Security operations center (SOC) tools
Sometimes security pros use the term “defense-in-depth” to describe how best to secure the critical data and systems that need to be protected against cyber threats.
 Think of this concept as a jawbreaker.
Think of this concept as a jawbreaker.
The idea is pretty simple. Starting with the data you’re protecting at the center, you add layer upon layer of policy enforcement in order to make it difficult for an attacker to break through each layer to access that data.
In fact, the cyber security industry grew out of this layered model. Each vendor started to specialize in each of these ‘layers,’ expecting the customer to piece these disparate tools together for the full context needed for security monitoring. For large organizations like banks or governmental agencies with large cyber security budgets and highly skilled teams, this approach has worked for—more or less.
Prevention vs. Detection
The key point to emphasize here is the importance of detection (vs. prevention). Of course organizations need to implement preventative tools (e.g. firewalls, AV, etc.) along with ensuring that vulnerabilities are patched among other prevention-type activities (e.g. secure desktop configurations, strict password policies, secure account management, etc.).
But in the last few years, detection has quickly risen in importance. Attackers have evolved their capabilities—consider the rise in cybercrime attacks like ransomware and DDoS threats—to the point where they execute these attacks without being noticed. In a recent Verizon Data Breach Investigation report, they concluded that it was far more common for victims to learn that they’d been breached from a third party vs. discovering these breaches themselves.
Smaller organizations, with limited budgets and time, need a new approach—one that combines the essential tools for building a SOC into a workflow that can be easily supported by small teams. These essential SOC capabilities include asset discovery, vulnerability assessment, behavioral monitoring, intrusion detection, and SIEM (security information and event management).
In this chapter, we’ll review the details of these SOC tools. We’ll show you how AlienVault® Unified Security Management® (USM) combines these essential capabilities for building a SOC into a single platform. Finally, we’ll cover how AlienVault Labs Threat Intelligence and AlienVault Open Threat Exchange® (OTX™) power these essential capabilities within AlienVault USM.
Key Takeaways
Review the essential security monitoring tools you’ll need to build a SOC: Asset Discovery, Vulnerability Assessment, Intrusion Detection, Behavioral Monitoring and SIEM / Security Analytics. Achieve SOC success with limited time and resources by utilizing a single platform like AlienVault Unified Security Management (USM) that consolidates these tools into one place.

1 Asset Discovery
 FEATURE SPOTLIGHT: Asset Detail
FEATURE SPOTLIGHT: Asset Detail
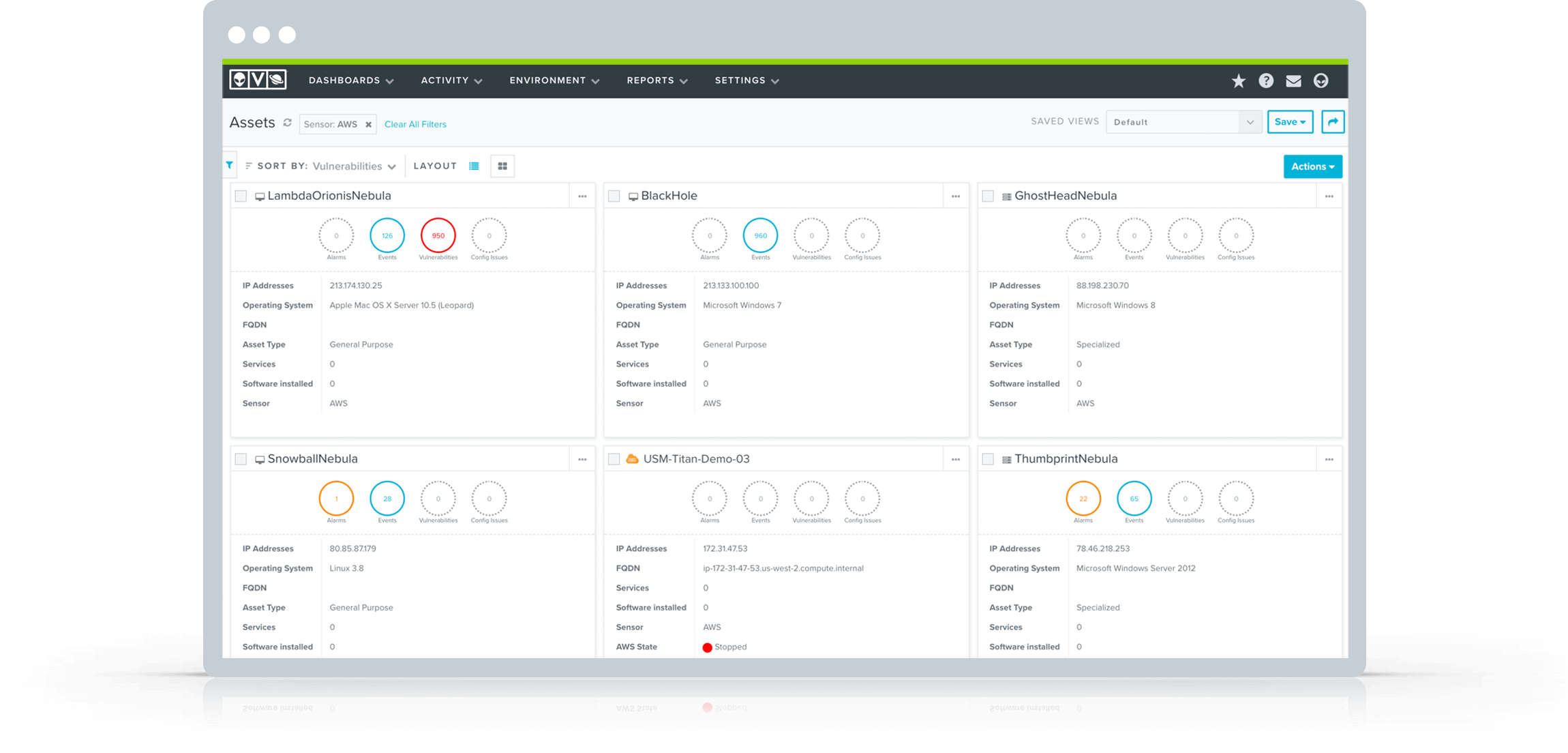
The asset discovery & inventory capabilities within AlienVault USM are explicitly designed for SOC analysts. No other asset inventory tool provides this level of context, in a format that streamlines SOC analyst workflows.
The key is that all of the security-relevant information about an asset is displayed in a single view. By clicking into asset details, you can review all of the vulnerabilities, alarms, and events that are associated with a specific asset.
2 Vulnerability Assessment
A Closer Look: Vulnerability Assessment in AlienVault USM

Regularly Scheduled Auto-scanning
Create scans that run daily, weekly, or monthly during your off-peak hours. Automated scanning ensures continuous visibility of your vulnerabilities as your IT landscape changes.
Authenticated Scanning
Authenticated scans perform vulnerability assessment by using host credentials to probe your assets deeply, looking for vulnerable software packages, local processes, and services running on the system.
Cloud Infrastructure Scanning
AlienVault USM uses purpose-built cloud sensors to interface directly with cloud providers to automatically perform network vulnerability assessments of your AWS and Azure environments, including assets, security groups, and configurations.
 FEATURE SPOTLIGHT:
FEATURE SPOTLIGHT:
Vulnerability Scan Scheduler
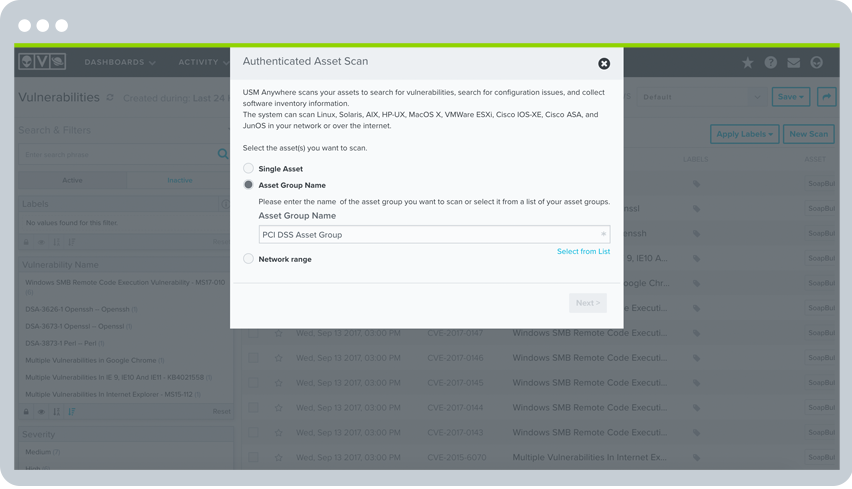
Flexibility is one of the most important aspects of doing vulnerability assessment well. At peak hours, vulnerability scans can disrupt network and system performance. To address this challenge, AlienVault USM offers SOC analysts control and flexibility when setting up ad-hoc and scheduled vulnerability scans.
With AlienVault USM, you can:
• Easily set up scan jobs targeting individual assets, asset groups, or even entire networks
• Schedule scans to run automatically at regular intervals to take the guesswork out of managing a scanning routine
• Control the techniques utilized and level of scanning intensity using default profiles or by creating your own
3 Behavioral Monitoring
4 Intrusion Detection
 FEATURE SPOTLIGHT:
FEATURE SPOTLIGHT:
AlienVault USM Integration with AlienVault Labs Threat Intelligence
Before explaining how this integration works, it’s important to understand how the AlienVault Labs Security Research Team develops its threat intelligence updates. Through a combination of proprietary research, collaboration with other security research institutions, and insights from the community-driven threat data within the AlienVault Open Threat Exchange (OTX), AlienVault collects tens of millions of threat indicators every day, including malicious IP addresses and URLs, domain names, malware samples, and suspicious files. AlienVault aggregates data from a wide range of sources, including:
- External threat vendors (such as McAfee, Emerging Threats, Virus Total)
- Open sources (including the SANS Internet Storm Center, the Malware Domain List, as well as from collaboration with state agencies and academia)
- AlienVault USM and AlienVault OSSIM users voluntarily contributing anonymized data
- Community-contributed threat data in the form of OTX “pulses” (the format for the OTX community to share information about threats)
- High-interaction honeypots that we set up to capture the latest attacker techniques and tools. We scale up instances of the honeypots depending on activity.
Next, we have set up automated systems and processes which leverage machine learning to assess the validity and severity of each of these threat indicators collected in OTX, including:
- A contribution system (for malware)
- A URL system (for suspicious URLs)
- An IP reputation system (for suspicious IP addresses)

We then use threat evaluation tools created by the Security Research Team to test and validate specific threat indicators. These evaluation processes include a Malware Analyzer, a DNS Analyzer, a Web Analyzer, and a BotNet Monitor. The validated threat data are also shared with the OTX community via the OTX Portal.
The Security Research Team then conducts deeper qualitative and quantitative analysis on the threats. Examples include reverse-engineering a malware sample, or conducting extensive research on particular threat actors and their infrastructure, to detect patterns of behavior and methods.
The Security Research Team delivers all information about the threats and the attack infrastructure to the USM platform via the AlienVault Labs Threat Intelligence Subscription. The team regularly updates eight coordinated rulesets, including correlation directives, IDS signatures & response templates, which eliminates the need for organizations to tune their systems on their own. The analyzed threat data is also fed back into the Security Research Team’s analytical systems and tools, enabling them to make future correlations of threat indicators.
5 SIEM
SIEM Secret Sauce: Threat Intelligence
Even though we have a whole chapter dedicated to Threat Intelligence, we still feel compelled to emphasize how essential dynamic threat intelligence is to the value of your SIEM, and the overall functioning of your SOC. Without threat intelligence, your SIEM would have no alarms, and no interesting reports to review. While it would be nice to have no alarms to respond to (because that means nothing is wrong or you’re on vacation), it basically means that there’s no correlation or analysis being done on your raw event log data. Or, you may have some sample or DIY correlation rules as a starting point, but you’re no longer looking for the latest threats because your threat intelligence hasn’t been updated since the LoveBug virus.
The point is…threats are constantly evolving, cyber attackers are constantly upping their game, and so too must your SOC. As new indicators and countermeasures are being discovered, collected, shared, analyzed and implemented, the more difficult we will all make it for the bad guys. That’s why AlienVault built the platform (AlienVault USM), the community (OTX), and the threat intelligence (AlienVault Labs Security Research Team) to create a SOC for all teams to implement—no matter the size.
We perform the analysis, allowing you to spend your scarce time mitigating the threats rather than researching them.
 FEATURE SPOTLIGHT:
FEATURE SPOTLIGHT:
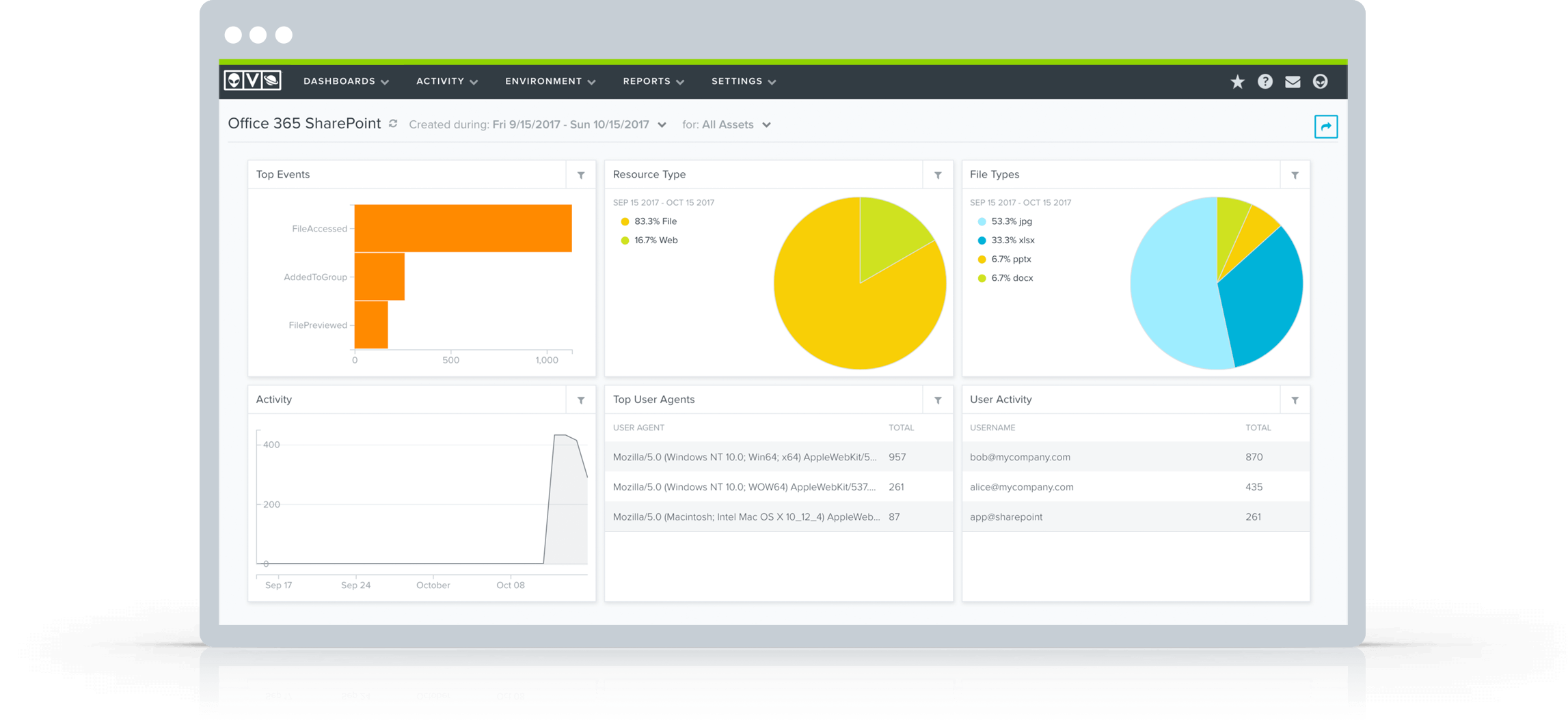
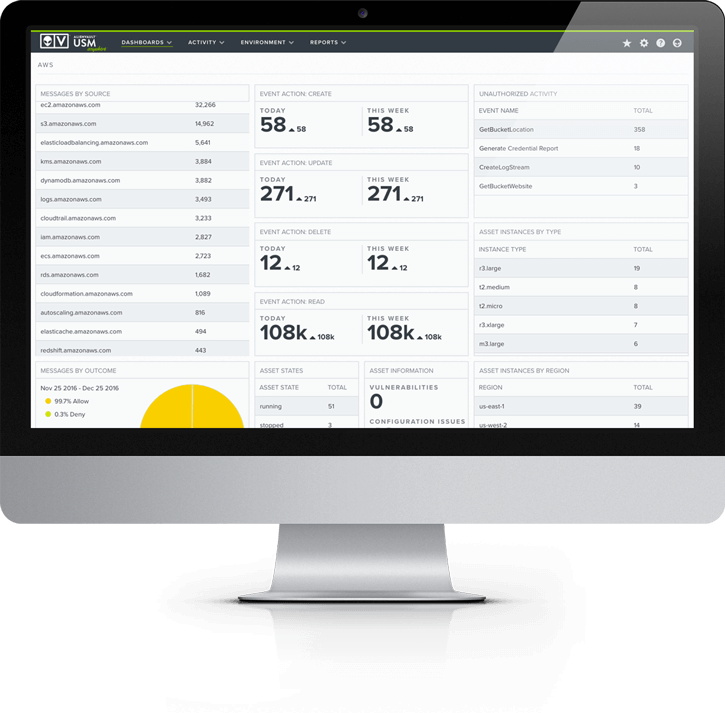
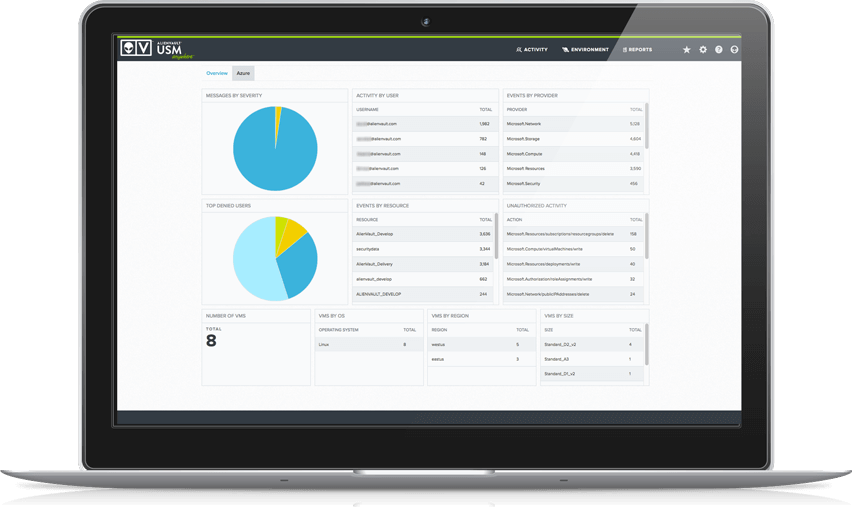
AlienVault USM Security Dashboards & Reports
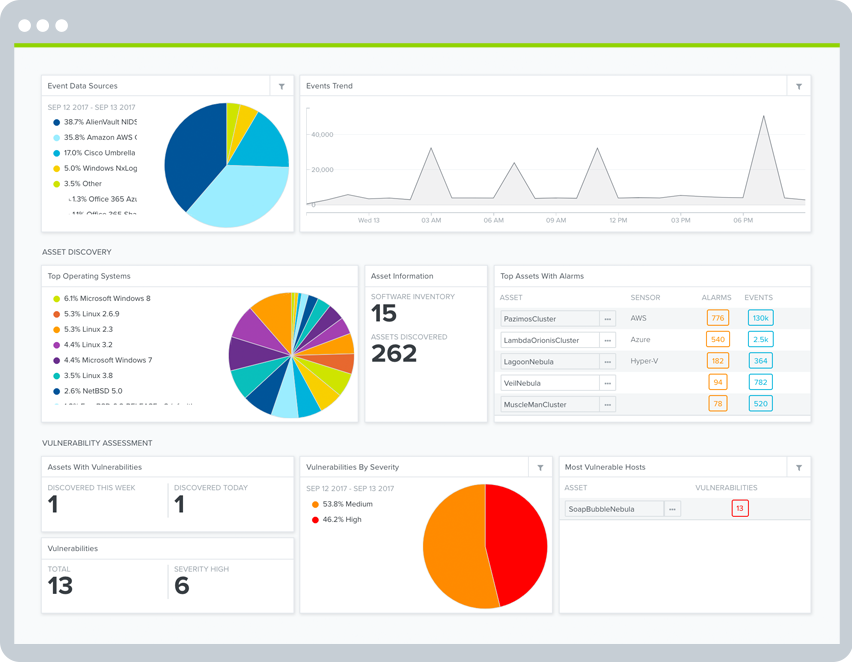
If you can’t measure it, you can’t manage it. That’s a favorite quote of millions of business people across industries and regions. It’s especially true now that we find ourselves in the age of big data. As many IT professionals have discovered, however, big data is meaningless without the ability to sort through and interpret it.
To help you put your security data to use, AlienVault USM includes intuitive dashboards and clean visualizations. AlienVault USM allows you to:
- Quickly assess the security status of your critical infrastructure
- Easily prioritize alarms and vulnerabilities
- Take immediate action to remediate new threats
- Fight data overwhelm with clean visualizations
Additionally, you can drill down within the dashboards AlienVault USM provides to see details about the threats and vulnerabilities affecting your critical infrastructure.