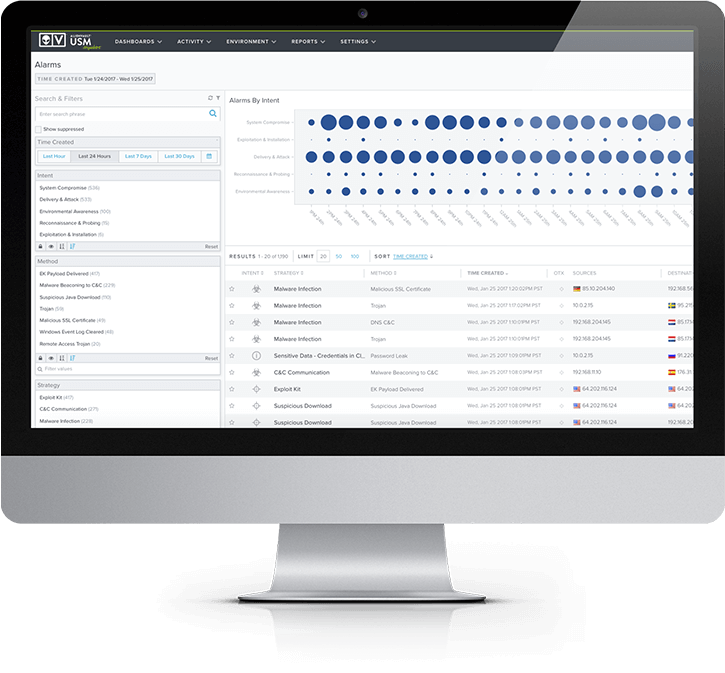
Network security monitoring
AlienVault Unified Security Management (USM) gives you complete network security monitoring for your cloud, on-premises, and hybrid environments.
Complete Network Security Monitoring in a Single Pane of Glass
Effective network security monitoring requires you to collect, analyze, and correlate security data from across your cloud and on-premises environments to identify threats and intrusions. Alone, intrusion detection systems (IDS) are not enough. To fully monitor and protect your network, you need a unified view of:
- What's connected to your infrastructure at all times
- Vulnerable systems that could be exploited
- Threats and activity with known malicious hosts
- Security incidents with correlated event data
- Regular threat intelligence updates
- Aggregated events and logs from your cloud, on-premises, and hybrid environments
Traditionally, orchestrating this information within network security monitoring software has been complex, expensive, and out of reach for most organizations. AlienVault® Unified Security Management® (USM) breaks through this complexity and expense by bringing together multiple essential security capabilities on a unified platform that’s cost effective and easy to use.
In addition, continuous threat intelligence updates from the AlienVault Labs Security Research Team are delivered to the USM platform, backed by the AlienVault Open Threat Exchange® (OTX™) — the world’s first truly open threat intelligence community.
AlienVault USM delivers essential network security monitoring tools in a single pane of glass, enabling you to:
Know Your Assets & Vulnerabilities
- Asset Discovery & Inventory
- Vulnerability Assessment
Detect Threats & Intrusions Faster
- Cloud Intrusion Detection (CIDS)
- Network Intrusion Detection (NIDS)
- Host-Based Intrusion Detection (HIDS)
Analyze Security Incidents with SIEM
- Graph-based Correlation Engine
- Cross-Correlation Directives
- Incident Response Guidance
Stay Vigilant with Continuous Threat Intelligence
- Continuous Threat Intelligence Updates from AlienVault Labs
- OTX Community-driven Threat Intelligence
Know Your Assets & Vulnerabilities
For effective network security monitoring, you need to see what devices are connected in your environment and how the vulnerabilities on those assets expose you to threats and intrusions.
Because AlienVault USM uniquely combines asset discovery and inventory, vulnerability assessment, intrusion detection data and threat intelligence all within a single pane of glass, you can know (within in minutes of installation):
- What assets are connected to your environment
- What vulnerabilities exist on those assets
- What threats or intrusions are being executed against your vulnerable assets
- Which vulnerabilities are actively being exploited in the wild and how
Knowing which vulnerabilities are actively being exploited in the wild helps you to better plan and prioritize your remediation activities.
Asset Discovery & Inventory
Using active network scanning, AlienVault USM auto-discovers all the IP-enabled devices connected to your environment, how they’re configured, what services are installed and actively listening, any potential vulnerabilities, and any active threats being executed against them.
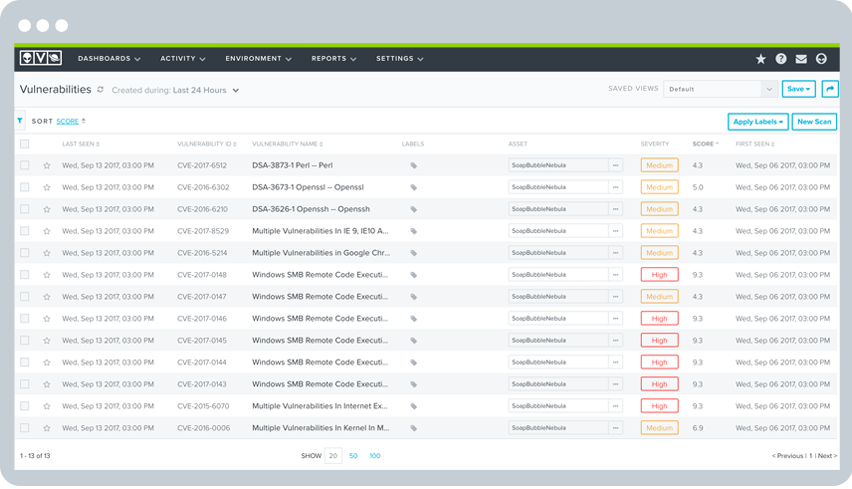
Vulnerability Assessment
AlienVault USM performs authenticated vulnerability scanning with the most up-to-date vulnerability signatures from the AlienVault Labs Security Research Team. This identifies the “holes” in your network that expose you to threats and intrusions. The USM platform ranks vulnerabilities by severity to help you prioritize your response. When intrusions do occur, you have a unified view of important asset and vulnerability data, so you can respond faster.
Detect Threats & Intrusions Faster
Attacks do not usually happen in one swift blow. Rather, they unfold in multiple steps. The earlier you detect attacks, the better chance you have at intervening to prevent a data breach or other harm.
AlienVault USM enables early intrusion detection and response with built-in cloud intrusion detection (CIDS), network intrusion detection (NIDS), and host intrusion detection (HIDS) systems. These tools monitor your traffic and hosts, along with user and administrator activities, looking for anomalous behaviors and known attack patterns. The built-in SIEM capability in the USM platform automatically correlates IDS data with other security information to give you complete visibility of your security posture.
In addition, AlienVault Labs Security Research Team continuously delivers threat intelligence updates directly to the USM platform, including the latest IDS attack signatures and correlation directives. So, you always have the most up-to-date threat detection intelligence as you monitor your environment for intrusions and other threats.
Cloud Intrusion Detection System (CIDS)
USM Anywhere provides native intrusion detection system (IDS) capabilities in AWS and Azure cloud environments. Cloud sensors purpose-built for AWS and Azure cloud environments leverage AWS and Azure APIs, so you have full visibility into every operation that happens in your cloud accounts.
Network Intrusion Detection System (NIDS)
The Network Intrusion Detection System (NIDS) capability of the USM platform detects known threats and attack patterns targeting your vulnerable assets. It scans your on-premises network traffic, looking for the signatures of the latest attacks, malware infections, system compromise techniques, policy violations, and other exposures, and it raises alarms in your AlienVault USM dashboard to alert you when threats are identified.
Host-based Intrusion Detection System (HIDS)
The Host-based Intrusion Detection System (HIDS) capabilities in AlienVault USM employ an agent on each host to analyze the behavior and configuration status of the system. HIDS captures and monitors key events across the operating system and installed applications.

Analyze Security Incidents with SIEM
The goal of network security monitoring is to detect and respond to threats as early as possible to prevent data loss or disruption to your operations. However, this can be complicated when mountains of security-related events and log data are continuously produced by multiple disparate security tools.
AlienVault USM has powerful SIEM and centralized logging capabilities built in so you can aggregate and make sense of security data generated across your network. Going beyond traditional SIEM products, the USM platform combines multiple essential security capabilities – asset discovery, vulnerability assessment, intrusion detection, behavioral monitoring, SIEM event correlation, and log management so that when an incident happens, you have immediate 360° visibility of the actors, targeted assets and their vulnerabilities, methods of attack, and more.
USM Anywhere deploys with ready-to-use SIEM correlation rules, and with its graph-based machine learning and finite state machine (FSM) correlation engine, you can start detecting threats on Day One. As threats evolve, threat intelligence is continuously updated by AlienVault Labs and delivered directly to the USM platform.
Cross-Correlation of Events
For IDS-generated events, which by themselves can be quite noisy, AlienVault USM checks to see what vulnerabilities would be needed for an exploit to be successful. AlienVault USM then checks if the asset is actually vulnerable. This data is correlated and risk is assessed, so you can focus on the information that really matters most.
Incident Response Guidance
AlienVault USM delivers dynamic incident response guidance to assist you with your intrusion response, including details about:
- Context on the threat, including details on strategy, method, and actor
- Enriched information on the incident from the Open Threat Exchange (OTX), with links to ‘pulses’ from the OTX community
- The affected asset, including the software and services installed and other related vulnerabilities and alarms
- The destination IP address or domain communications are being sent to (e.g. Command & Control server)
- Recommended actions to take for further investigation and threat containment