SIEM software & solutions
SIEM and log management plus everything you need to detect and respond to threats.
Benefits
Full-scale SIEM solutions
Single-purpose SIEM software solutions and log management tools provide valuable security information, but often require expensive and time-consuming integration efforts to bring in log files from disparate sources such as asset inventory, vulnerability assessment, endpoint agents, and IDS products. Once you have the data, you then must research and write correlation rules to identify threats in your environment. These challenges multiply as you migrate workloads and services from on-premises infrastructure to public cloud environments.
For today’s resource-strapped IT teams, the time and expense required to deploy a SIEM seriously delays their time to threat detection, and thus, return on investment.
See the advantages of all-in-one security essentials versus traditional SIEM
Discover a smarter way to prioritize your incident response
Investigate threats deeper with advanced security analytics
Stay vigilant with threat intelligence updates from Alien Labs
See the advantages of all-in-one security essentials versus traditional SIEM
Traditional SIEM software solutions promise to provide what you need, but the path to get there is one that most of us can’t afford. Traditional SIEM solutions collect and analyze the data produced by other security tools and log sources, which can be expensive and complex to deploy and integrate. Plus, they require constant fine-tuning and rule writing.
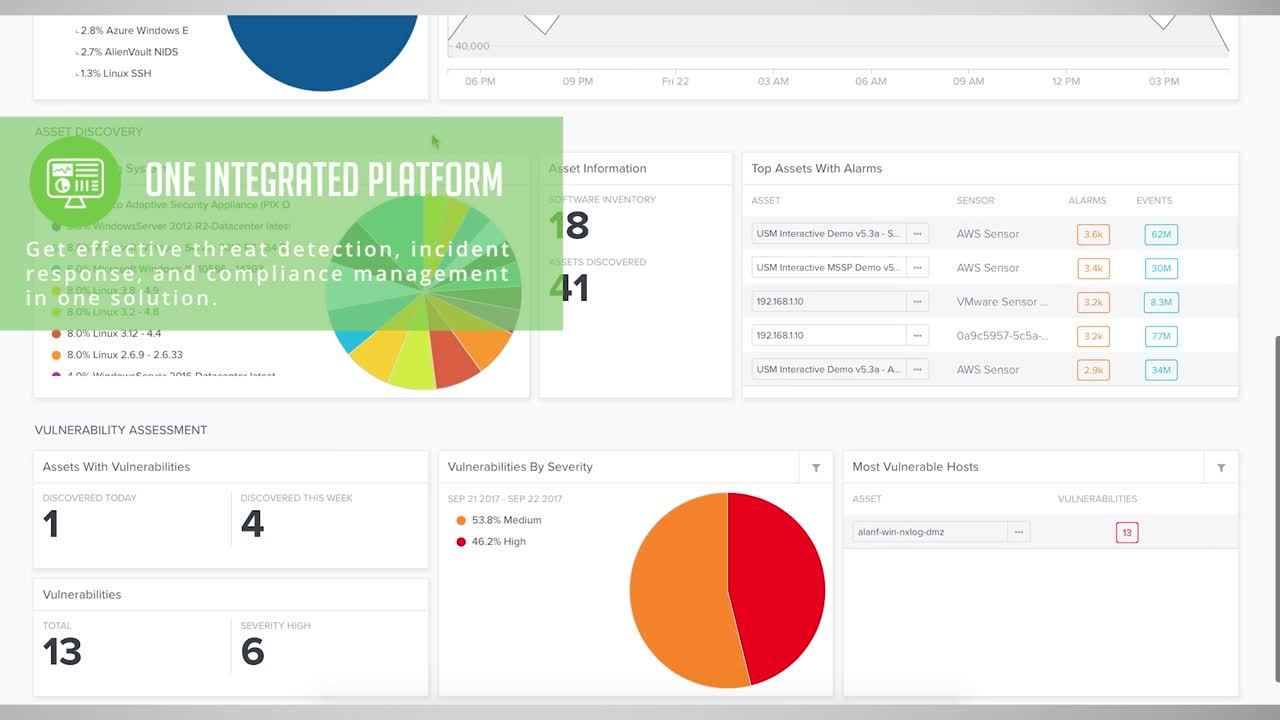
AlienVault USM provides a different path. In addition to all the functionality of a world-class SIEM, AlienVault USM unifies the essential security capabilities needed for complete and effective threat detection, incident response, and compliance management—all in a single platform with no additional feature charges. Our focus on ease of use and rapid time to benefit makes the USM platform the perfect fit for organizations of all shapes and sizes.
Features:
AlienVault USM
Traditional SIEM
Management:








(3rd-party product that requires integration)
(3rd-party product that requires integration)
(3rd-party product that requires integration)
(3rd-party product that requires integration)
(AWS, Azure, Office 365, G Suite)
(3rd-party product that requires integration)
(3rd-party product that requires integration)
(3rd-party product that requires integration)
(3rd-party product that requires integration)
Discover a smarter way to prioritize your incident response
The promise of SIEM software is particularly powerful—collecting data from disparate technologies, normalizing it, centralizing alerts, and correlating events to tell you exactly which threats to focus on first. Unfortunately, achieving and maintaining the promise of SIEM is time-consuming, costly, and complex.
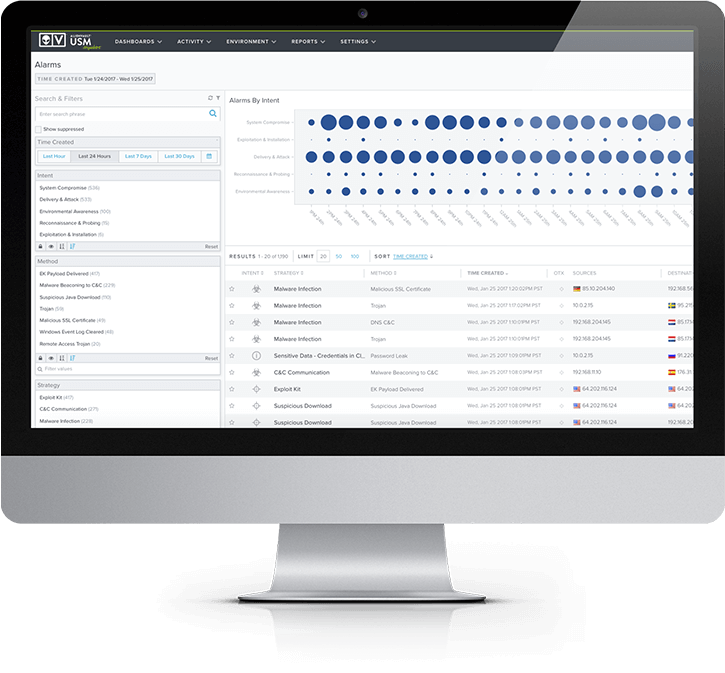
AlienVault USM centralizes all the security capabilities you need and simplifies your response efforts by providing an intuitive, graphical alarm dashboard that utilizes the Kill Chain Taxonomy to focus your attention on the most severe threats.
For each alarm in AlienVault USM, you have a complete view of threat evidence: attack methods, related events, source and destination IP addresses, as well as incident response remediation recommendations in a unified view, so you can investigate and respond to threats faster. The USM platform works to reduce noisy alarms and false positives, making your work more efficient.
The kill chain taxonomy in USM
AlienVault USM breaks out attacks into five threat categories to help you easily identify attack intent and threat severity, based on how threats interact with your environment.
- System compromise – Behavior indicating a compromised system
- Exploitation & installation – Behavior indicating a successful exploit of a vulnerability or backdoor/RAT being installed on a system
- Delivery & attack – Behavior indicating an attempted delivery of an exploit
- Reconnaissance & probing – Behavior indicating a bad actor attempting to discover information about your network
- Environmental awareness – Behavior indicating policy violations, vulnerable software, or suspicious communications
Investigate threats deeper with advanced security analytics
When an incident happens, you need immediate 360° visibility of the actors, targeted assets, exploitable vulnerabilities on those assets, methods of attack, and more. AlienVault USM delivers all this data in a unified console with rich security analytics, so you can instantly get the context you need to make fast, effective decisions.
Search and analyze events
In AlienVault USM, all relevant security data is available at your fingertips with intuitive search and filter capabilities, making incident investigation a fast and efficient process. In the USM platform, you can easily:
- Search events to identify activity and trends
- Apply filters to find more granular data
- Sort by event name, IP address, and more
- Create, save, and export custom data views
- Generate custom reports from any view or leverage pre-built templates
- Examine raw log data related to alarm activity
- Access OTX pulses and “in the wild” security information
Unified security visibility of assets, events, and vulnerabilities
For every alarm raised in AlienVault USM, you can drill down to see the related assets, vulnerabilities, events, and much more from a single consolidated view. All-in-one unified security management means that you can:
- See all alarms and events per asset
- Proactively query endpoints for additional information
- Know if your vulnerabilities affect high-priority or business-critical assets
- Correlate vulnerabilities with malicious activities
- Drill down in an alarm to see the individual events that triggered the alarm
- View forensics data about what triggered events
- Instantly launch pre-built forensics and response actions directly from an event or alarm
- Create an orchestration rule directly from an executed action to apply to similar alarms and events that occur in the future