Introduction
The Open Threat Exchange (OTX) team has been hard at work and we wanted to update everyone on some new functionality that we believe will be very useful to you. We're happy to announce that Alienvault OTX is now a STIX/TAXII feed/server.
What Does That Mean? What is STIX/TAXII?
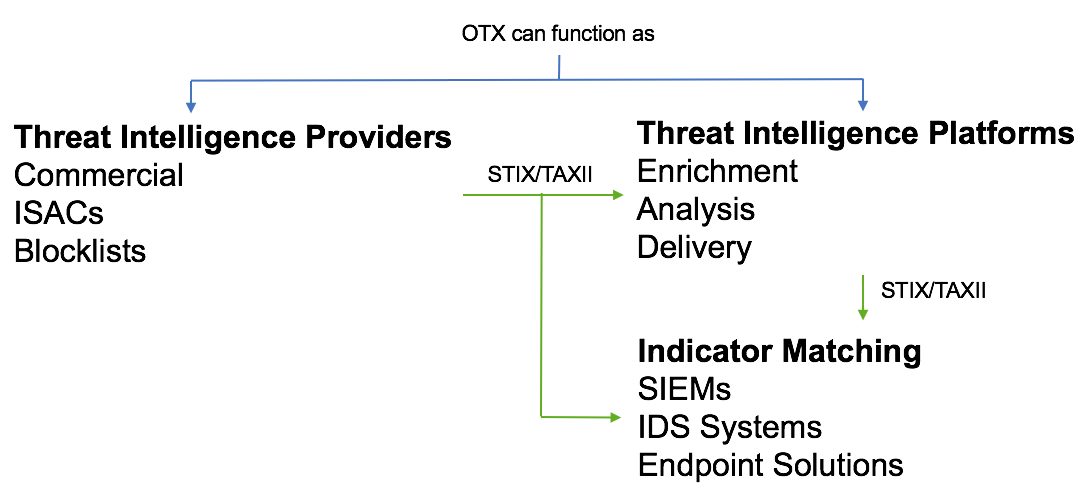
STIX provides a formal way to describe threat intelligence, and TAXII a method to deliver that intelligence.
For example, an Information Sharing and Analysis Center (ISAC) might share information about attacks against an industry via STIX/TAXII. Companies that are members of the ISAC then collect this (and other) information in a threat intelligence platform, then feed this information onto their security devices. They might also skip the threat intelligence platform and feed information from the ISAC directly to their security devices.
OTX can now act as both a provider and a platform in your environment.
Getting set up
To consume the OTX STIX/TAXII feed you'l need to enter the following details into your TAXII client:
Discovery URL https://otx.alienvault.com/taxii/discovery
Username:(Your API key)
Password: (Blank)
Deliver your own intelligence from OTX to your network and your customers
You can use the group functionality of OTX to store threat intelligence and privately share it with people you specify. You can then deliver this by STIX/TAXII to your devices, or if you are a service provider, to your customers. You can also maintain feeds within these groups.
How are you using STIX/TAXII?
Despite a mammoth specification, we found there is little standardisation in the way TAXII client implementations work. For example, some clients will poll for updates every minute, some every hour.
Please email us at otx-support@alienvault.com if our implementation isn't working for your client, or if you have any questions or suggestions.
Testing / exploration
To get an idea of how TAXII works with OTX, you can try it out using any number of available TAXII clients. Here are some examples using a client called cabby. Cabby can be downloaded and installed, or if you have a working Docker installed, you can run it via a Docker container. If you're using Docker, your command line will look something like:
if you're running from a locally installed cabby instance, the same command would just be:
Discovery
taxii-discovery is a cabby program that will call the taxii discovery endpoint, which tells you what services are available and some of the options they support.
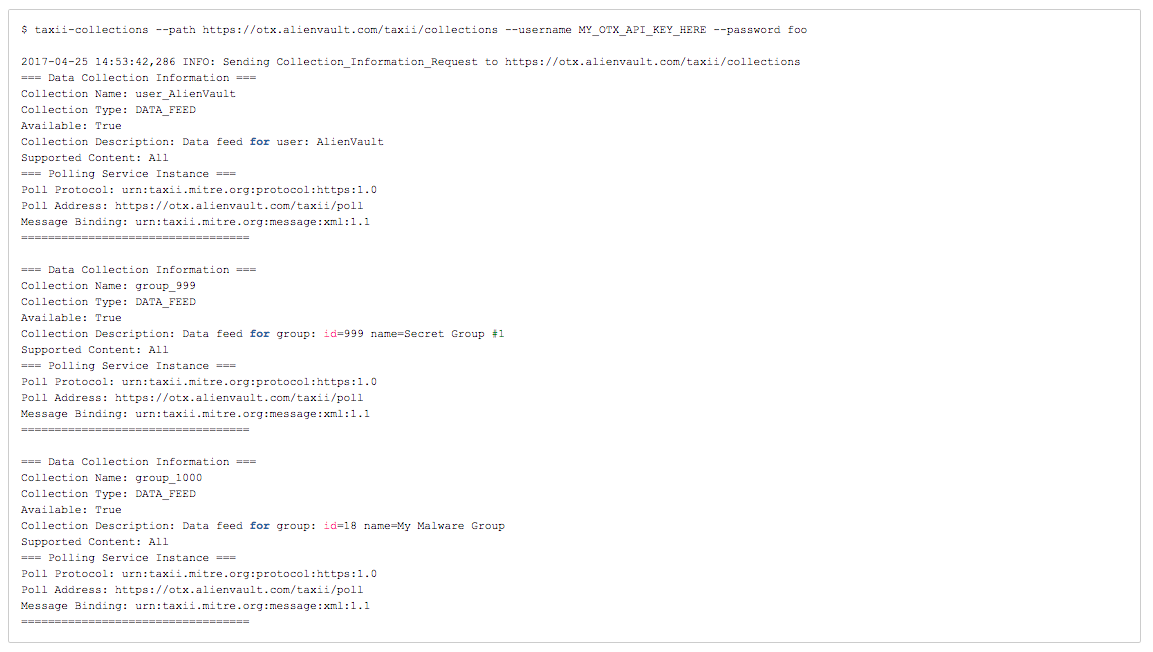
Collections
taxii-collections is a cabby program that will list the collections that are available to you. Note that available collections will vary by user, depending on collections you have access to. If you do not pass a username, then you will see only public collections. To see your personal additional collection, pass your OTX API key as the "username", with anything or nothing as the password.
Polling
taxii-poll is a cabby program that will poll a collection and return all matching results. This command can be helpful to make sure that the collection feed is working, but because it dumps all the output in a raw for, the output won't be included here. This example will fetch the first page of results from the AlienVault user's feed, starting at April 15th, 2017 at midnight UTC.
Conclusion
OTX has been around a while as a source of great threat intelligence. With this new capability, you can use the group functionality of OTX to store threat intelligence and privately share it with people you specify. You can then deliver this by STIX/TAXII to your devices, or if you are a service provider, to your customers.