
I recently interviewed Russ Spitler, VP of Product Strategy at AlienVault, on the hot topic of threat intelligence.
Question: First, how do you define “threat intelligence”?
It’s information about malicious actors, their tools, infrastructure and methods. There are a lot more detailed definitions but my simple definition covers the core concept.
Question: How does threat intelligence work?
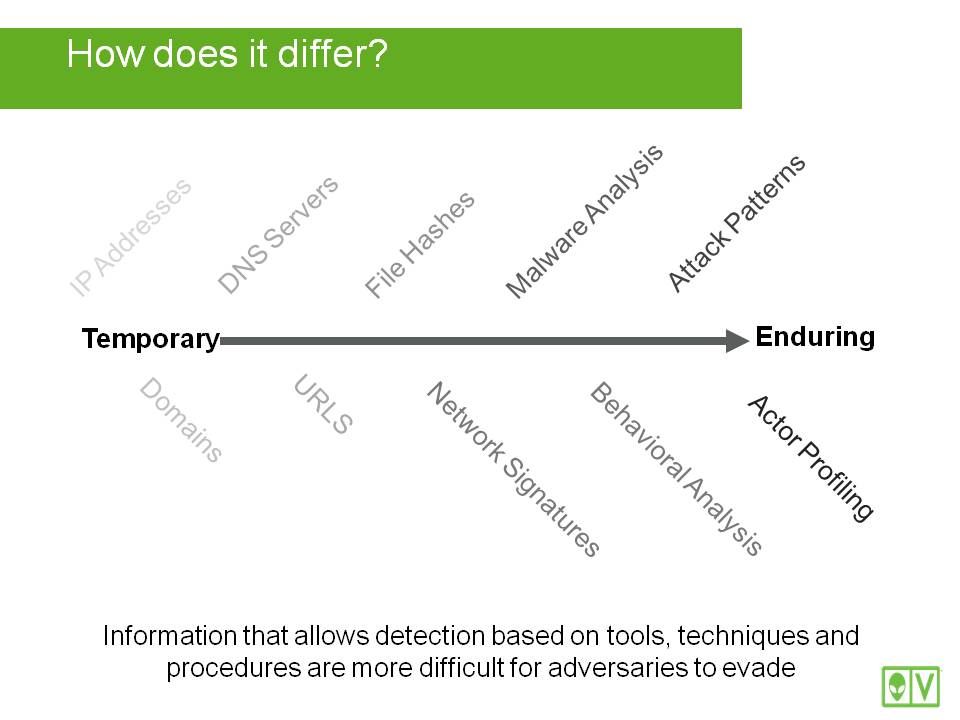
Threat intelligence works by applying information known about malicious actors (or their tools, infrastructure or methods) to observed activity in your environment. This may involve looking at many aspects of malicious activity and applying your threat intelligence in a number of ways. What makes this difficult is that threat intelligence comes in many forms, so applying that intelligence in context to your environment can be time-consuming and difficult. Even worse, some aspects, like IP addresses and domains (infrastructure), are ephemeral, and are easily changed by malware. However, other aspects, like the actor’s motivation or attack patterns, are tougher to change quickly and are more robust.
Question: What is threat intelligence and how is it developed?
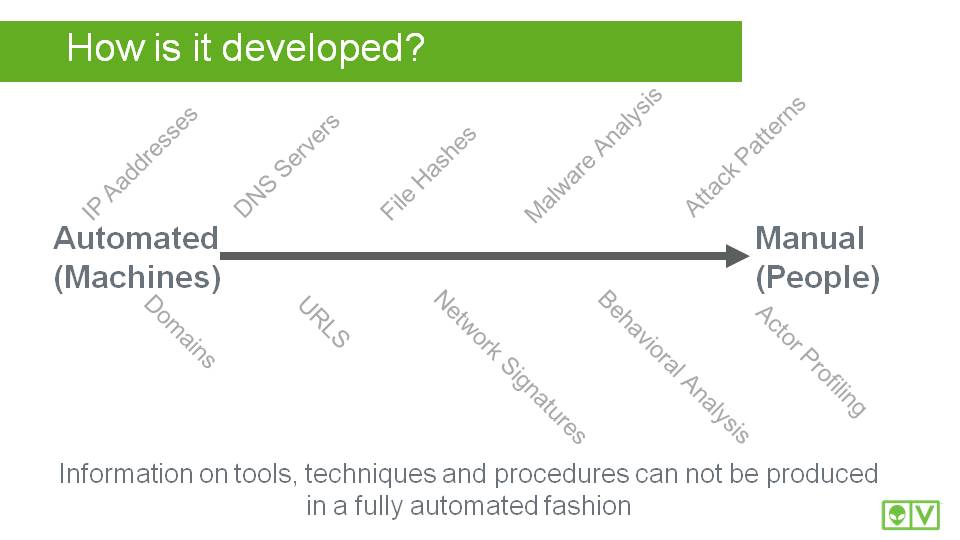
Threat Intelligence comes in many forms. As we talked about before, our goal is to describe a malicious actor's motivations, activity, infrastructure, methods, tools, etc. As these evolve so will our descriptions of them. Some of the forms that we use commonly today include IP addresses, domain names, DNS servers, URLs, file hashes, network signatures, attack patterns, and actual written profiles (like you might find in a teen magazine). Each of these forms is developed in a different way, some of which is automated and some of which involves pain-staking manual effort.
So, some of the information is processed automatically, and some requires security researchers to develop?
That’s right. On the scale, here’s how it looks:
Question: When selecting a threat intelligence vendor, how would you start?
Ignoring the hype is the most important thing. Look at the reputation of the security researchers that the vendor has – do they publish unique research? Are they referenced by other researchers? Look at the technology they employ – do their methods seem sound? Avoid over-hyped vendors who cite things like one guy who used to be in the military that is on their board of advisors. Look at their technologies and processes very closely. If they are not willing to be open about their methods, and instead rely on “secret sauce,” beware! Transparency is the key starting point, to me.
Question: We do hear a lot of hype around threat intelligence! What types of threat intelligence vendors do you see?
Vendors fall into 3 classes:
- Closed threat intelligence, like ISACs, which tend to be vertically aligned and often have steep or arduous joining requirements
- Security product vendors that have their threat intelligence tied tightly with their products, but not accessible easily outside of their products. If you have their products, this can be a great, but it also means that you can only consume the forms of threat intelligence that their products can understand
- Pure-play threat intelligence vendors that charge you a subscription to access information. These can be an option, but remember, you will still need security products and staff to analyze this information.
Question: How does OTX compare with this?
Open Threat Exchange (OTX), is a hybrid of the options above with key differences that set it apart. The most important difference is that OTX is an open community that anyone can participate in. It has an open API with available integration methods for a number of security tools and SDK’s for Python and Java. However, it also has tight integration with the AlienVault products making it possible to get the benefits of tightly integrated threat intelligence. This integration not only provides what is available to the open community but also includes additional forms and proprietary research that our Labs team has developed.
Question: How does community interaction relate to the quality of threat intelligence?
It takes a village. If we look at OTX, we’ve had over 2000 contributions since opening up the platform for social interaction in August, 2014. OTX now has more than 37,000 participants in 140 countries, who contribute over 3 million threat indicators daily. Of these, more than 10,000 members are actively collaborating in the new OTX portal, which was introduced in August 2015. We are averaging 10 new Pulses (our term for information about a threat) per day. We also get around 60K contributions per day from our USM and OSSIM products, which allow our customers to “opt in” and share the data automatically generated from our products in use. Recently we have opened up the platform even more to allow the community to directly collaborate with one another, ‘wikipedia’ style, to improve the quality of one another’s pulses.
We are proud of our growing OTX community, and grateful for the contributions of our members.
Question: Threat intelligence sounds hard for IT practitioners in midsize businesses to leverage in their environments, since they’re typically not security researchers. How would you advise an SMB to start using OTX?
OTX is, by design, a platform for sharing information about threats. OTX users get the latest information about threats. They can also research the threats and collaborate with security researchers using the platform. But even an IT generalist with limited security expertise can use OTX through manual connection or through our APIs that can feed threat information to their firewall, IDS, OSSIM or USM. Then they can forget that OTX exists and simply use the information it supplies to assist them.
Question: How would that work?
OTX provides an API and SDK from the dashboard. They can use our pre-built application connector to integrate into Suricata, Bro, TAXII, or of course OSSIM or USM. Alternatively, they can also export the information manually, using STYX, MAECE or CSV.
Question: How does AlienVault use OTX to enhance its USM product?
AlienVault Labs uses threat intelligence from OTX with their analytical systems to identify emerging threats to generate new IDS signatures, correlation rules and vulnerabilities to alarm in USM. These updates occur on an ongoing basis, keeping USM able to detect even the newest malware.
Question: Could malicious actors use OTX to corrupt threat information?
They could try, but the system is based on an opt-in model. It is similar to Twitter: researchers subscribe to other users just as a Twitter user would Follow people of interest. The platform is transparent to this end so users can see how many subscribers everyone has. In addition, you can promote pulses that users have published to provide visibility into the community judgement of the contributor. People providing bad intel would be rewarded poorly in such a system.
Question: Is there any external validation of OTX? How can I learn more?
The rate of growth of OTX users is a great indicator. We are also getting validation by security researchers. Several of our competitors in the SIEM space are actively using OTX as a source of threat intelligence. Check out our full list of our OTX partners. Below is a slide which was part of a talk at CTI Summit by security researcher Alex Pinto.
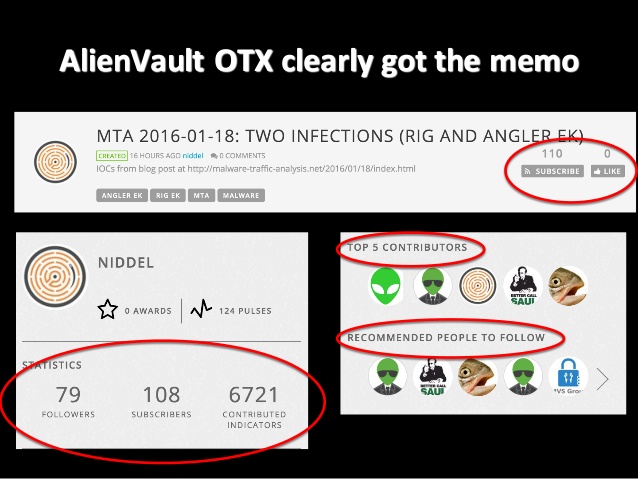
Thanks for the #CTISummit audience. Follow @kylemaxwell on the #ddti hashtag for live tweets. Slides here: https://t.co/sjP12RKHLY
— Alex Pinto (@alexcpsec) February 3, 2016
That’s exciting! Where is OTX going from here?
Glad you asked. Our newest release, which was announced today includes the ability to collaborate with other users to improve the quality of the pulses in the system. If you see something that could be improved or have some more intel about a threat, you can easily contribute it to an existing pulse improving it for all!
Check out this webcast or visit our website to learn more about threat intelligence and OTX.

