Security operations center
Build a smarter security operations center (SOC) for your cloud, hybrid cloud, and on-premises critical infrastructure.
Overview
Build a smarter SOC with AT&T Unified Security Management
The purpose of a security operations center (SOC) is to identify, investigate, prioritize, and resolve issues that could affect the security of an organization’s critical infrastructure and data. A well-developed and well-run SOC can perform real-time threat detection and incident response, with SOC analysts that can deliver rapid security intelligence to stakeholders and senior management, identifying when an attack starts, who is attacking, how the attack is being conducted, and what data or systems are being compromised.
For many organizations, however, “SOC Analyst” is just one of many hats worn by today's resource-constrained IT professionals. They need a solution that provides the same threat detection and incident response capabilities as a world-class security operation center, but at a fraction of the cost to deploy and manage it.
Centralize security visibility
Eliminate security blind spots by aggregating and correlating events from all your devices, servers
Accelerate incident response
Make informed decisions with contextual data about attacks and recommendations on response
Stay ahead of emerging and evolving threats
Stay up to date with continuously updated threat intelligence from AT&T Alien Labs
Identify the business-critical assets in your environment
Having a deep understanding of all the assets in your cloud, on-premises, and hybrid environments is the first step in being able to respond to and contain the most serious threats. Asset discovery and inventory enables you to continually know what assets are connected to your environment and to group assets based on system type, business criticality, and more. With this you can prioritize how you respond to risks and threats, which is an essential component of an effective security operations center.
Within minutes of installing AlienVault USM, the platform will start to discover all the devices connected to your environment, what software and services are running on them, how they’re configured, any potential vulnerabilities, and any active threats being executed against them.
Active asset scanning—built into the USM platform—probes your environments for the signature of each detected asset. These ‘signatures’ provide clues that help identify the device, the OS, running services, and configuration details—all information that can be used to determine the probability of the success of an attack.
With devices dynamically connecting and disconnecting from your environment—especially in elastic cloud environments—it’s important to continuously scan for assets. With the USM platform, you can readily schedule asset scans and asset group scans to run on a per-minute, hourly, or daily basis.
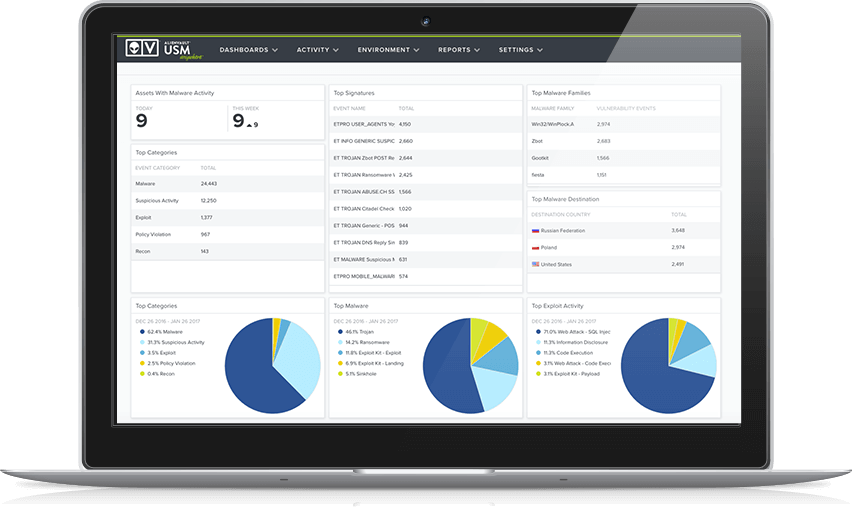
Find the vulnerabilities in your environment before attackers do
Being able to pinpoint “holes” or vulnerabilities in your IT environment gives you a deeper understanding of how your organization may be exploited during a breach.
A security operations center needs to run internal vulnerability assessment on a regular and on-going basis to ensure new vulnerabilities are discovered and responded to in a timely manner.
AlienVault USM provides the following approaches to automate vulnerability assessment:
Active network scanning
AlienVault USM actively probes the network to elicit responses from hosts. This allows AlienVault USM to determine the configuration of the remote system and cross-reference with a database of known vulnerabilities.
Host-based assessment
Using authenticated scans, AlienVault USM’s analysis engine can perform a more detailed and accurate detection of vulnerabilities by inspecting installed software and services, and comparing with a list of known vulnerable software packages.
Regularly scheduled vulnerability scans
The USM platform allows you to schedule vulnerability scans that run at desired times, whether every hour, every day during your off-peak hours, or at whatever schedule meets your security policy. Automated scanning ensures continuous visibility of your vulnerabilities as your IT landscape changes.
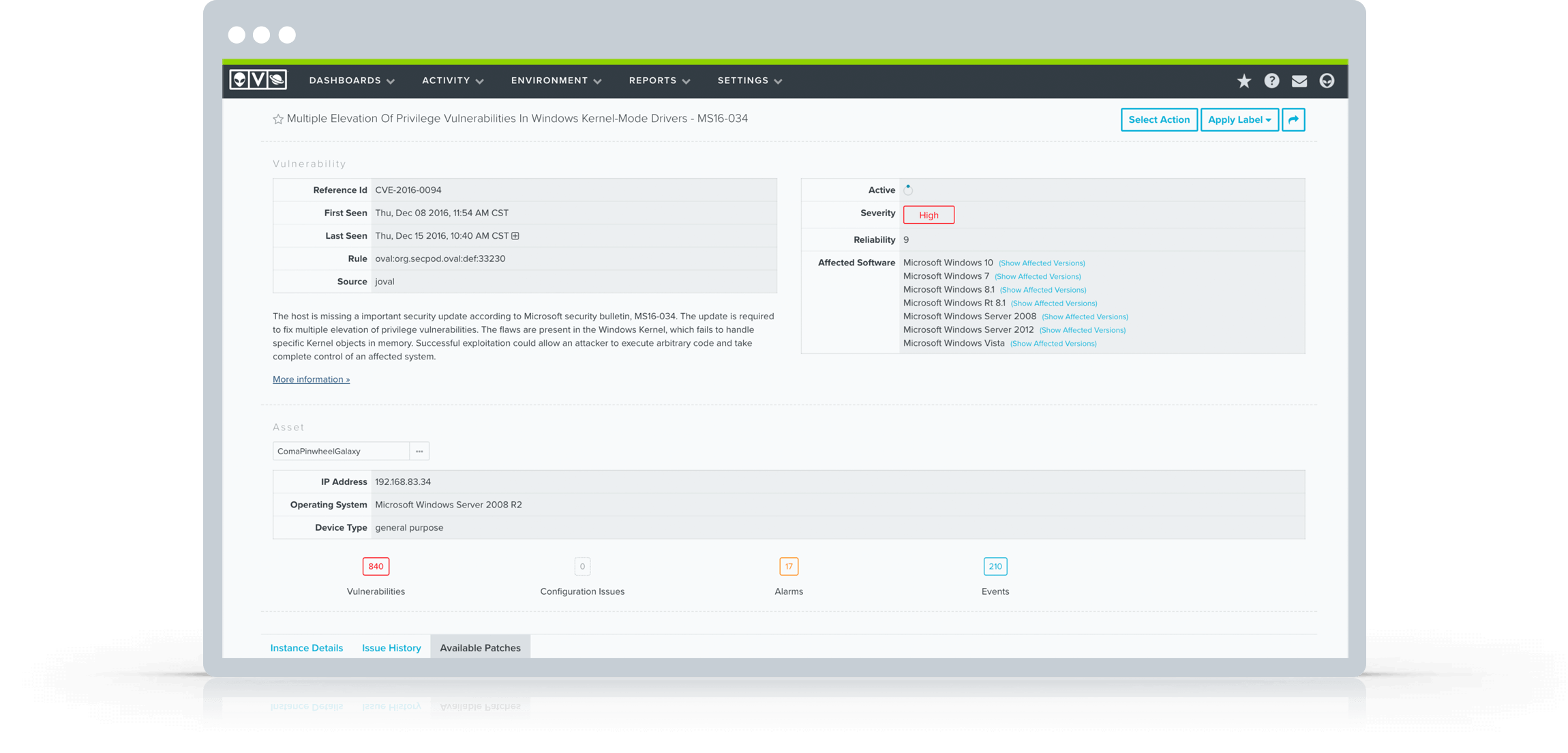
Prioritized vulnerabilities
Every vulnerability detected in AlienVault USM is assigned a score that identifies its level of severity. Using this score, the vulnerabilities are prioritized as high, medium, and low severity, so you can prioritize which vulnerabilities to respond to first.
Use multi-layered threat detection technologies to identify attacks
AlienVault USM enables you to perform multi-layered intrusion detection in the cloud and in your data center. It leverages Open Threat Exchange (OTX) threat intelligence, verified by the AlienVault Labs Security Research Team, to identify the latest tools, techniques. and attack methods used in the wild, so you stay one step ahead.
Network Intrusion Detection System (NIDS)
The Network Intrusion Detection System (NIDS) capability of the USM platform scans your network traffic, looking for the signatures of the latest attacks and other exposures. Alarms are raised in your AlienVault USM dashboard to alert you when threats are identified.
Host Intrusion Detection System (HIDS), including File Integrity Monitoring (FIM)
The Host-based Intrusion Detection System (HIDS) capability of AlienVault USM employs an agent on each host to capture and monitor key events across the operating system and installed applications. Its File Integrity Monitoring (FIM) capabilities track access to and activity on files, including any changes to configuration files, system and applications binaries, registry settings, and content files.
Intrusion detection in the cloud
AlienVault® USM Anywhere™ delivers native cloud intrusion detection capabilities in AWS and Azure cloud environments. In USM Anywhere, purpose-built cloud sensors leverage the management APIs in AWS and Azure, giving you full visibility into every operation that happens in your cloud accounts.
Threat intelligence
AlienVault USM receives threat intelligence updates continuously from the AlienVault Labs Security Research Team. The team acts as an extension to your IT team, and constantly performs advanced research on current threats to develop updates to AlienVault USM’s threat intelligence subscription in the form of SIEM correlation rules, IDS signatures, response guidance, and more.

Know which threats to focus on right now
When a variety of security technologies are deployed at scale, a security operations center can quickly become overwhelmed with a vast amount of data to analyze. This leads to questions like: What should be done first? What data needs further analysis? Where is my time best spent?
Evaluating each stream of data independently can be a poor use of your time. Instead, all data streams need to be considered as a whole with each adding further context to the other.
AlienVault USM automates and simplifies the process of collating and correlating the vast amounts of data with its built-in Security Information and Event Management (SIEM) event correlation and log management capabilities.
The USM platform aggregates data from across all the devices, servers, and applications from across your on-premises, cloud, and hybrid environments. Its SIEM event correlation capabilities normalize and analyze all collected data, correlating events to identify threats and generate alarms within the USM platform.
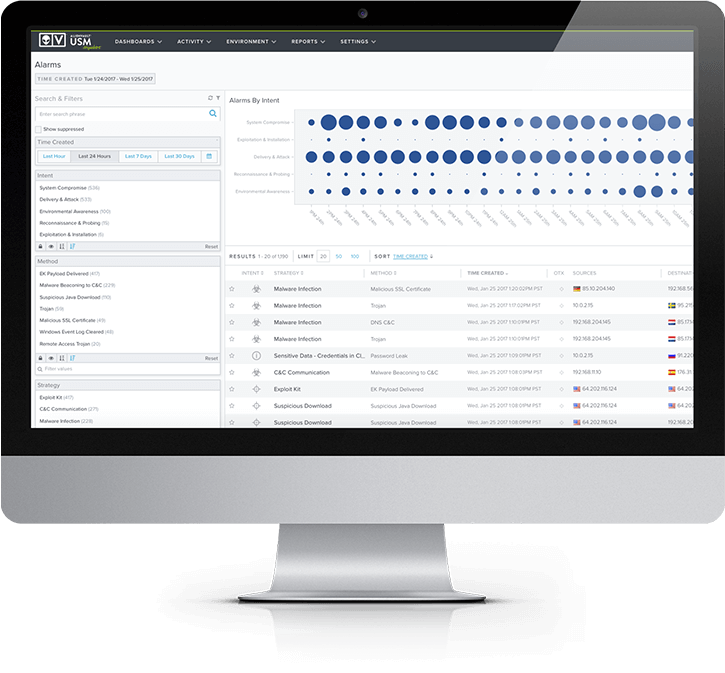
AlienVault USM categorizes alarms into one of the following Kill Chain Taxonomy categories, helping prioritize your response.
- System compromise – Behavior indicating a compromised system. This is the most severe threat level.
- Exploitation & installation – Behavior indicating a successful exploit of a vulnerability or backdoor/RAT being installed on a system.
- Delivery & attack – Behavior indicating an attempted delivery of an exploit.
- Reconnaissance & probing – Behavior indicating a bad actor attempting to discover information about your network.
- Environmental awareness – Behavior indicating policy violations, vulnerable software, or suspicious communications.