AT&T Cybersecurity is pleased to announce a code-free way for our USM Anywhere customers to make their own API-driven log collectors and custom parsers. This big advancement in threat detection and response technology will make it possible for customers to collect information from a much larger variety of sources and SaaS services without having to request new integrations or log parsers.
The foundation of threat detection is visibility; this means visibility into internal network activity, user logins and behaviors, and cloud application access to name just a few examples. And visibility is data. But getting all this information from the cloud, on premises, and user endpoints has always been a challenge. Business transformation has completely changed where our data lives and how we need to collect it.
Two big trends have emerged: businesses are flocking to SaaS services of every description, and the internet of things has massively expanded the number and type of devices we want to collect data from—think security cameras, meeting room equipment, even building control systems and thermostats. These trends have conspired to make it very difficult for security vendors to keep up with the demand for data collection tools. Custom applications need to be written to talk to cloud APIs, and even if old-school syslog is used by legacy building control systems, parsers are required to normalize and enrich the data before it can be used to find threats.
AT&T is proud to announce Custom AlienApps and Custom Log Parsers
The Custom AlienApps feature empowers customers to create their own REST API applications for collecting data from any cloud service with an API for collecting events. To do this, customers do not need to understand how to code in any scripting languages, nor do they need any special skills. All they will need to do is complete a simple configuration dialogue and provide some relevant information, which includes authentication type, location of the log endpoint.
Once the app has been successfully configured by the customer, it will reach out to the SaaS service and download the events that are waiting there. However, as you may know, not all log event data is the same. There is no standard way to perform logging, nor is there one convention for how to format logs or name the keys used in logs. Logs are essentially key value pairs, and the USM platform must normalize these pairs in order for detection to work. For example, network logs usually have a field for the source IP address of the event the log refers to. Sometimes vendors use sourceip=, and sometimes they use source_ip=, source-ip=, etc.
Figure 1: App mapping
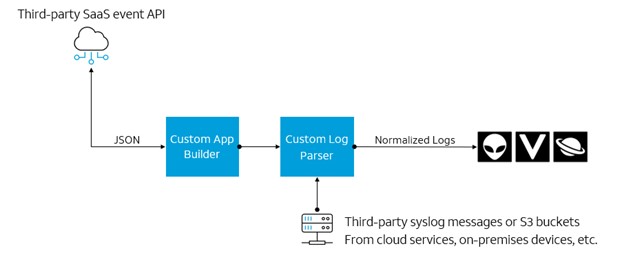
Normalizing the logs is the job of a parser. With the new Custom Log Parser feature, customers can build their own parser by dragging and dropping fields instead of waiting for an engineer to build one for them. (See figure 1.) Note that this step should be performed carefully because all data correlation will depend on it. This new feature allows customers to create parsers not only for their custom AlienApps, but also for any “Generic Log” imported via syslog or an S3 bucket. See figure 2 for a graphical view of this.
Figure 2: Custom Log Parsers – graphical view
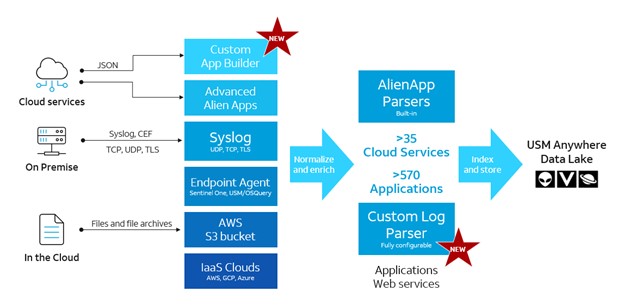
These innovations join a host of others in the AlienApps log ingestion framework. (See figure 3.) Our log processing architecture is built to accommodate as many methods as possible, and we continue to evolve and add others. In addition to making their own AlienApps and parsers, customers can ingest logs via our roster of 36 Advanced AlienApps for various cloud services. And these apps also allow customers to respond to alarms by using the containment capabilities of the various security products in their network, such as endpoint self-isolation or adding a firewall.
Figure 3: AlienApp log processing architecture
The USM platform also supports traditional syslog, in standard format and CEF. We currently have more than 570 parsers for different products. Additionally, the platform will process logs that are sent to an Amazon S3 bucket and grab logs from the customer’s IaaS services. We recently added sensorless log collection for AWS with our Cloud Connector feature, and we collect endpoint logs using our agent or the SentinelOne EDR agent.
If you’d like to learn more about Custom AlienApps and Custom Log Parsers, you can find full documentation in the USM Anywhere Help section. If you’re interested in trying out these features and are not already a customer, we invite you to sign up for a free trial.