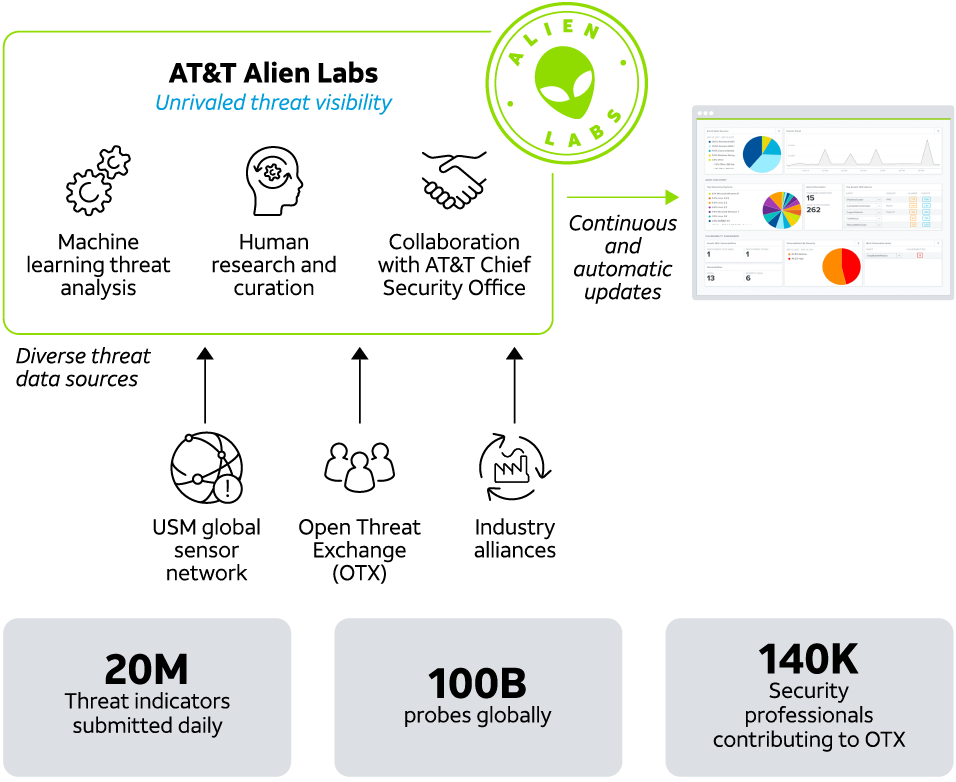
AT&T Alien Labs fuels our SOCs with continuous threat intelligence backed by the Open Threat Exchange (OTX) and the expertise of the AT&T CSO so you can stay current with the constantly shifting threat landscape.
Unique threat visibility
Alien Labs has unrivaled visibility into the AT&T IP backbone, the global USM Sensor network, the Open Threat Exchange (OTX), and other sources of threat data.
Deep insights into adversaries and attacks
The Alien Labs research team uses proprietary analytics, machine learning (ML), and a global team of threat researchers to analyze and interpret the huge volume of threat data we collect. This team goes beyond simply delivering threat indicators to performing deep, qualitative research that provides insight into adversary tools, tactics, and procedures (TTPs) to our customers and the larger intel community.
Automating proactive threat hunting
We write and update threat correlation rules that are directly integrated with the USM platform on a daily basis.
Updates include:
- Correlation directives
- NIDS signatures
- HIDS signatures
- Vulnerability signatures
- Asset fingerprints
- Response templates
- Reporting modules
- Data source plugins
The AT&T Security Operations Center (SOC) has a dedicated team of security analysts who are solely focused on helping you to protect your business by identifying and disrupting advanced threats around the clock.
The AT&T Managed Detection and Response SOC analyst team handles daily security operations on your behalf so that your existing security staff can focus on strategic work.
Ongoing security program advocacy
In addition to continuous monitoring and incident investigation, our analyst team leads regular review calls with your security team to cover all investigations and incident response activities.
Our analysts host regular meetings with your team to review service metrics related to our SLAs, and to review progress towards your security program objectives and provide recommendations for improvements.
How the AT&T SOC operates
24x7 alarm monitoring and validation
- 24x7 eyes on glass in our SOC
- Tier 1 analysts review every alarm in the USM platform
- Remove false positives and non-actionable alarms
- Escalate actionable alarms for Tier 2 validation
Escalation and incident investigation
AT&T SOC analysts:
- Lead alarm analysis and validation
- Escalate incidents and open investigations
- Gather evidence, conduct forensics and research
- Assign severity and notify your team per SLAs
- Together, we execute against your incident response plan
Response orchestration and automation
- AlienApps enable response actions to third-party tools
- Orchestration rules help to automate response actions
- We can also facilitate response towards other AT&T managed security services
With our high-touch service delivery model and SaaS platform deployment model, our SOC analysts can be monitoring your critical infrastructure and responding to threats within 30 days of signing the contract.
Service onboarding and threat modeling
Every service onboarding experience begins with an AT&T Cybersecurity consulting engagement. Our highly skilled consultants lead a threat modeling workshop to identify and guide deployment requirements and establish future security program objectives.
Based on the in-depth analysis of your environment, our SOC analysts are able to install, configure, and tune your USM platform deployment according to your requirements and integrate with other security technologies that are in scope of our AlienApps framework.
Training and enablement for your security personnel
Going beyond the initial technology implementation, our analysts use this onboarding engagement as an opportunity to train and enable your security personnel on the platform and to develop a custom Incident Response Plan in collaboration with your incident response team.
Get a quote
We're here to help! Complete the form and we will be in touch soon.
