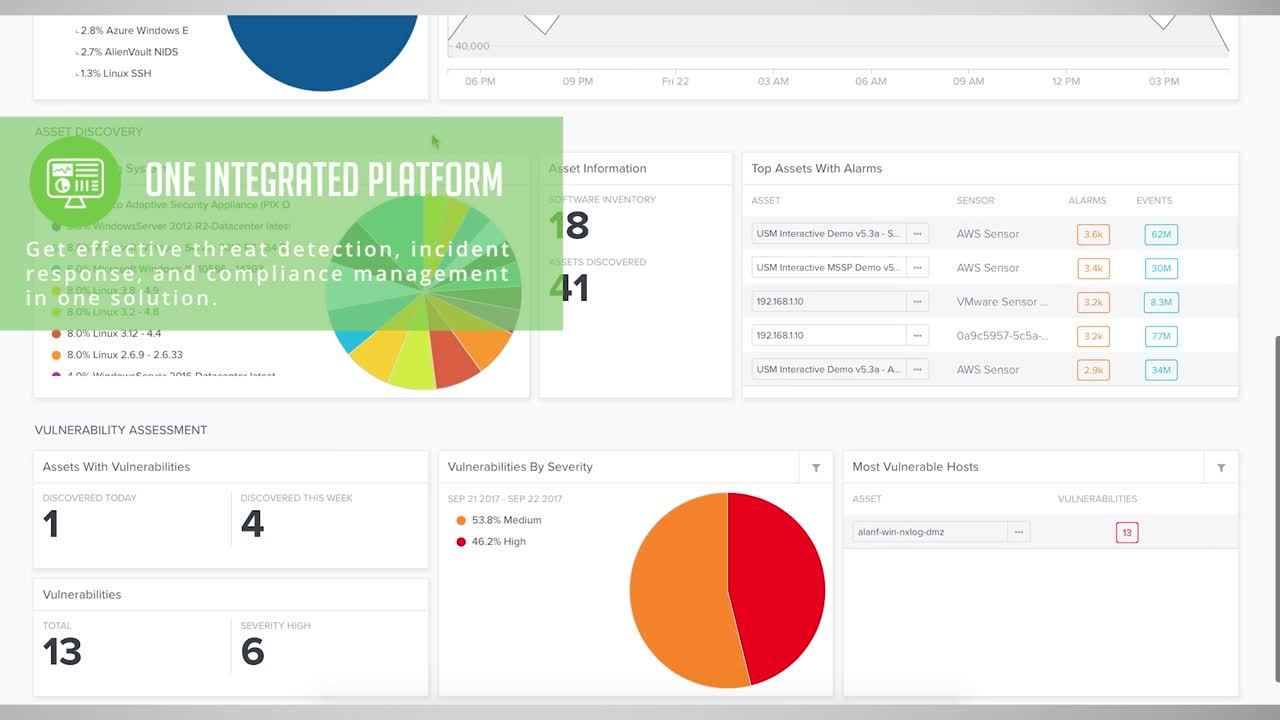
Security event management and monitoring
Managing security events with powerful monitoring software within Unified Security Management™ (USM) allows you to focus on the most important security events in your organization.
Monitor Security Events and Stay on Top of What’s Important
Every system in your IT enterprise generates a security event of some type. This can be very useful as it maintains a historical record of events that have happened and statuses of systems in a time sequential format as well as recording activity on the network.
Security events can assist in:
- Determining what happened
- Intrusion detection
- Incident containment
- Forensic analysis
- Real-time alerts of malicious activity
- Understanding attacker intent
- And more
However, the amount of data generated can be overwhelming and without an effective security event management system, you could be missing critical events.
Knowing which activities and systems to monitor and when is key to filtering and locating the needle in the haystack of event data that could be the cause of a security breach.
AlienVault USM™ delivers essential security event management and monitoring capabilities:
Centralized Security Alerts
- Automatic event correlation
- Easily configure monitoring for all critical assets
- Monitored security events arranged by kill chain methodology to give you context into actions
Actionable Intelligence
- Identify patterns of known malicious activity
- Host and network intrusion detection
- Behavioural monitoring
- Powered by Open Threat Exchange™, the world’s largest open threat intelligence community
Compliance
- Report templates for PCI-DSS, ISO 27002, HIPAA and more
- Role-based access control for customized views
- Visibility into which users are violating policy
Centralized Security Alerts
One of the best first steps in effectively monitoring and managing security events is to collect and correlate logs from across systems, applications and network devices. Within these logs lies an audit trail of who has done what, where, when and why.
However, monitoring events from disparate systems can be a huge challenge. These logs contain an enormous amount of information and identifying anomalies can be difficult.
USM takes the guesswork out of security event management by analysing and correlating security events across all systems and builds all the monitoring and security event management capabilities you need into a centralized dashboard which is arranged using the Kill Chain Taxonomy. This allows you to focus on the most pressing events.
It breaks out events into five categories that help you to understand security events intent and severity, based on how they’re interacting in your environment.
- System Compromise
- Exploitation & Installation
- Delivery & Attack
- Reconnaissance & Probing
- Environmental Awareness
Compliant Security Event Management
Compliance isn’t a one-time event, rather a system of processes that need to be continually enforced. Although specific requirements for monitoring and security event management vary from one standard to the next, USM can help you quickly achieve compliance with all the essential security capabilities you need in a single console.
Compliance benefits with USM include:
- Flexible reporting and dashboards
- Report templates for PCI-DSS, ISO 27002, HIPAA and more
- Role-based access control for customized views
- Visibility into which users are violating policy
- Privileged user monitoring
- Monitoring for disruptions & intrusions using network traffic and file integrity monitoring